Table Of Contents
Users’ Attributes Management with ADUC
Set-ADUser Cmdlet
Set-ADUser Parameters
Set-ADUser Examples
- Change the Office and State AD Attributes
- Change the Title Attribute
- Set the Manager Property
- Set Properties with “Set-ADUser Replace”
- Replace Multiple Attributes
- Update Attributes for Multiple Users
- Update Multiple Attributes for Users from a CSV
- Use Alternate Credentials
- Clear an Attribute Value via Set-ADUser
- Disable AD User Accounts
- Bulk Update to AD Users’ Account Properties
- Force Active Directory Users to Change Password at Next Logon
Manage Users’ Attributes with ADUC
Managing bulk changes to user accounts has limited support in the Active Directory Users and Computers console. Administrators can right-click several user accounts and select Properties to launch user properties, where they can make a few basic changes, such as changing the users’ description and office location. PowerShell is used more frequently for changes to multiple user account properties.
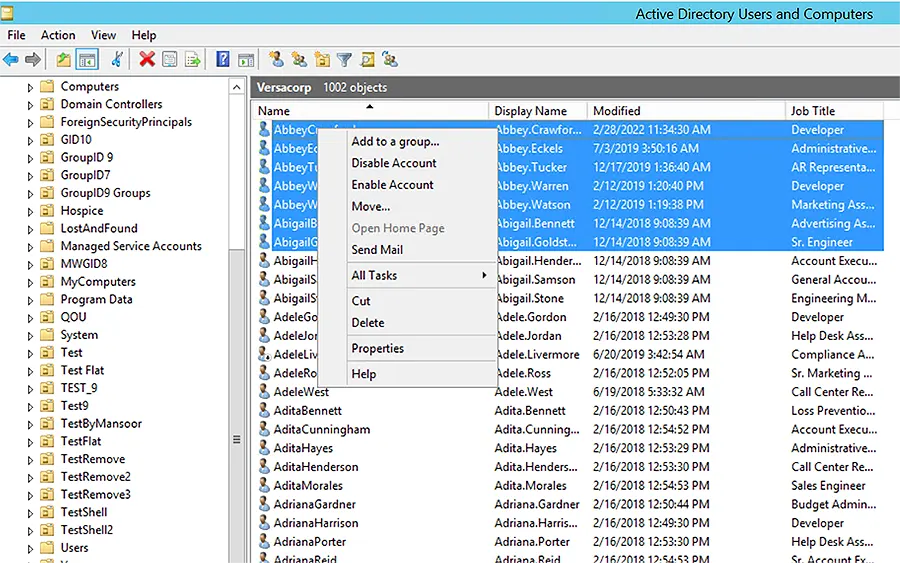
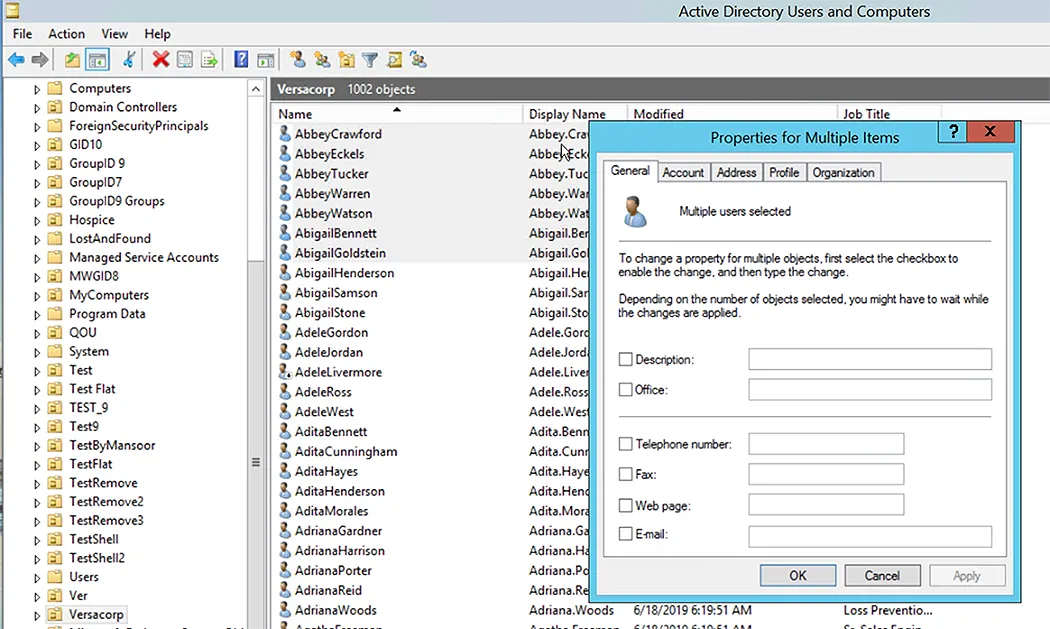
Set-ADUser Command-let
The Set-ADUser command-let modifies Active Directory user properties.
Using the command-let arguments, you can change the values of commonly used properties. The following parameters can be used to set property values that are not related to command-let arguments:
- Add
- Remove
- Replace
- Clear
Set-ADUser Parameters
Following are the Set-ADUser parameters that enables the change in AD User Properties.
