A Virtual Private Network or VPN, is a technology that helps you establish an encrypted environment on your network so that when you access the World Wide Web, your system is safe and secure from prying eyes.
In addition to this, VPN also facilitates in hiding your IP address so that you can visit websites that are not accessible in your location. Ever since Covid-19, organizations from all over the globe have resorted to remote work to mitigate the risk of contracting the virus. In such crucial times, VPN services act as a lifesaver by encrypting your data, which ensures that all the important files are safe from intruders.
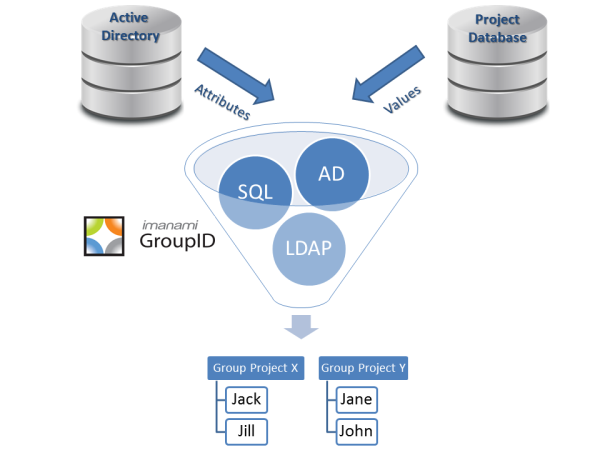
Active Directory VPN Management via Groups
A team member of mine recently complained that he was unable to access VPN on our network despite trying everything that he could.
Before contacting the help desk, I decided to troubleshoot the problem myself. Since security groups in Active Directory are capable of managing nearly everything, I instantly went to our Active Directory Self-Service portal to see what security group memberships I had that my team member didn’t.
Observation: It was an easy fix
While investigating the issue, I observed that:
-
- My colleague didn’t have membership in a security group called “Access from home”, which was exactly why he was experiencing the VPN issue.
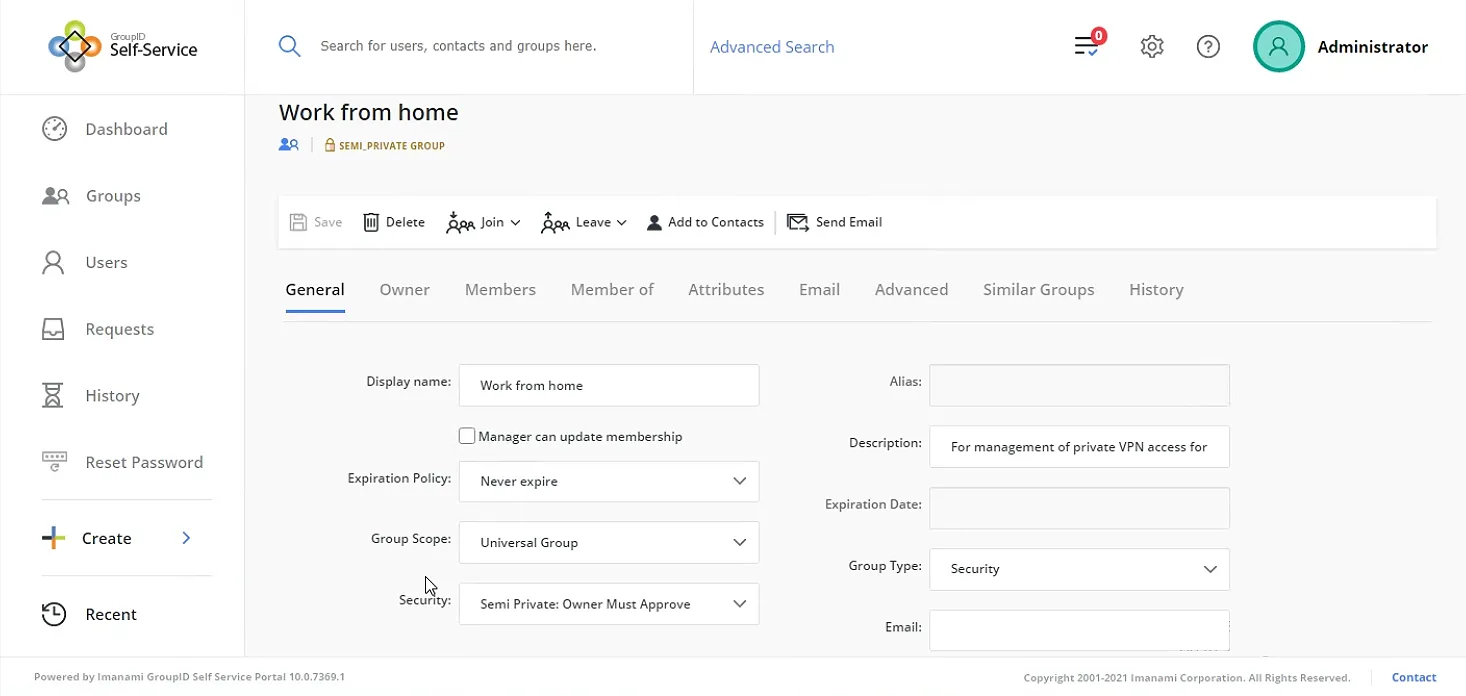
- The active directory group “Access from home” was semi-private (the owner has to approve the new member), a feature that GroupID provides.
