We are all familiar with the scenario: where a user calls the helpdesk to request a password reset after complaining that the computer won’t accept their current one or HR sends you an email with a list of recent hires who require new passwords to be created. Both situations can be handled utilizing the following GUI tools from Microsoft:
- Active Directory Users and Computers
- Active Directory Administrative Center
These tools, however, necessitate several steps and may not always be successful.
Normally, users can easily update their passwords using the Windows Settings menu. But what if they forget it or get their local administrator account disabled and are locked on the login screen?
Table Of Contents
-
Resetting Passwords using the GUI Method
-
Set-ADAccountPassword – Description
-
Set-ADAccountPassword – Syntax
-
Set-ADAccountPassword – Parameters
-
Resetting an AD User Password using PowerShell
-
Unlocking an Account while Resetting its Password
-
Forcing the User to Change Password at Next Logon
-
Resetting Password using Alternative Credentials
-
Verifying your Password Set Results
-
Resetting Multiple Users’ Passwords
-
Password Center by GroupID
-
Conclusion
Resetting Passwords using the GUI Method
This section discusses the following:
- Password Reset using Active Directory Users and Computers
- Password Reset using Active Directory Administration Center
- View the Delegated Permission to a User Account for Password Reset
- Limitations of the GUI Method and PowerShell
Password Reset using Active Directory Users and Computers
The dsa.msc (Active Directory Users & Computers – ADUC) snap-in is typically used by system administrators to reset user passwords in AD. To reset the password they have to locate the user account in AD, right-click it, and choose the Reset Password option. Because of this, they believe that automation is the key to streamlining Active Directory management activities, and they look for a simple method to automate the process or at the very least, make it simple.
By default, members of the following built-in groups have the ability to change passwords for other accounts, which prevents non-admin AD users from doing so.
- Domain Admins
- Account Operators groups
Any other account must be set up with the necessary credentials in the AD domain in order to enable it to reset passwords.
One of the following options can be opted to reset passwords:
- If you know the location of the user in AD whose password you want to change, navigate to it, right-click it, and choose “Reset Password”.

- If you do not know the location of the user in AD, you can simply search for the user by right-clicking
- the domain and selecting “Find”.
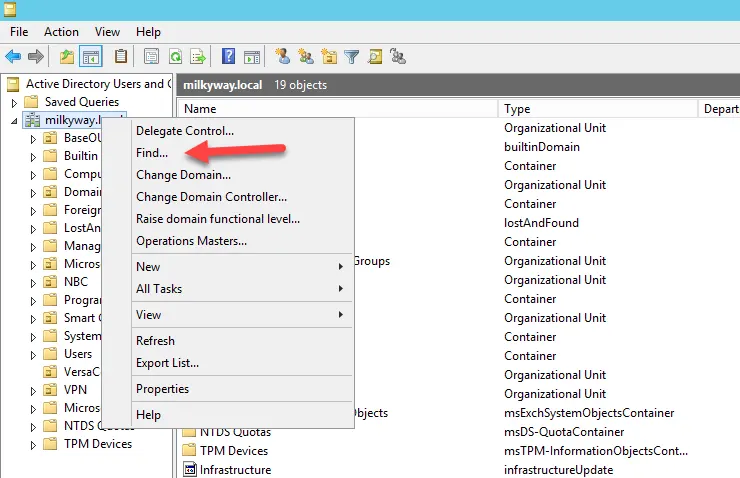 Search the user by providing the name. Then right-click it and choose Reset Password.
Search the user by providing the name. Then right-click it and choose Reset Password.
- Enter a new password and confirm it by entering it again in the given field.
- Select the User must change password at next logon check box if you want the user to create a new password for himself/herself upon next login.
- If the user account is locked by the AD security policy due to multiple login attempts with an incorrect password, you can unlock the account by selecting the Unlock the user’s account check box.
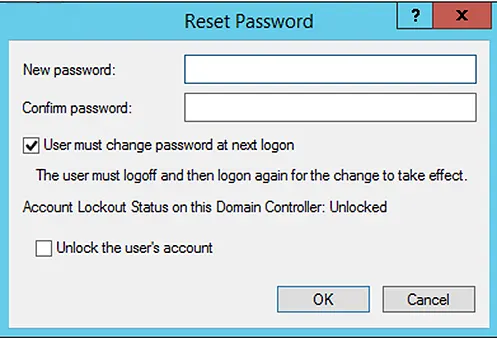
- Click OK.