Parameters |
Functions |
|---|---|
| (A) | |
-AccountExpirationDate |
Sets the account expiration date of the user object. |
-AccountNotDelegated |
If the user’s security context is delegated to a service, this value is true. |
-Add |
Adds one or more values to a property that can’t be changed using a cmdlet parameter. |
-AllowReversiblePasswordEncryption |
Indicates if the account is allowed to use reversible password encryption. The AllowReversiblePasswordEncryption property of the account is set by this parameter |
-AuthenticationPolicy |
Specifies an authentication policy object for Active Directory Domain Services. |
-AuthenticationPolicySilo |
Sets the authentication policy silo object for Active Directory Domain Services. |
-AuthType |
Specifies the authentication method to use. The acceptable values for this parameter are: Negotiate or 0, Basic or 1. |
| (C) | |
-CannotChangePassword |
Sets a value indicating whether the password cannot be changed for the user. |
-Certificates |
Specifies an array of certificates. The cmdlet changes the account’s DER-encoded X.509v3 certificates. The public-key certificates issued to this account by the Microsoft Certificate Service are among these certifications. |
-ChangePasswordAtLogon |
Sets whether the user must change their password at the next login. |
-City |
Specifies the city or town of the user. |
-Clear |
Clears one or more values of an attribute that cannot be changed using a command-let parameter. |
-Company |
Sets the company attribute of the user account. |
-CompoundIdentitySupported |
Indicates whether a user’s account supports Kerberos service tickets, which include the user’s device’s authorization data. |
-Confirm |
Prompts you for confirmation before running the cmdlet. |
-Country |
Sets the country or region code for the user account. |
-Credential |
Specifies the user account credentials that will complete this task. Unless the cmdlet is launched from an Active Directory PowerShell provider drive, the default credentials are those of the logged-on user. |
| (D) | |
-Department |
Updates the department of the user. |
-Description |
Updates the description of the user account. |
-DisplayName |
Updates the display name of the user. |
-Division |
Changes the division of the user. |
| (E) | |
-EmailAddress |
Updates the email address of the user. |
-EmployeeID |
Updates the employee ID of the user. |
-EmployeeNumber |
Updates the employee number of the user. |
-Enabled |
Updates the state of the user account as enabled or disabled. |
| (F) | |
-Fax |
Updates the fax number of the user. |
| (G) | |
-GivenName |
Updates the first name of the user. |
| (H) | |
-HomeDirectory |
Updates the home directory of the user. |
-HomeDrive |
Sets the UNC path of the home directory of the user account. |
| (I) | |
-Identity |
Gets the user account whose properties need to be changed. |
-Initials |
Updates the middle initials of the user account. |
-Instance |
Sets an ADUser object that identifies the Active Directory user object to be changed, and the modifications to be made to that object. Any changes made to the ADUser object are also propagated to the appropriate Active Directory object when this parameter is supplied. Only the object properties that have changed are updated by the cmdlet. |
| (K) | |
-KerberosEncryptionType |
Sets whether a user’s account is compatible with Kerberos encryption types, which create service tickets. |
| (L) | |
-LogonWorkstations |
Updates the logon workstations of the user. |
| (M) | |
-Manager |
Updates the manager of the user. |
-MobilePhone |
Updates the mobile phone number of the user. |
| (O) | |
-Office |
Updates the physical office location of the user. |
-OfficePhone |
Updates the office phone number of the user. |
-Organization |
Updates the organization of the user. |
-OtherName |
Updates any other name property of the user. |
| (P) | |
-Partition |
Provides the distinguishing name of an Active Directory partition. One of the current directory server’s naming contexts must be the differentiated name. |
-PassThru |
Returns an object that represents the object you are working with. By default, this cmdlet does not generate any output. |
-PasswordNeverExpires |
Empowers the user account to never change the password. |
-PasswordNotRequired |
Sets the user account without a password. |
-POBox |
Updates the PO Box of the user. |
-PostalCode |
Updates the postal code of the user. |
-ProfilePath |
Updates the profile path of the user. |
| (R) | |
-Remove |
Removes one or more values of the properties that cannot be modified using a command-let parameter. |
-Replace |
Replaces one or more values of the properties that cannot be modified using a command-let parameter. |
| (S) | |
-SamAccountName |
Provides the security account manager (SAM) account name of the user on creation. |
-ScriptPath |
Updates the logon script for the user. |
-Server |
Updates the logon server of the user. |
-ServicePrincipalNames |
Updates the service principal name of the user. |
-SmartcardLogonRequired |
Sets the value of a user’s smart card logon, if required. |
-State |
Updates the state of the user. |
-StreetAddress |
Updates the street address of the user. |
| (T) | |
-Title |
Updates the title of the user. |
-TrustedForDelegation |
Sets whether a Kerberos delegation account can be trusted. A service running under a trusted Kerberos delegation account can take on the identity of a client requesting the service. |
| (U) | |
-UserPrincipalName |
Updates the user principal name property of a user in the format: testuser@testdomain.com. |
| (W) | |
WhatIf |
Shows what will happen after running the command-let. |
Lets elaborate on -Identity parameter of Set-ADUser as below.
-Identity
The Identity parameter in the Set-ADUser command-let specifies the Active Directory user that you want to modify. A user can be identified by its:
- Distinguished Name (DN)
- GUID
- Security Identifier (SID)
- Security Account Manager (SAM) Account Name
You may also use the Identity parameter to feed an object through the pipeline or set it to an object variable like $localUserObject.
For example, the Get-ADUser command-let can be used to retrieve a user object, which can then be passed via the pipeline to the Set-ADUser command-let.
Set-ADUser Examples
Following are the examples for using Set-ADUser Cmdlet in powershell.
Change the Office and State AD Attributes
Change the following AD attributes for the AbbeyCrawford object to demonstrate updates for various user account attributes:
- Change the value of the Office attribute from Miami to Atlanta
- Change the value of the State attribute from FL to GA
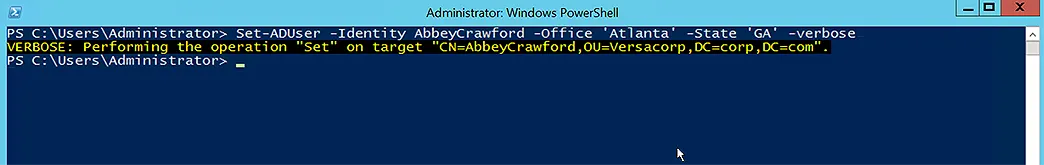
Set-ADUser has parameters that correspond to Active Directory attributes, as shown below:
Set-ADUser -Identity AbbeyCrawford -Office 'Atlanta' -State 'GA'
When you run the Set-ADUser command-let, there is no output by default. The Verbose parameter can be used to adjust this behavior. The Verbose argument provides extensive information about the task that the command-let is performing.
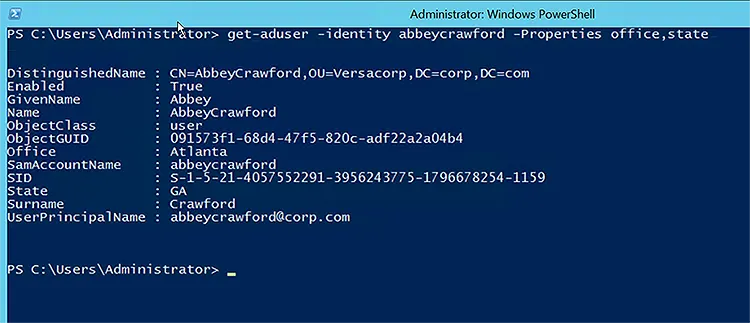
Notice that Atlanta and Georgia (as GA) have been set as values for the Office and State AD attributes respectively for the Abbey Crawford user object.
To see the full list of parameters and syntax for the Set-ADUser command-let, run the following command-let:
Get-help Set-ADUser
Change the Title Attribute
Several parameters are available in the Set-ADUser command-let to update the property values of AD accounts. Let’s update the Title attribute for a single user account as an example.