- The group owner was the CEO, and the team member sent him a request to be a part of the group.
The moment the request was accepted, the team member got access to the network via the security group.
Active Directory VPN Access on Differing Time Periods
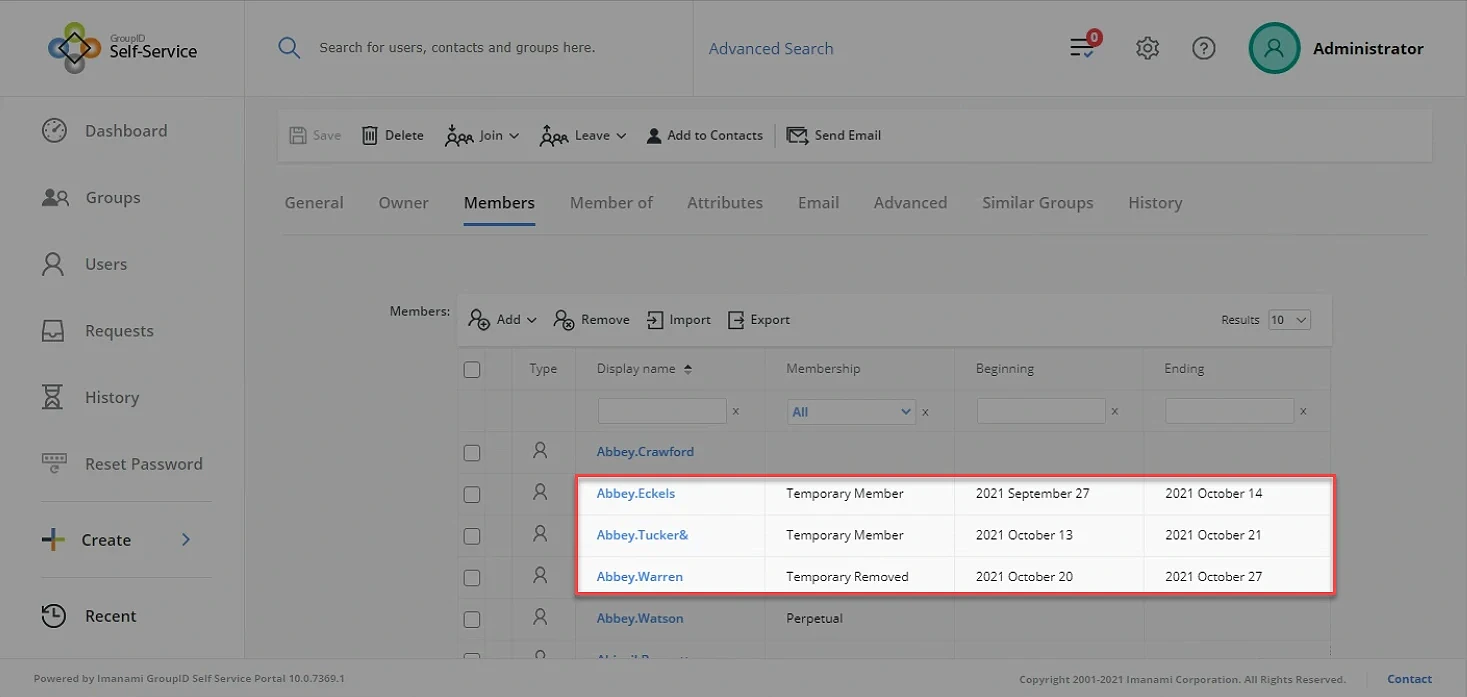
It also came to my knowledge that two other individuals were not a part of the “Access from home” group. One of the members, Thomas Watson, needed access only for one month (a specific time), and the other member, Hannah Murray needed permanent access to VPN via active directory.