Password Reset using Active Directory Administration Center
The process of resetting passwords using Active Directory Administrative Center is quite similar to the one we have used for ADUC. For this reason, I am just adding the corresponding screenshots for reference.
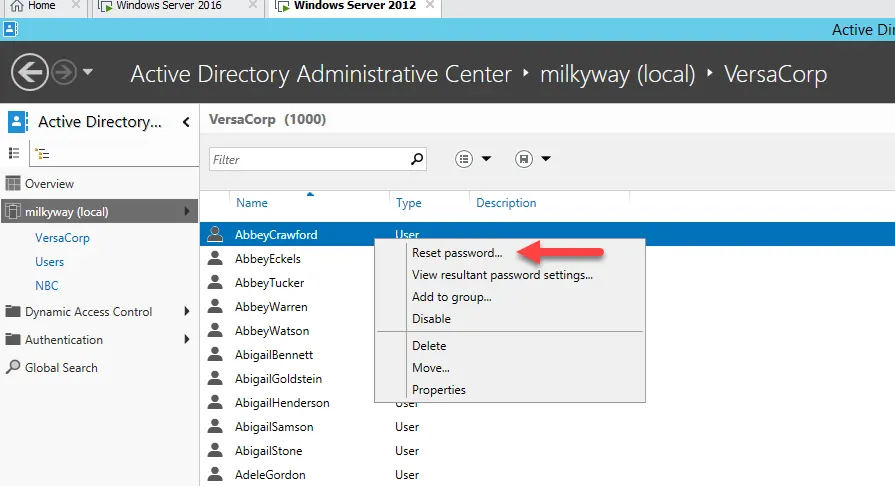
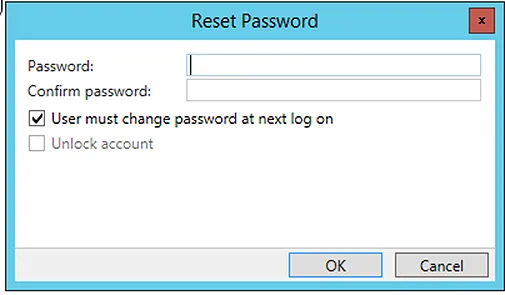
View the Delegated Permission to a User Account for Password Reset
By using Active Directory delegation, you may grant permissions to a user/group to reset user passwords in certain OUs.
To view the delegated permission to an account:
- Open the properties of the AD user for whom you want to view the permissions.
- Navigate to the Security tab and click Advanced.
- Select Effective Access, enter the name of the account and confirm that it has the Reset Password authority.

Limitations of the GUI Method and PowerShell
Resetting Active Directory (AD) user passwords using the GUI is acceptable. However, the GUI is not always a useful tool, particularly when changing the passwords for numerous users. Fortunately, the Set ADAccountPassword PowerShell cmdlet is an option.
PowerShell allows you to rapidly reset AD user passwords and even automatically create complicated random passwords. Additionally, you can develop a script that can mass-reset AD user credentials.
PowerShell makes it simple to quickly reset passwords for numerous accounts.
Set-ADAccountPassword – Description
The Set-ADAccountPassword cmdlet sets a user, computer, or service account’s password. The Identity parameter can be used to identify the required account in Active Directory. The value for the Identity parameter can be provided as:
- DN (Distinguished Name)
- GUID (Global Unique Identifier)
- SID (Security Identifier)
- SAM Account Name (Security Account Manager)
You can use the pipeline to provide an object to the Identity parameter. For instance, you could retrieve an account object using the Search-ADAccount cmdlet and then pipeline it to the Set-ADAccountPassword cmdlet. Like this, you can retrieve account objects for standalone MSAs using the Get-ADUser, Get-ADComputer, or Get-ADServiceAccount cmdlets before passing them through the pipeline to this cmdlet.