Using the method discussed in the Change the Office and State AD Attributes section, you can update the Title property via Set-ADUser by using the Title parameter.
Set-ADUser -Identity AbbeyCrawford -Title 'CIO'
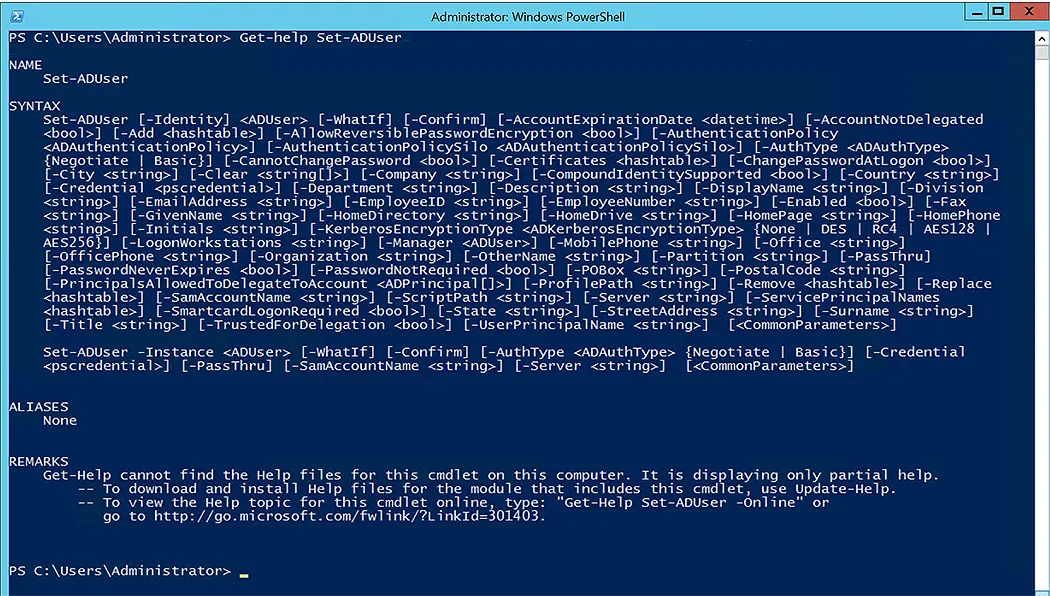
After updating the value, use Get-ADUser to double-check if the update was successful. The following image shows that the value of the AD attribute, Title, has been changed to CIO.
Get-ADUser -Identity AbbeyCrawford -Properties Name,Department,title | Select-Object -Property Name,Department,title
Set the Manager Property
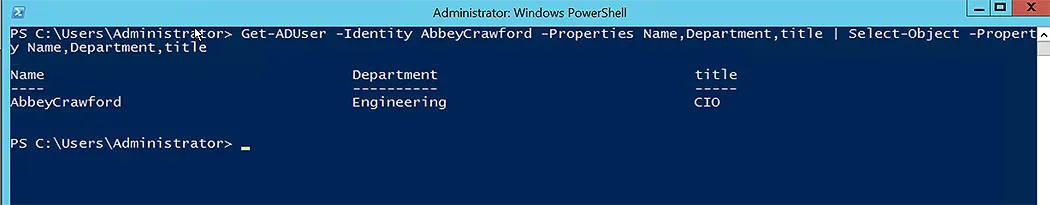
Use the manager property with the -Identity parameter in Set-ADUser to set or change a user’s manager in AD. First we need to fetch the user and then set its manager. For that, we have to combine the Get-ADUser and Set-ADUser command-lets.
Get-ADUser -Identity "AbbeyCrawford" | Set-ADUser -Manager "AbbeyEckels"
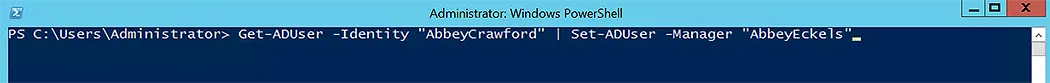
In the example above, Get-ADUser is used to get the AD user, Abbey Crawford, and then this user object is passed to the Set-ADUser command-let to update its Manager attribute. Using a unique identifier, such as user principal name or UPN, you can get an AD user.
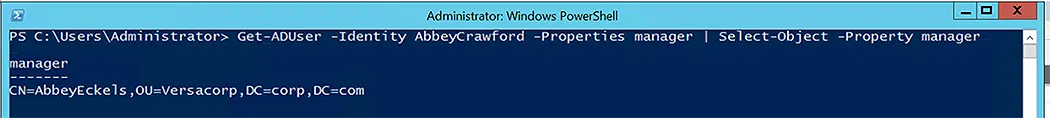
You can confirm the change by using the following command-let:
Get-ADUser -Identity AbbeyCrawford -Properties manager | Select-Object -Property manager
Set Properties with “Set-ADUser Replace”
Set-ADUser Replace can be used to replace an object property’s current value with a new value. To change an object’s property, use the LDAP display name to identify that object.
Consider this scenario: we want to update an employee’s title and email address using Set-ADUser Replace.
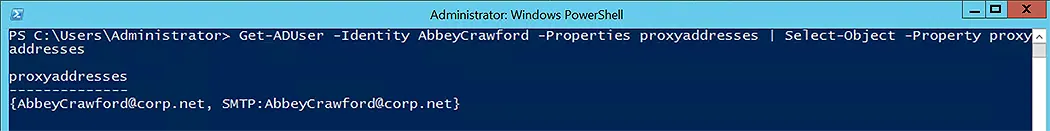
Set-ADUser -Identity Abbey.Crawford -Replace @{title="manager";mail="AbbeyCrawford@corp.net"}
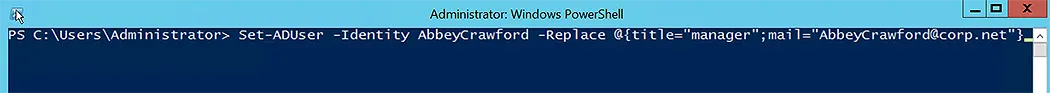
This command updates the Abbey Crawford user title to manager and email address to AbbeyCrawford@corp.net.
