Managing any Active Directory (AD) component using Windows PowerShell is simple. In addition to managing AD objects like users, computers, and groups, we can handle any AD functionality via PowerShell. This blog will concentrate on users and groups while explaining how you can use Windows PowerShell and the Active Directory module to obtain a user’s group memberships.
Get-ADPrincipalGroupMembership Cmdlet
The Get-ADPrincipalGroupMembership cmdlet can be used to find out which Active Directory groups a certain user, machine, group, or service account is a member of.
A global catalog is necessary for this command to do the group search. If the forest that contains the user, computer, or group doesn’t have a global catalog server, the cmdlet gives an error.
Use the ResourceContextServer parameter to indicate a different server in another domain if you wish to look for local groups there.
Table Of Contents
-
Get-ADPrincipalGroupMembership Cmdlet
-
Getting a User’s Group Membership using Traditional Methods
-
Get-ADPrincipalGroupMembership Parameters
-
Group Memberships for User in AD LDS Instance
-
Group Memberships for Administrator
-
Get the Group Memberships for an Account in Resource Domain
-
Filter Groups using Get-ADPrincipalGroupMembership
-
Get Computer Membership Using Get ADPrincipalGroupMembership
-
View Memberships using the GroupID Report Module
-
Conclusion
Getting a User’s Group Membership using Traditional Methods
There are several methods for discovering which Active Directory groups a user belongs to, such as:
- View memberships in ADUC
- Use the GPResult cmdlet
- Use the Whoami cmdlet
Using the Active Directory Users and Computers Console
ADUC remains the most common way to investigate a user’s group memberships.
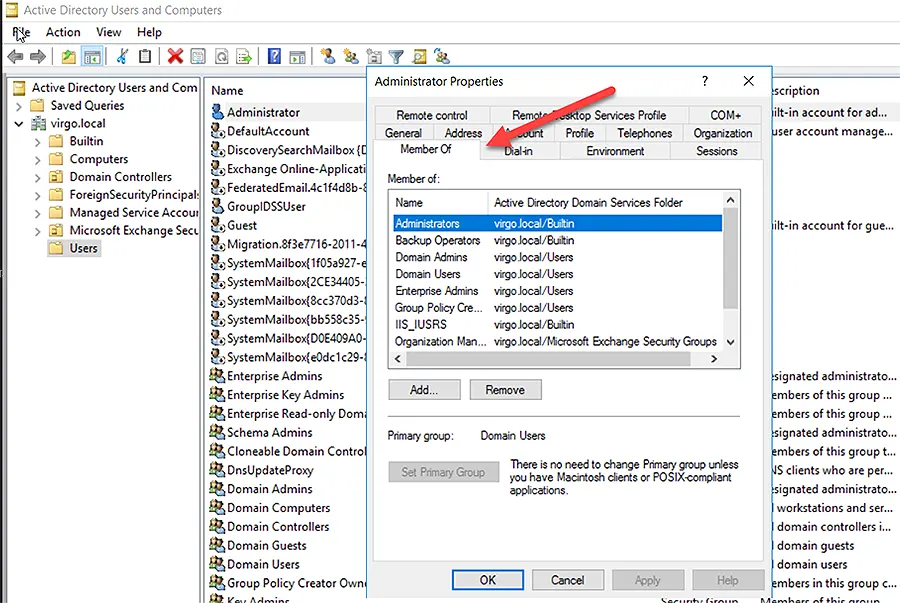
- Launch the Active Directory Users and Computers console.
- Open the properties of a user and go to the MemberOf tab, as shown below.
Using the GPResult Cmdlet as Logged-on User
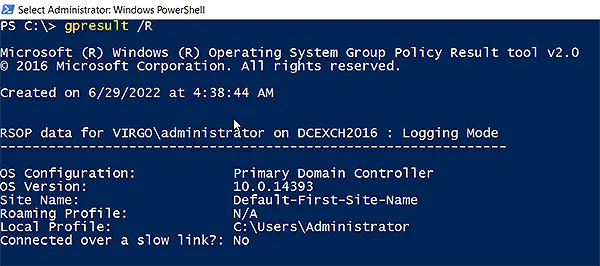
Open an elevated PowerShell command line, log in as the user you want to verify, and then issue the gpresult /R command.
Microsoft Windows Operating System Group Policy Result tool is primarily used to check the group policy settings on the client/workstation, but it also provides information about the user’s group memberships.