Set-ADAccountPassword – Syntax
The syntax of the Set-ADAccountPassword cmdlet is as follows:
Set-ADAccountPassword [-WhatIf] [-Confirm] [-AuthType ] [-Credential ] [-Identity] [-NewPassword ] [-OldPassword ] [-Partition ] [-PassThru] [-Reset] [-Server ] []
Set-ADAccountPassword – Parameters
The Set-ADAccountPassword cmdlet uses the following parameters:
- AuthType
- Confirm
- Credentials
- Identity
- NewPassword
- OldPassword
- Partition
- PassThru
- Reset
- Server
- WhatIf
AuthType
This parameter specifies the authentication method to be used. The following are valid values for it:
- Negotiate or 0
- Basic or 1
Negotiate is the default authentication method.
Confirm
If you want a confirmation prompt before running the command, you can use this parameter.
Credentials
If you want to run the command or script using alternate credentials, you can use the Credentials parameter by providing the user name and password of a higher privileged account.
Identity
With this parameter, you provide the Active Directory object for which the password reset operation is required. You can use the following as values:
- Distinguished Name
- GUID
- Security identifier (ObjectSid)
- SAM Account name (Security Account Manager)
NewPassword
As the name suggests, you can provide the new password as value to this parameter.
OldPassword
This parameter is used to provide the old password in case you are changing the password. If you are resetting the password, you do not need to specify this parameter.
Partition
Use this parameter to specify the Active Directory partition, other than the default partition, you are connected with.
PassThru
The cmdlet normally returns the object and doesn’t show anything in the console. You can use the -PassThru parameter in AD to display details about the user object.
Reset
This parameter is used to reset the password for an object. You must also use the NewPassword parameter when using this parameter, but you do not need to use the OldPassword parameter, as you are only resetting the password and not changing it.
Server
You can use this parameter to provide one of the following values for a corresponding domain name or directory server:
- FQDN (fully qualified domain name) of domain
- FQDN of directory server
- FQDN with the port number of the domain/directory server
One of the following services may be deployed in your environment for this cmdlet:
- Active Directory Domain Services
- Active Directory Snapshot Instance
- Active Directory Lightweight Domain Services
WhatIf
If you want to see what will happen when the command runs, use this parameter. It just shows the info on what will happen; it does not run the command.
Resetting an AD User Password using PowerShell
When you run the following command for resetting the password of a user account, you will be prompted for the new and old password for the user account you are resetting the password for. It is shown in the screenshot below:
Set-ADAccountPassword -Identity AbbeyCrawford
Set-ADAccountPassword -Identity "CN=AbbeyCrawford,OU=VersaCorp,DC=milkyway,DC=local"

You can also first store the password in a variable and then use it in the cmdlet to reset the password.
$Pwd = ConvertTo-SecureString "MyNewPassword@123" -AsPlainText -Force
Then use the following cmdlet to reset the password using the variable.
Set-ADAccountPassword -Identity AbbeyWarren -NewPassword $Pwd -Reset
The above two cmdlets will not show any output as they set the things on the go and there is nothing to show as output in the PowerShell console. You can use the following command alternatively to achieve the same results but with an output to show.
Set-ADAccountPassword abbeywarren -Reset -NewPassword (ConvertTo-SecureString -AsPlainText “NewP@ssw0rd123” -Force -Verbose) –PassThru
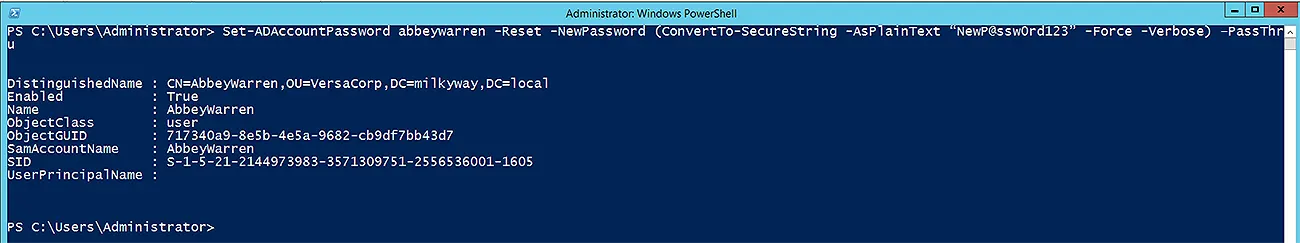
In the above screenshot, you can see some details about the user for whom you have performed the password reset operation. Notice that there are two more parameters used in the cmdlet:
- -Reset
-Reset is used when you are only resetting the account forcefully. You do not need to provide the old password for the account. - -PassThru
-PassThru is to show some output regarding the user account on which the password set or reset action is being performed.