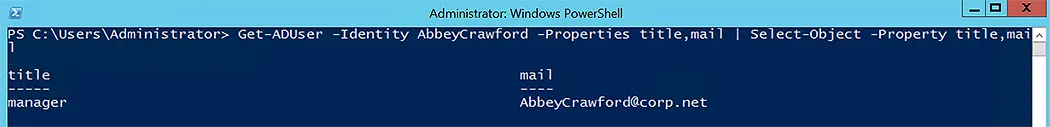
You can verify the changes via the following command-let:
Get-ADUser -Identity AbbeyCrawford -Properties title,mail | Select-Object -Property title,mail
Replace Multiple Attributes via Set-ADUser
To update numerous properties for Active Directory users, such as department and company name, run the following command-let:
Get-ADUser -SearchBase " OU=Engineering,OU=Versacorp,DC=corp,DC=com" -filter * -Properties Department,Company,l,st | Set-ADUser -Replace @{Department=”Engineering”;Company="VersaCorp";l=”San Francisco”;St=”CA”}
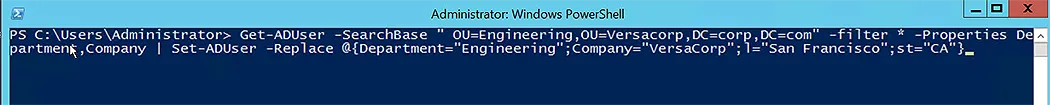
- The first command in the PowerShell script fetches AD users from the given OU and delivers the output to the second command.
- The second command utilizes Set-ADUser to replace several attributes, such as department and company name, for all the users returned.
To inspect the output of the Set-ADUser replace multiple attributes command, run the following script to get AD users for the chosen OU:
Get-ADUser -SearchBase "OU=Engineering,OU=Versacorp,DC=corp,DC=com" -Filter * -Properties DisplayName,Department,Company,l,st | select-object -property DisplayName,Department,Company,l,St
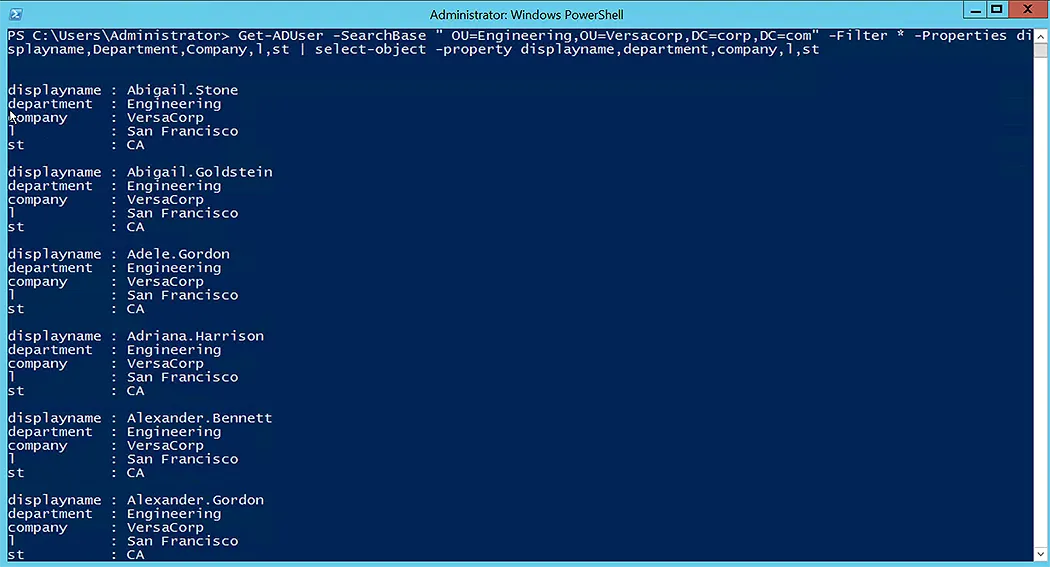
Update Attributes for Multiple Users via Set-ADUser
In the above example, the Get-ADUser cmdlet returns a list of all users in the OU=Engineering,OU=Versacorp,DC=corp,DC=com OU. Use the following Set-ADUser command to update the DisplayName attributes:
Get-ADUser -Filter 'Name -like "*"' -SearchBase ”OU=Engineering,OU=Versacorp,DC=corp,DC=com” -Properties DisplayName | % {Set-ADUser $_ -DisplayName ($_.GivenName + ' ' + $_.SurName)}
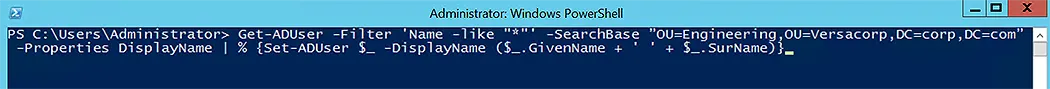
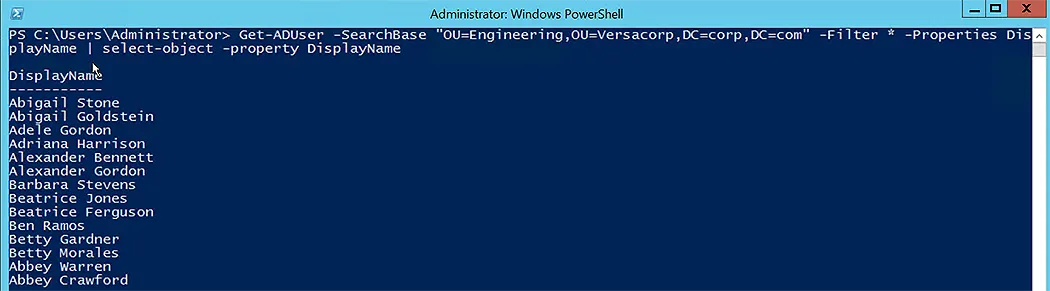
To inspect the output of this cmdlet, run the following script to get AD users for the chosen OU:
Get-ADUser -SearchBase "OU=Engineering,OU=Versacorp,DC=corp,DC=com" -Filter * -Properties DisplayName | select-object -property DisplayName
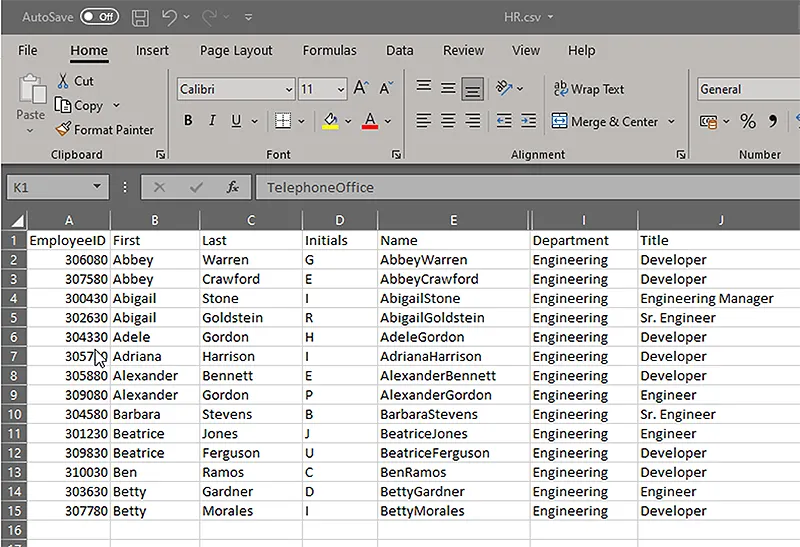
Update Multiple Attributes for Users from a CSV using Set-ADUser
Consider the following script to update multiple properties of AD users, such as Title and Department, from a CSV file:
- If you are running the command-lets from a domain controller Power Shell, then you do not have to run the command-let to import the Active Directory module for Windows PowerShell.