This meant that access had to be granted based on a time period that was different for both individuals. In this scenario, I used Group ID’s self-service feature: Membership Lifecycle that allowed me to do the task hassle-free.
VPN Access in Active Directory via Lifecycle Management
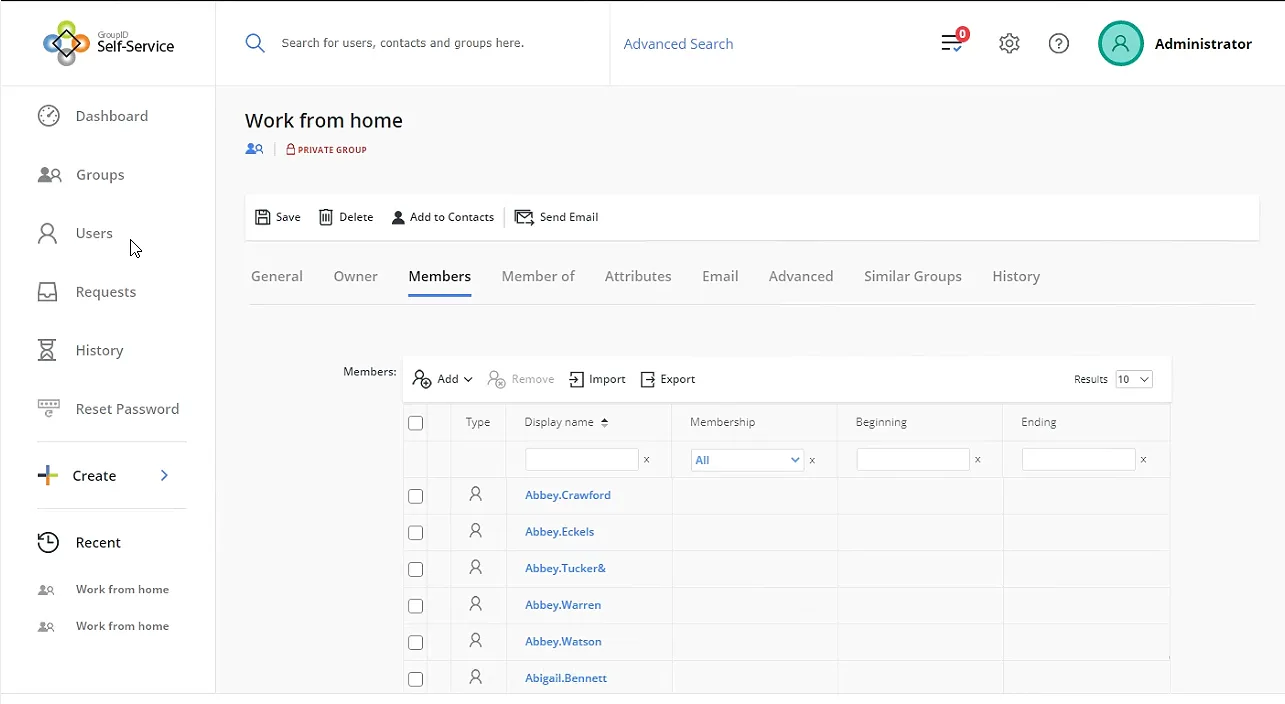
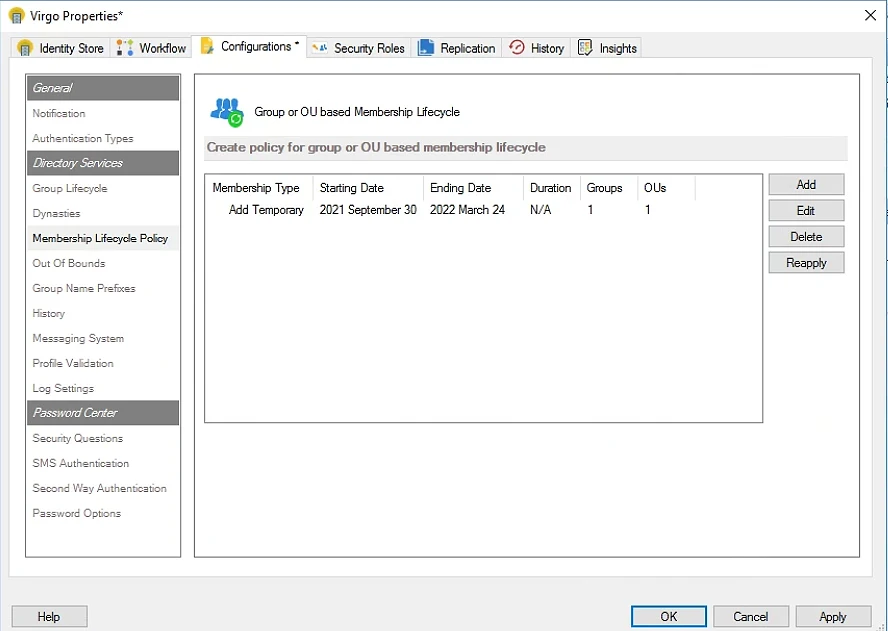
The Lifecycle feature in GroupID Self-Service enables group owners to specify the dates against each member being added to the group using the Members tab in group properties. When the specified period ends, the members are instantly added or removed according to the dates set. Managers and peers can also join and leave a group temporarily on behalf of other users.