Unlocking an Account while Resetting its Password
Sometimes a user’s account may get locked when they enter the wrong password 3 or 5 times consecutively, as laid out in the account lockout policy.


You can simply unlock their accounts while resetting their passwords by using Unlock-ADAccount with pipeline in the following cmdlet:
Set-ADAccountPassword abbeywarren -Reset –NewPassword $PWD –PassThru | Unlock-ADAccount
Forcing the User to Change Password at Next Logon
Run the following command to make a user change his or her password the next time they log into the domain.
Set-ADUser -Identity abbeywarren -ChangePasswordAtLogon $true
You can also use Set-ADAccountPassword while combining it with the password change command and the need to change the password at next logon (this is the userAccountControl object attribute).
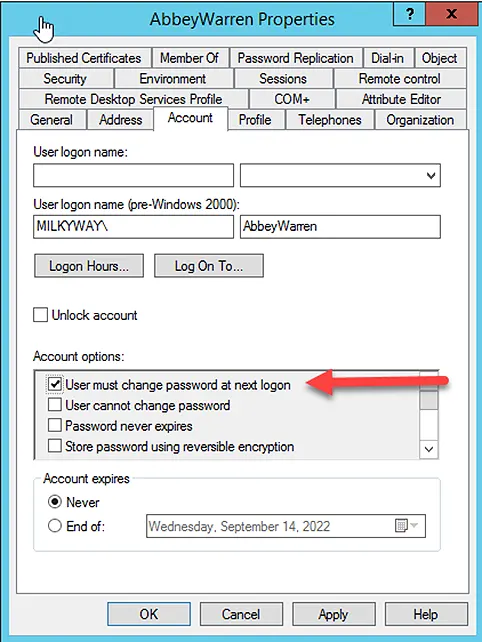
Set-ADAccountPassword abbeycrawford -NewPassword $Pwd -Reset -PassThru | Set-ADuser -ChangePasswordAtLogon $True
The above command will enable the “User must change the password at next logon” option, as shown below.
Resetting Password using Alternative Credentials
Usually administrators have two accounts (a standard user account and an admin account) to perform their tasks. If you need to run the command with your privileged account (Admin) to reset a user’s password, you can use the -Credential parameter in a variable and then use it for running the specific command. Here is how you can store the credentials in a variable.
$Credentials = Get-Credential
The command prompts you to provide the credentials to be stored, as shown below.

We will use the following variable again to store the new password for the user.
$Pwd = ConvertTo-SecureString "MyNewPassword@123" -AsPlainText -Force
Then we can use both the password and credentials variable in Set-ADAccountPassword to achieve the requirement.
Set-ADAccountPassword -Identity abbeywarren -NewPassword $Pwd -Credential $Credential
Verifying your Password Set Results
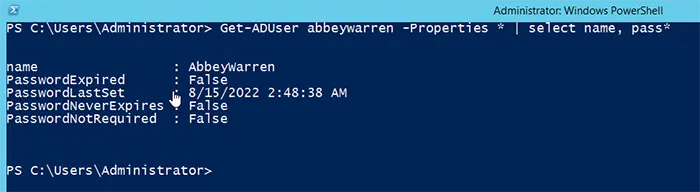
You can use the Get-ADUser command with properties to verify that the password has been successfully reset. It shows the last date and time when the password was changed.
Get-ADUser abbeywarren -Properties * | select name, pass*
Resetting Multiple Users’ Passwords
You were just shown how to use PowerShell to reset the password for a single AD user. Let’s now examine another situation where you must modify many users’ passwords simultaneously.
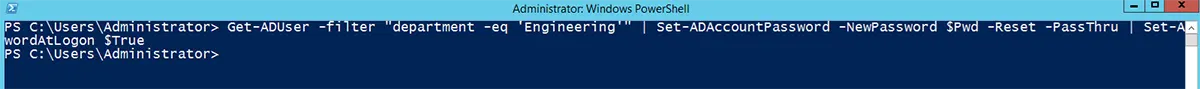
Consider a scenario when you set the same password for all users in the Engineering department and require that these users change their passwords the next time they log in. The Get-ADUser with the -Filter command can be used to choose users who have a certain value for one of the attributes. For example, users with department = Engineering.