- If you are using a client computer with Windows client or member server operating system, then you need to import the Active Directory module; else you will get an error message for all the command-lets you run.
Import-Module ActiveDirectory
In the following command-let, the “$Users” variable will fetch the users’ information from the CSV file:
$users = Import-csv -Path c:\hr.csv
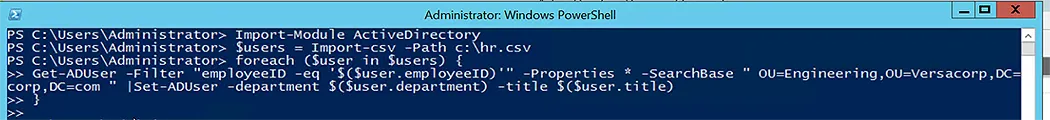
In the following, we are using the “foreach” loop to go for every user in a row and then we are using the Get-ADUser and Set-ADUser command-lets to perform the action for each user.
foreach ($user in $users) {
Get-ADUser -Filter "employeeID -eq '$($user.employeeID)'" -Properties * -SearchBase " OU=Engineering,OU=Versacorp,DC=corp,DC=com" |Set-ADUser -department $($user.department) -title $($user.title)
}
Using the Get-ADUser command-let, iterate over $user to get users from each OU in Active Directory. To update the department and title of an employee, use the received employee user object and the pipeline (|) parameter in the Set-ADUser command-let.
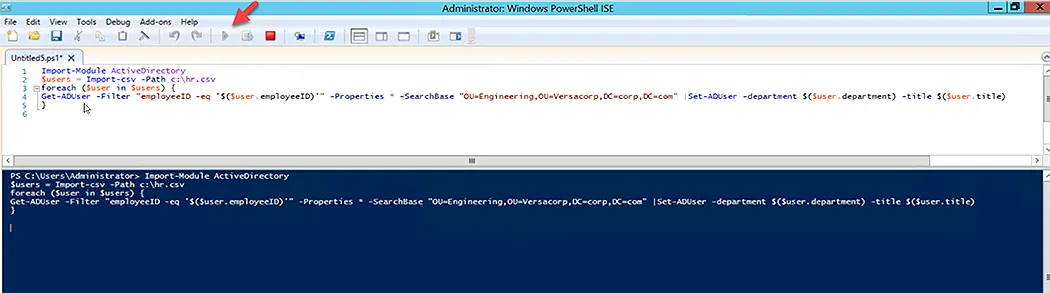
Even if you can write the script line by line in Windows PowerShell, it is recommended to use Windows PowerShell ISE for large scripts, as shown below:

Windows PowerShell ISE has two sections:
- Script Editor
- PowerShell Console
The following image shows how the command-let or script is being run. There is a toolbar button for playing and stopping the script.
Use Alternate Credentials
By default, Set-ADUser runs in the context of the currently logged-on user b. However, you can override this behavior by using the Credential argument to specify a different credential set.
To authenticate to AD with alternate credentials, use Get-Credential to produce a PS Credential object, as shown below.
$credential = Get-Credential
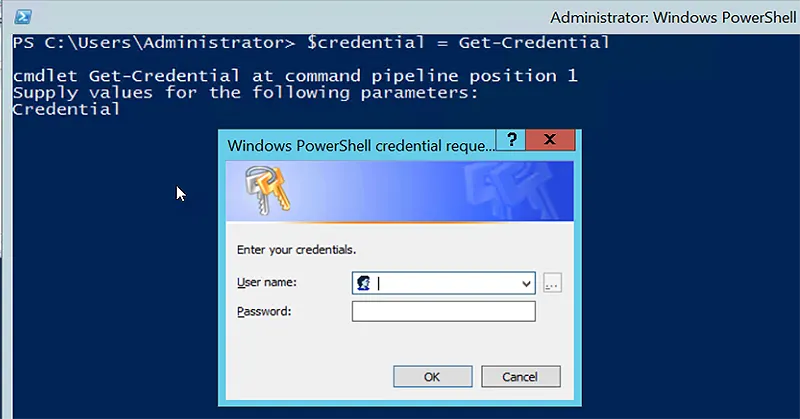
Now, with Set-ADUser, pass the PSCredential object to the Credential parameter, as seen below. This instructs AD to authenticate and make the required modification using the login and password contained in the credential set.
Set-ADUser -Identity AbbeyCrawford -Title “Senior Software Developer” -Credential $credential
Clear an Attribute Value
To clear the value for an Active Directory user attribute, use Set-ADUser -Clear attribute.
Consider the following command-let to clear the value of the Department attribute:
Get-ADUser -filter * -SearchBase " OU=Engineering,OU=Versacorp,DC=corp,DC=com" | Set-AdUser -clear department
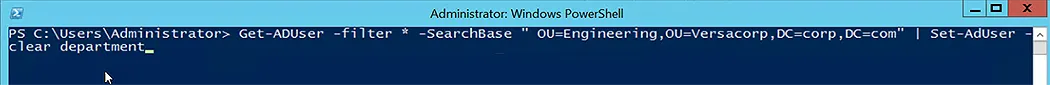
- The Get-ADUser command-let retrieves a user from the specified OU and passes the result to the second command-let.
- Next, Set-ADUser is used to clear attribute values.