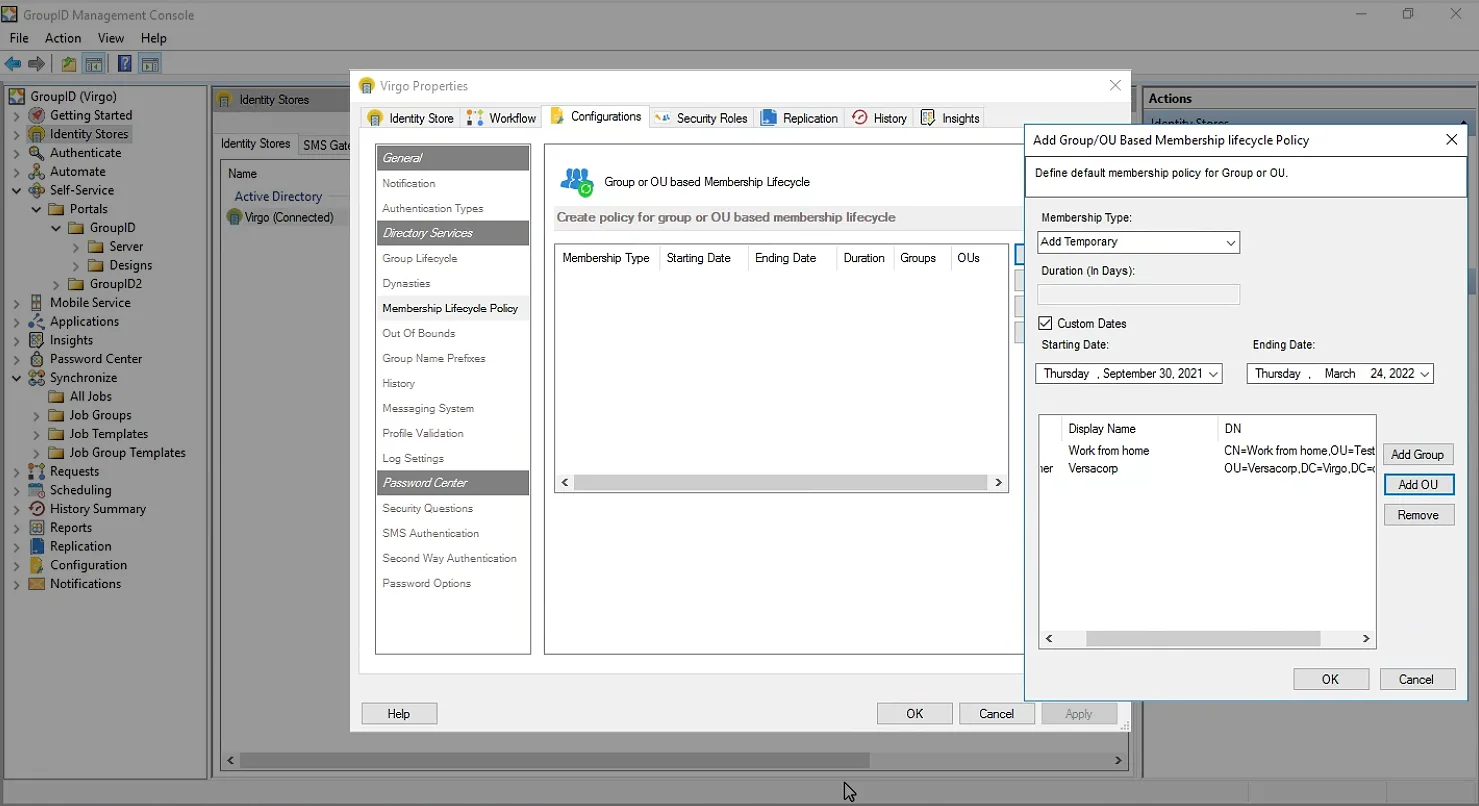
A group/OU-based membership policy enables you to specify a period so that all members added or removed from a specific group during that period are treated as temporary additions or are removed after the set date.