Get-ADUser -filter "department -eq 'Engineering'" | Set-ADAccountPassword -NewPassword $Pwd -Reset -PassThru | Set-ADuser -ChangePasswordAtLogon $True
The above command will not show any output, but we will verify the output by calling the user’s password properties, as shown below.
Get-ADUser -filter "department -eq 'Engineering'" -Properties * | select name, pass*

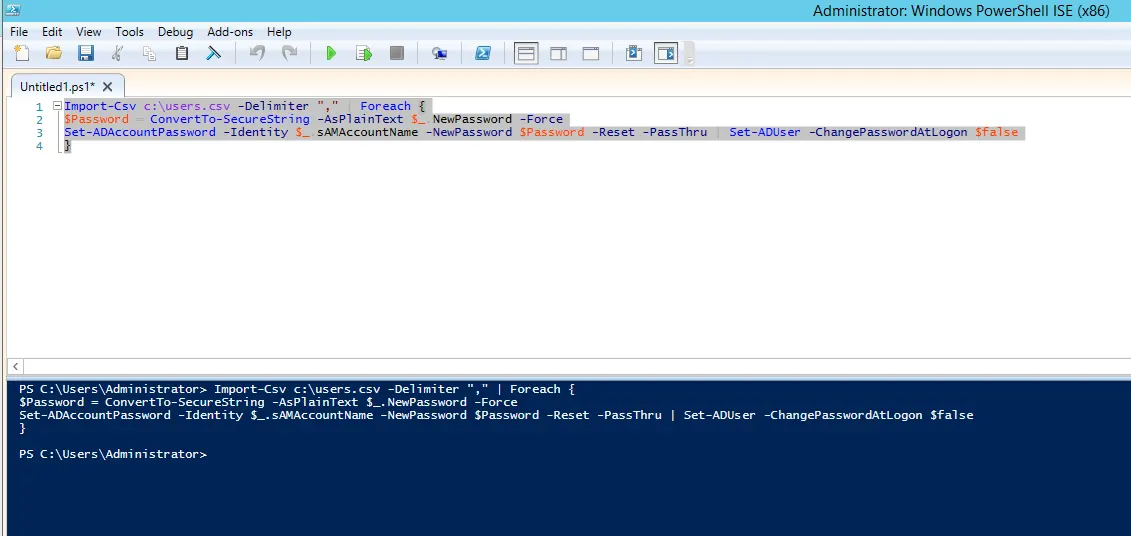
Let’s consider another illustration. Suppose you have a CSV/Excel file with a list of users who want password resets and a different password for each user. The format of the CSV file is shown below.

The following PowerShell script allows you to change the password for each user account in the supplied CSV file.
Import-Csv c:\users.csv -Delimiter "," | Foreach {
$Password = ConvertTo-SecureString -AsPlainText $_.NewPassword -Force
Set-ADAccountPassword -Identity $_.sAMAccountName -NewPassword $Password -Reset -PassThru | Set-ADUser -ChangePasswordAtLogon $false
}
Password Center by GroupID
GroupID Password Center is a password management solution by Imanami. It enables end-users to reset their domain account passwords on their own. Moreover, helpdesk can also reset passwords for users. This way, you can reduce your administrative workload.