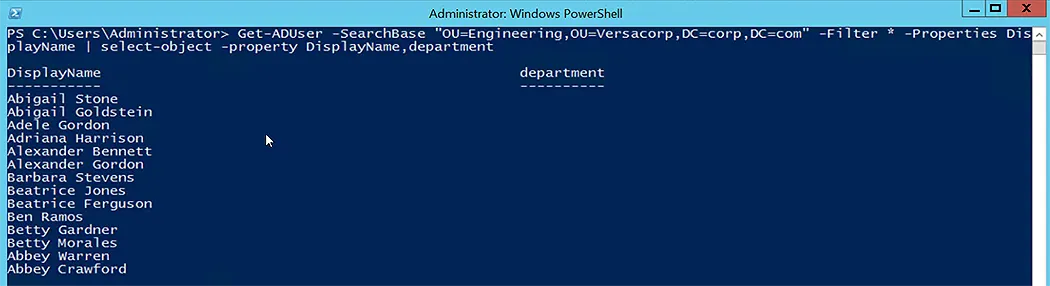
The following is the output when we run the Get-ADUser command-let:
Get-ADUser -SearchBase "OU=Engineering,OU=Versacorp,DC=corp,DC=com" -Filter * -Properties DisplayName | select-object -property DisplayName,Department
Disable AD User Accounts
We need to maintain track of active user accounts and accounts that are no longer in use. We also need to disable Active Directory accounts of users who leave the organization.
Scenario: Let’s use Set-ADUser to deactivate the account of an employee named Don who departs an organization.
To begin, we’ll use the Get-ADUser command-let to determine whether an AD user account is enabled or disabled.
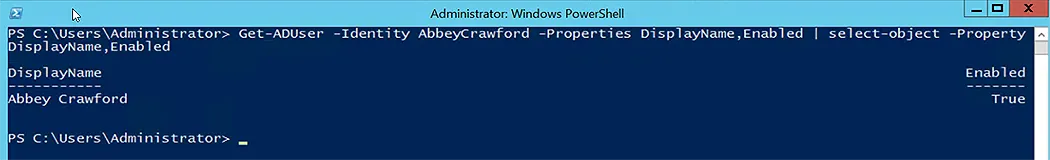
Get-ADUser -Identity AbbeyCrawford -Properties Enabled | Select Enabled
- If the Get-ADUser Enabled property is True, the account is active.
- If it is False, the account is disabled.
Following is the output of the above-mentioned command, showing that the user is active.
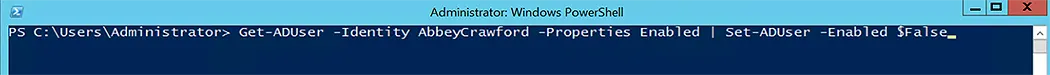
When a user leaves the company, his/her Active Directory account status must be set to disabled. We’ll disable the account using the Set-AdUser command-let, as shown below:
Get-ADUser -Identity AbbeyCrawford -Properties Enabled | Set-ADUser -Enabled $False
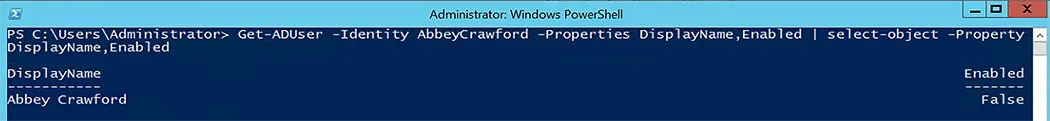
- The first command in the script gets the AD user’s enabled status and gives the result to the second command.
- The second operation uses Set-ADUser with Enabled = False to disable the user account.
We can check the output of the Set-ADUser command-let by running the following command-let:
Bulk Update to AD Users Account Properties via Set-ADUser
Using PowerShell to make mass changes to the properties of multiple user accounts involves two stages:
- Determine which accounts need to be changed
- Make the required update
Defining the accounts for update can be done in a variety of ways.
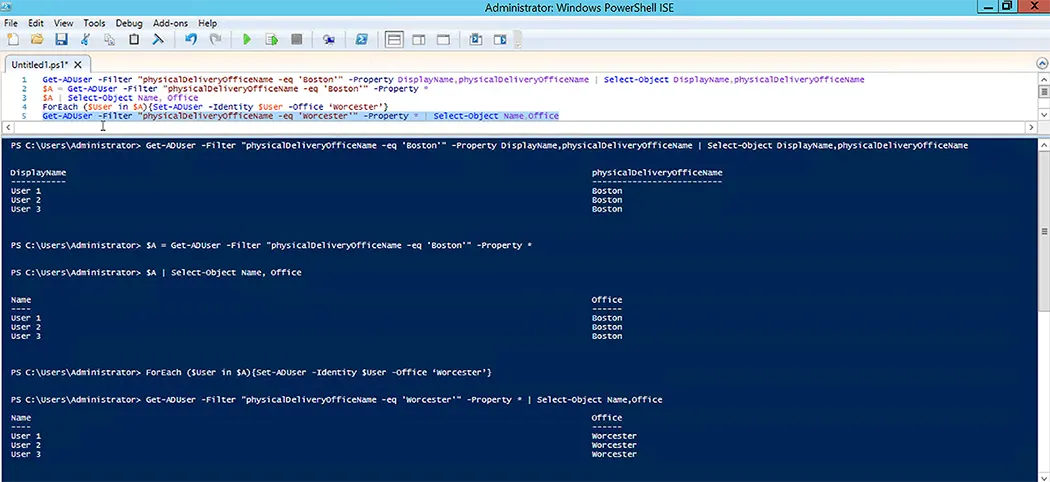
Use Case: Consider the case where all users in a company’s Boston office are being relocated to the Worcester office. In this case, the HR department may give a CSV file with a list of relocated users to the IT department. In this scenario:
- First read the CSV file with the Import-CSV command-let.
- Next, create a loop to handle all the accounts in the CSV file, as we have done in the Update Multiple Attributes for Users from a CSV using Set-ADUser section.
It’s also feasible for the HR department to not offer a list to IT department, rather inform them that all the employees in Boston are being relocated to Worcester. In this instance, IT would have to create its own user list based on existing user account information. Use the following command to find all the users in the Boston office:
Get-ADUser -Filter "physicalDeliveryOfficeName -eq 'Boston'" -Property DisplayName,physicalDeliveryOfficeName | Select-Object DisplayName,physicalDeliveryOfficeName
Of course, the final goal is to update the users’ office location, so using a command-let to transfer the output of this program to a variable could be a better solution.
$A = Get-ADUser -Filter "physicalDeliveryOfficeName -eq 'Boston'" -Property *
The Property switch is introduced to make the Office property available. The following command-let allows you to see the users and their offices.
$A | Select-Object Name, Office
The next step is to update the users’ office location using Set-ADUser. However, assuming that more than one user account is being edited, a ForEach loop is required to ensure that only one user account is treated at a time. This is how the loop appears:
ForEach ($User in $A){Set-ADUser -Identity $User -Office ‘Worcester’}
We must verify that the update was successful when this command-let completes. The Get-ADUser command-let, which displays a list of users in the Worcester office, is the simplest way to achieve this.