| Feature | Description | Identity Store Permission |
| Join/Leave on Behalf of Direct Reports | A manager can place a request to join or leave a group on behalf of users directly reporting to him/her. | Manage my Direct Reports permission should be set to Allow for the security role the requesting manager belongs to. |
| Join/Leave on Behalf of Peers | Users can place a request to join or leave a group on behalf of their peers. (Users who report to the same manager are peers to each other.) | Join/Leave on Behalf of Peer permission should be set to Allow for the security role the requesting user belongs to. |
| Join/Leave on Behalf of Any User | Any user can place a request to join or leave a group on behalf of any other user. |
Join/Leave on Behalf of Any User permission should be set to Allow for the security role the requesting user belongs to. |
You can define a group membership policy for one or more groups and OUs. In the case of an OU, the policy suffices for all active directory groups in that OU. The Membership Lifecycle job applies group/OU-based membership policies to groups.
What I did in Thomas Watson and Hannah Murray’s Case
Thomas Watson needed access for the period of one month. I used the self-service feature “Join on behalf of others” for sending the request.
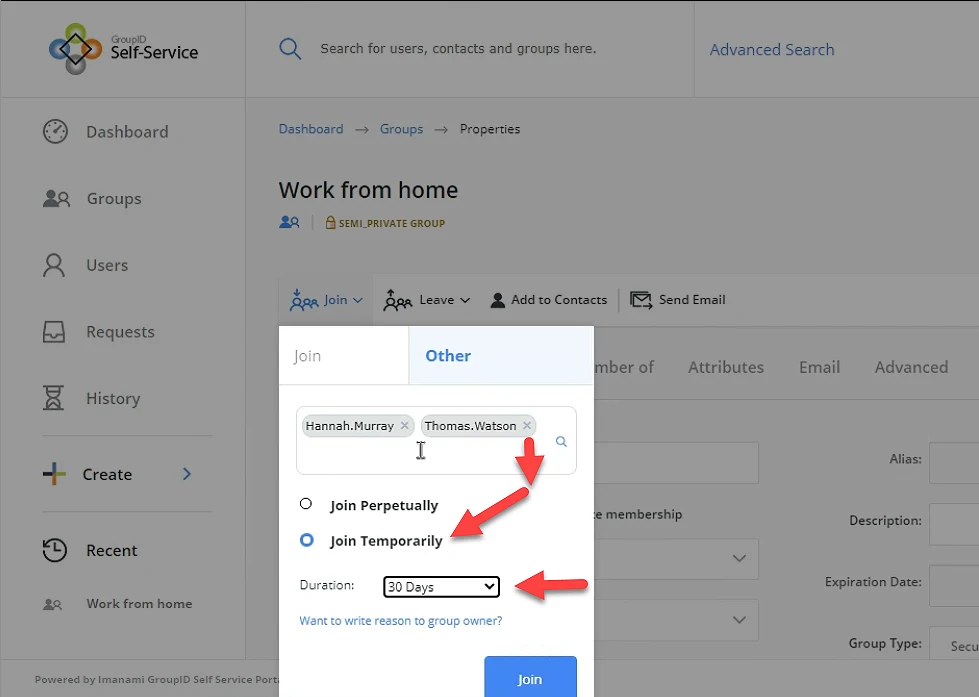
End-users can also use the “Temporary membership” feature by setting up the dates when requesting to join a group. The fields are pre-defined, for example, 7 days, 30 days, or 90 days, etc. The dates can also be customized from the date picker.