You can set up two types of web-based Password Center portals:
- User portal
- Helpdesk portal
User Portal
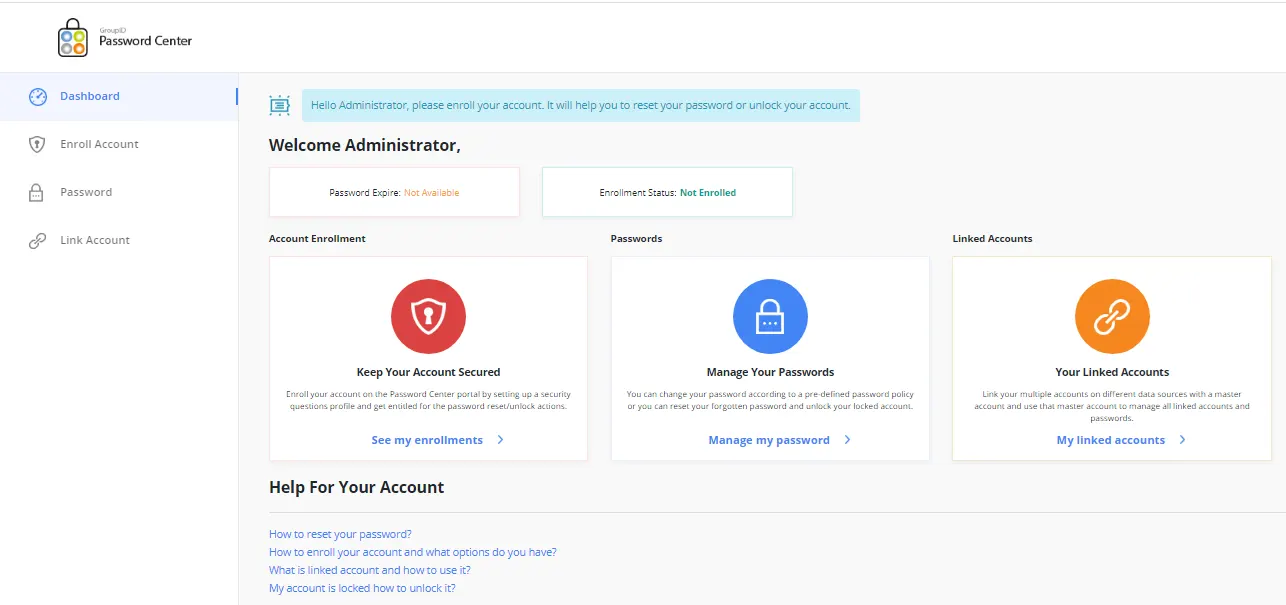
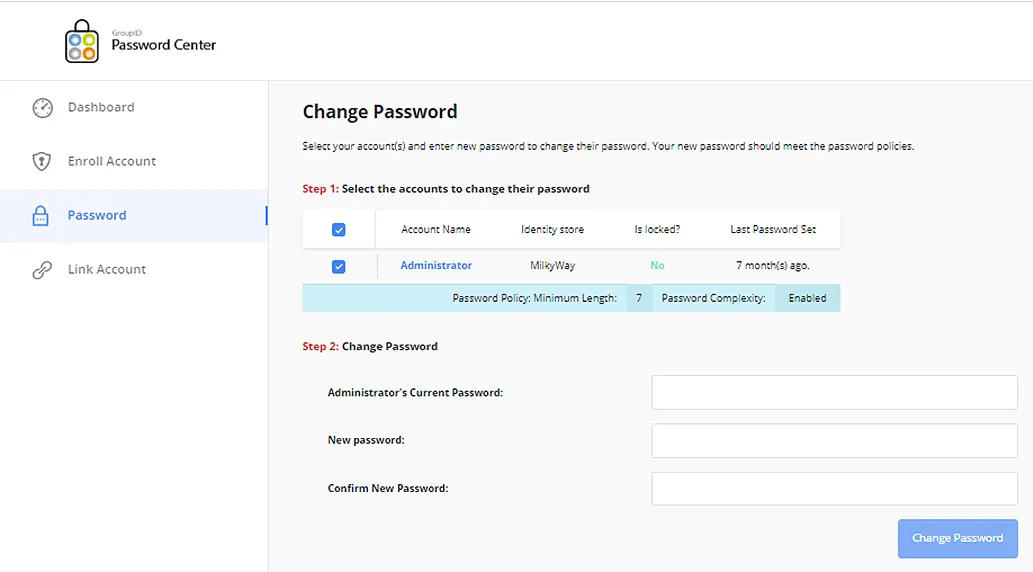
The Password Center user portal enables end-users to do the following on their own:
- Password change
- Password reset
- Account unlock
A portal can be linked to a single domain or multiple domains, which are created as identity stores in GroupID. Users of those Identity stores/domains can perform the aforementioned operations for their respective accounts after authenticating via multifactor authentication.