Get-ADUser -Filter "physicalDeliveryOfficeName -eq 'Worcester'" -Property * | Select-Object Name,Office
The entire sequence of command-lets will look like this:
Force Active Directory Users to Change Password at Next Logon
Properties for several user accounts can be updated at the same time. The following command, for example, will modify the value of the UserAccountControl property, forcing all users in the given OU to change their passwords at the next login.
Get-ADUser -Filter * -SearchBase "OU=Test,DC=corp,DC=com" | Set-ADUser -ChangePasswordAtLogon $true
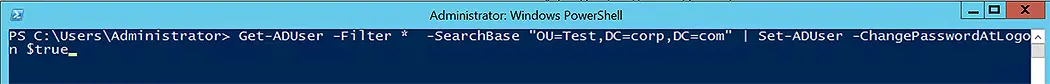
The following image shows the checkbox we just set via the above command-let:
Add and Remove Attributes with Set-ADUser
Some properties, such as ProxyAddress and otherTelephone, can have multiple values. The Add and Remove parameters in Set-ADUser can be used to set or update values in these attributes.
A comma-separated list can be used to set several values, as shown below:
Set-ADUser -Identity AbbeyCrawford -Add @{proxyAddresses="AbbeyCrawford@corp.net","AbbeyCrawford@hotmail.com"}
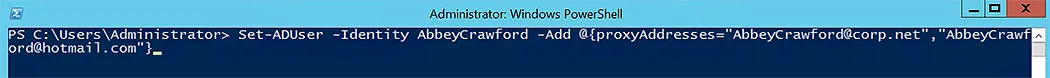
To see the output of this command-let, use the Get-ADUser command-let.
Get-ADUser -Identity AbbeyCrawford -Properties manager | Select-Object -Property manager
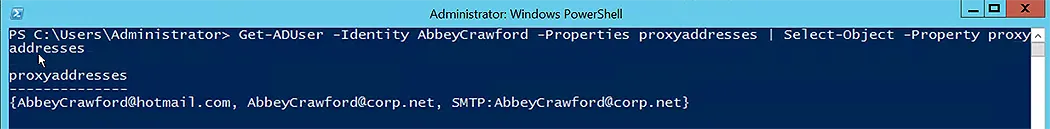
To remove a single value, we may indicate the item we want to remove from the list:
Set-ADUser -Identity AbbeyCrawford -Remove @{proxyAddresses="AbbeyCrawford@hotmail.com"}
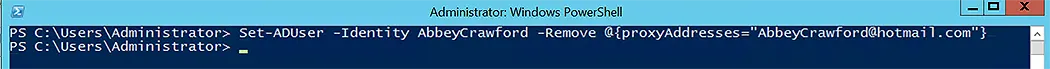
To see the output of this command-let, use the Get-ADUser command-let.
Get-ADUser -Identity AbbeyCrawford -Properties manager | Select-Object -Property manager
Notice that AbbeyCrawford@hotmail.com has been removed from the proxyAddresses list.
Manage AD Users with GroupID Shell
GroupID Shell is a command-line tool for managing objects in Active Directory and Azure-based identity stores, such as users, contacts, mailboxes, groups, Smart Groups, and Dynasties, as well as performing other administrative activities.
GroupID Shell is based on MS Windows Poweshell Technologies. It provides the platform to perform various tasks as IT Admins can do with Powershell.
In the following images, you can see that GroupID Shell command-lets are similar to PowerShell command-lets:
Following is a command-let similar to Set-ADUser, with its all parameters:
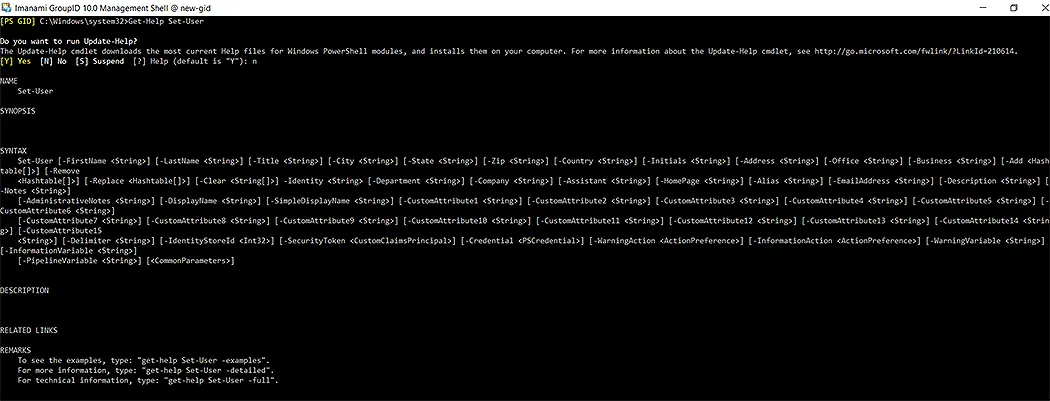
Tools to Manage ADUsers
Following are the tools to manage Active Directory Users without powershell.
GroupID’s Web-based Self-Service Portal
GroupID Self-Service allows you to quickly create and deploy web-based portals that allow end-users to administer their directory groups and direct reports.