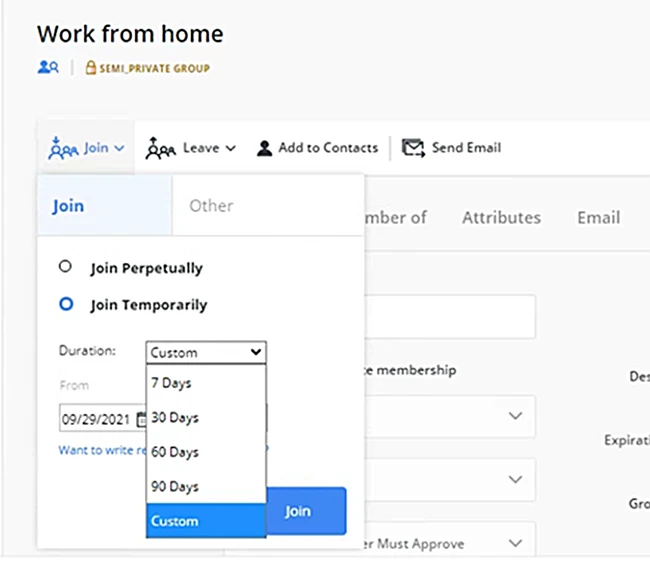
Hannah Murray, on the other hand, needed permanent access. For her, I set up the policy as “Perpetual” as shown in the screenshot below.
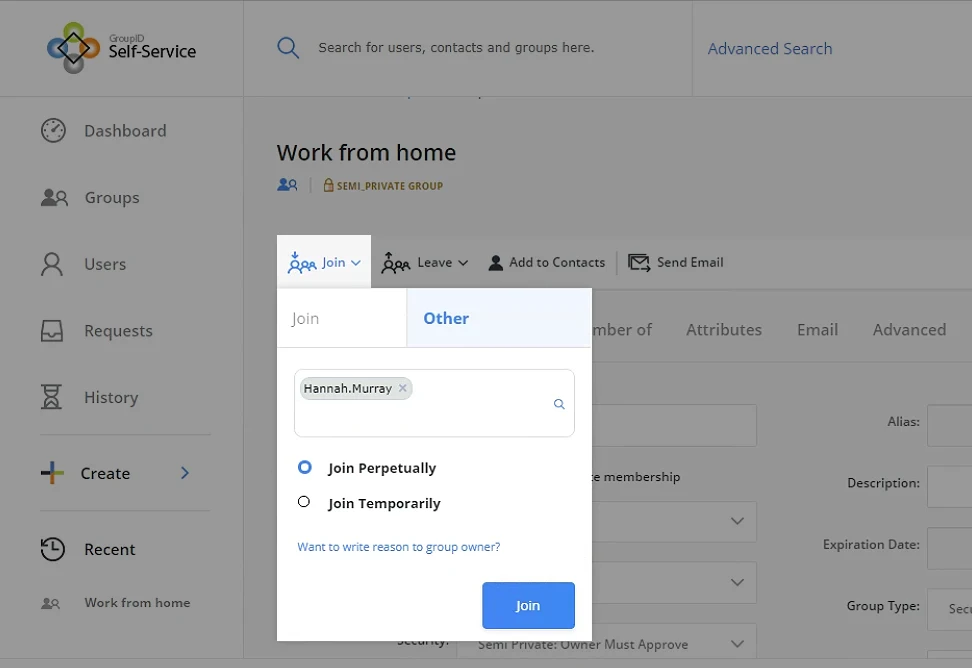
Conclusion
In just a matter of seconds, with a few clicks, active directory VPN access management via security group was successfully executed. My team members can now conveniently connect and use VPN service from the comfort of their homes in a safe environment.
GroupID solves for all Active Directory Management Challenges
Maintaining appropriate oversite of groups is critical to ensure that a group does not outlive its purpose – and should be expired and deleted when no longer needed. Delegation with fine-grained control is the key. GroupID is a comprehensive, out-of-the-box solution recognized as the top Active Directory Group Management tool. IT professionals from companies like Splunk, Nvidia, Samsung, Toshiba, Disney, and FedEx prefer GroupID among the top applications. GroupID has the highest-rated technical support as well.
GroupID by Imanami offers a suite of solutions that empowers IT professionals to manage groups, users, and entitlements effectively and automatically. Learn more about the suite of solutions under GroupID here.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.