Helpdesk Portal
A helpdesk portal can also be linked to many domains/identity stores. Helpdesk users can perform the following operations on behalf of end-users in any of the linked identity stores:
- Password reset
- Account unlock
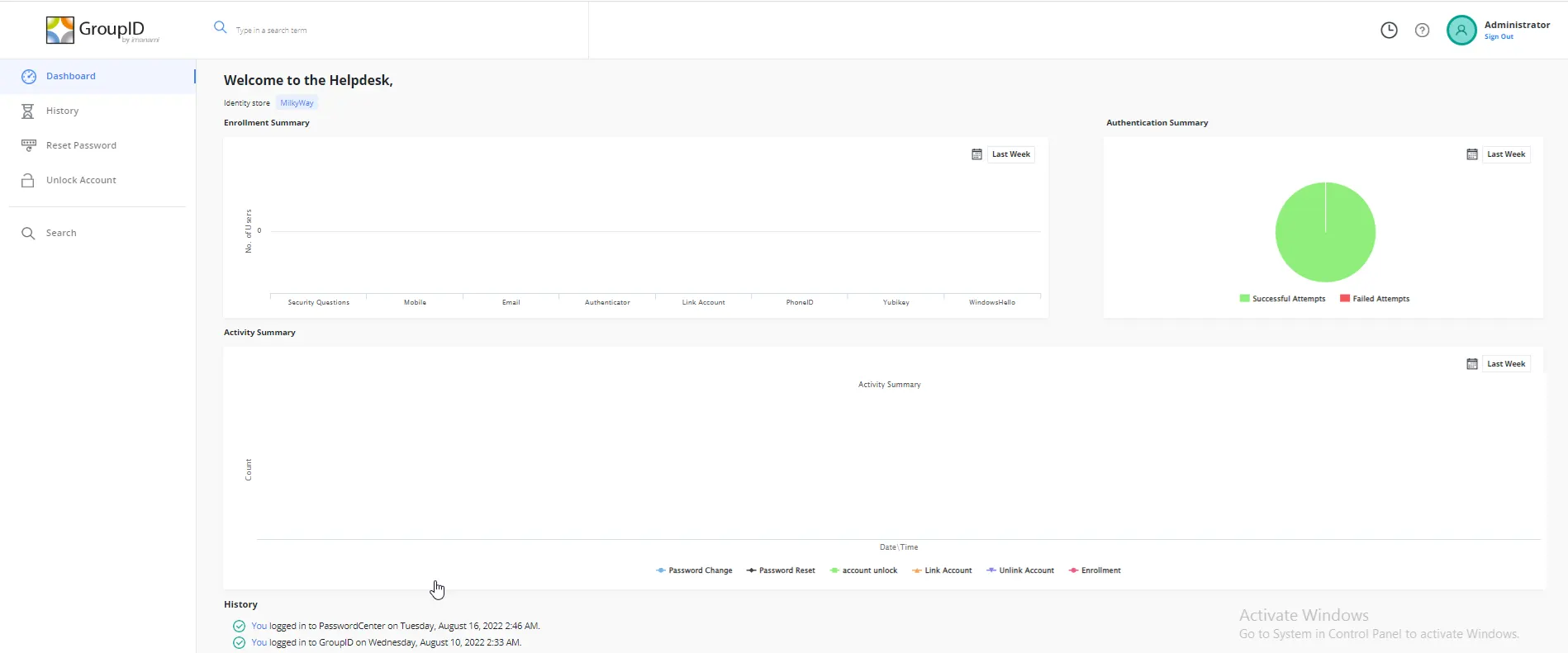
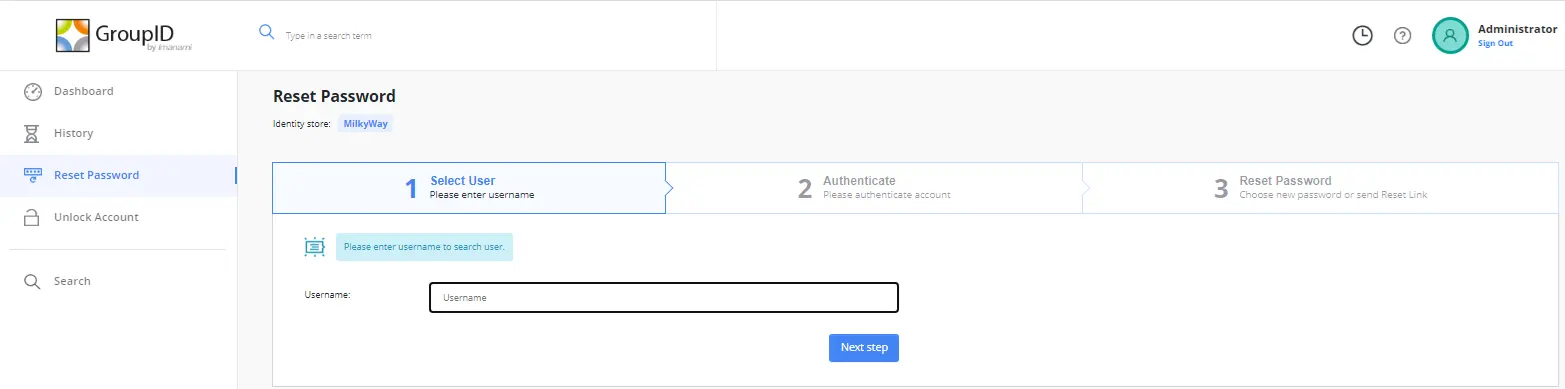
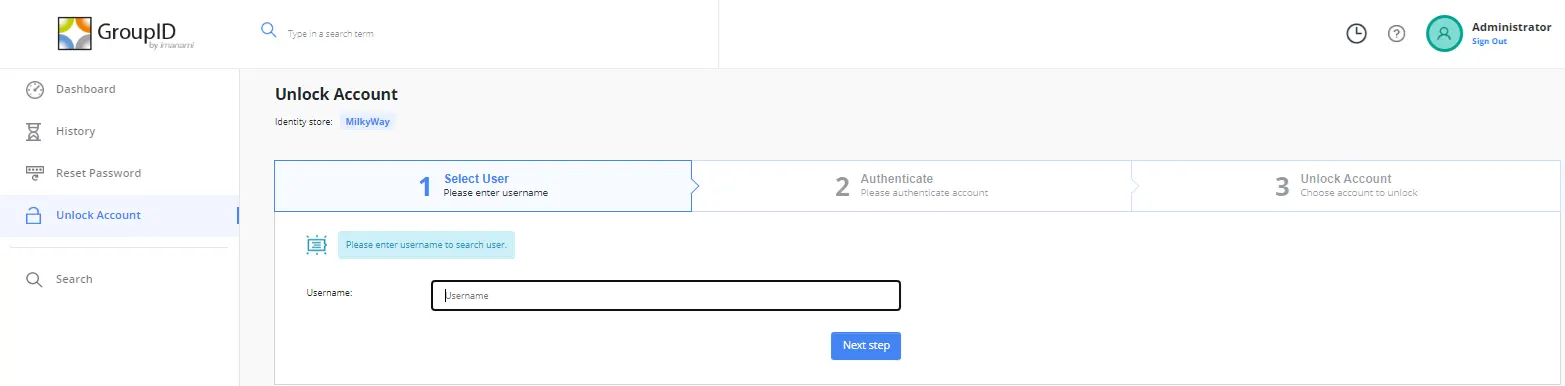
Helpdesk users can use the Dashboard, History, and Live Updates options of the helpdesk portal to audit and examine the tasks carried out by end-users on the user portal.

When a user modifies any object in the directory, the Password Center portals send email notifications to specified recipients to alert them to the changes.
Conclusion
In this blog, we have identified that the most calls or emails to IT helpdesk relate to the common issues of forgotten passwords and locked accounts due to multiple wrong password attempts. We have discussed the scenarios of using the traditional Microsoft tools like ADUC and ADAC for resetting the passwords for end-users and their limitations when it comes to resetting passwords for multiple users. Then we have discussed the password reset and password change scenarios for single users and multiple users using the PowerShell cmdlet, Set-ADAccountPassword. We have also discussed password change for multiple users using a csv file, and then discussed the powerful GroupID Password Center tool by Imanami, which makes it easier for the helpdesk and even end-users to perform password related operations.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.