Using a Self-Service portal, users can:
- Search the directory (this feature can be deployed for Helpdesks users)
- Maintain and update their directory profiles (end-users)
- Create and update directory objects (can be exposed to end-users and administrators)
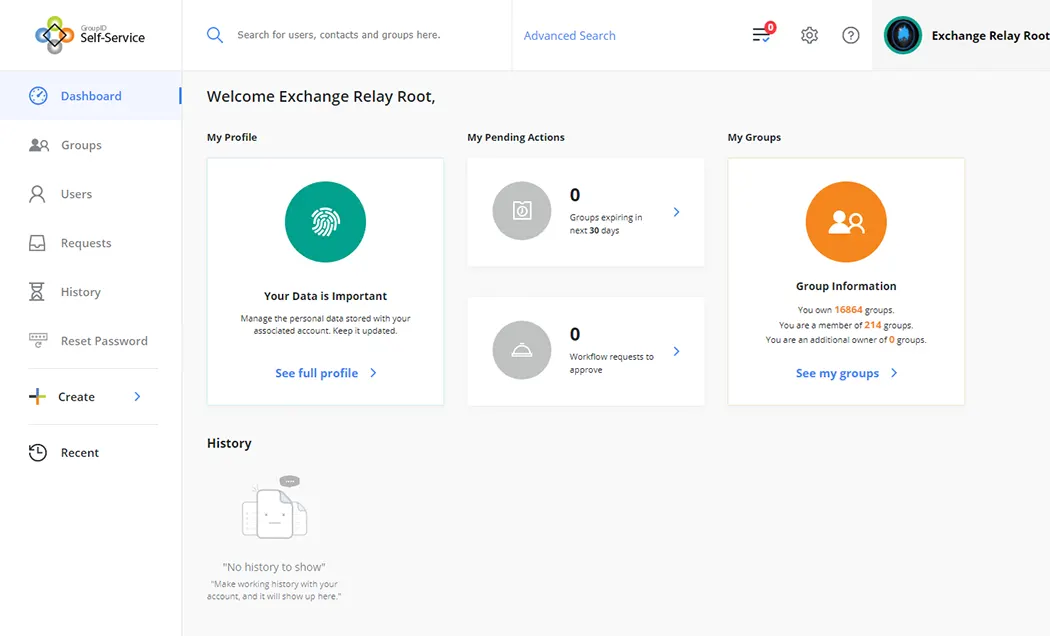
You can also use the Self-Service portal to reduce the work required to manage AD accounts. Self-Service allows end-users to create, delete and edit groups too, without assistance from an administrator.
The following images show some user attributes that can be updated through the Self-Service portal:
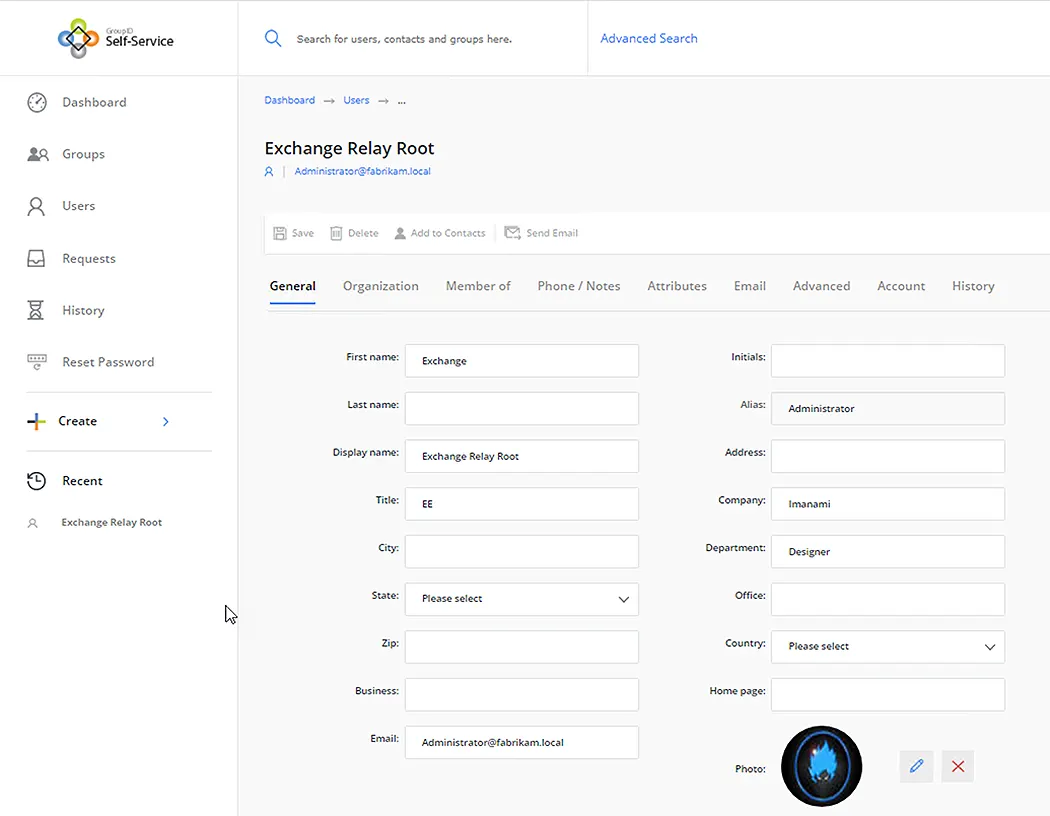
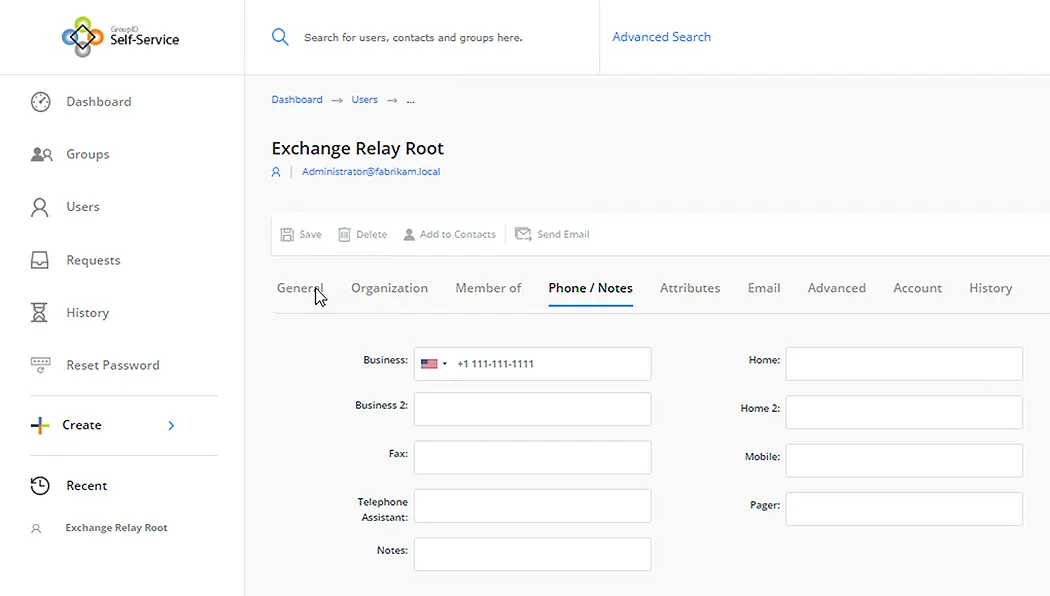
Data is more accurate and dependable when users manage and update their own information. Administrators keep complete control over data integrity, though, because they decide what users can see and modify through the portal.
Administrators can also build workflows, which act as a built-in auditing system to ensure that the correct data is entered before committing changes to the directory.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.