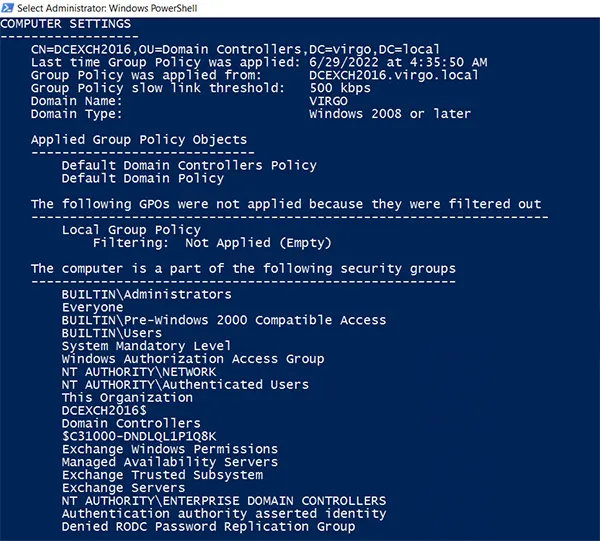
In the following screenshot, you can see the group memberships of the computer object in the Computer Settings section:
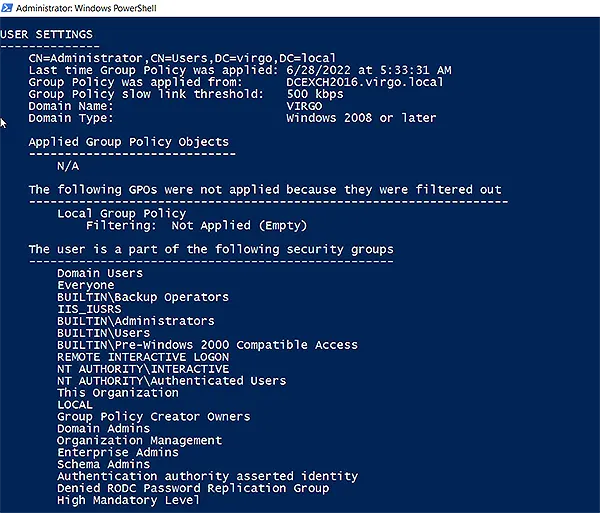
Under User Settings, you can see the memberships of the logged on user:
Using the Whoami Cmdlet for the Logged-on User
The logged-on user can also use the “Whoami /groups” cmdlet to see all his/her group memberships. It is as shown below:
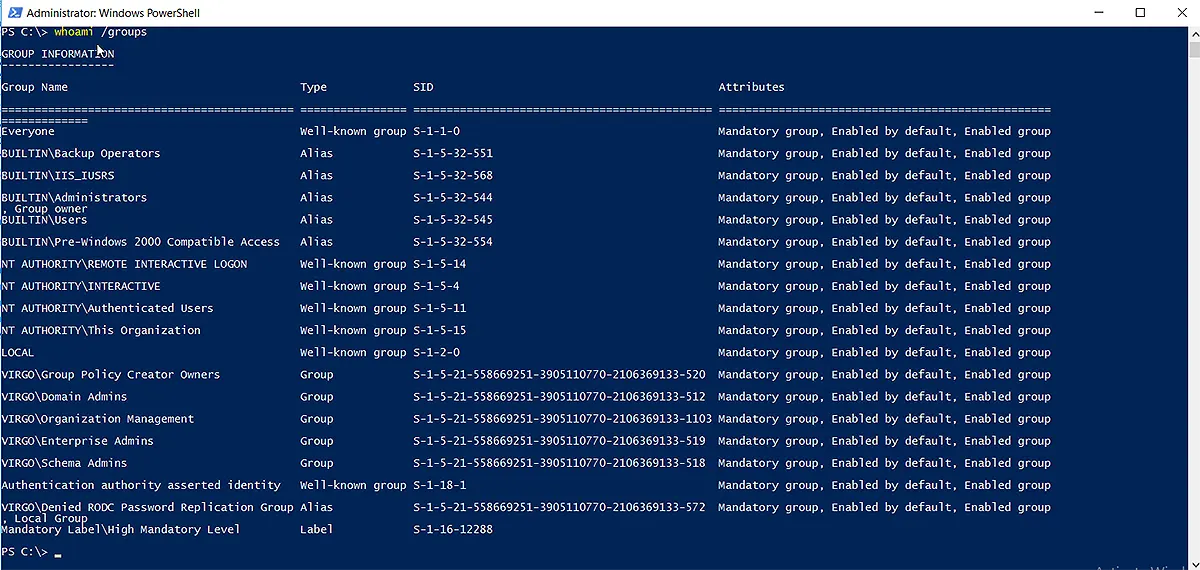
Needless to say, this is not the preferred method. What if you want to run multiple cmdlets to see several users’ group memberships? Here comes the PowerShell cmdlet, “Get-ADPrincipalGroupMembership”.
Get-ADPrincipalGroupMembership Parameters
The following parameters are most commonly used with the Get-ADPrincipalGroupMembership cmdlet:
- -AuthType
- -Credential
- -Identity
- -Partition
- -ResourceContextPartition
- -ResourceContextServer
- -Server
Following is a discussion of these parameters.
AuthType
To describe an authentication method based on Basic (or 1) or Negotiate (or 0). Its default authentication mechanism is Negotiate.
To use Basic Authentication, an SSL (Secure Sockets Layer) connection is necessary.
Credential
If you want to run the cmdlet or a script with multiple cmdlets and the logged-on user does not have enough rights, this parameter enables you to use alternate credentials.
To use the Credential parameter, use username as AbbeyCrawford or domain\AbbeyCrawford or you can create and use the PSCredential object by using the Get-Credential cmdlet.
Partition
You can specify the distinguished name of an Active Directory partition.
The Identity parameter
The user, computer, or group object for whom you want to get the group membership is specified by the Identity parameter.
- A user, machine, or group object’s distinguished name (DN), GUID, security identifier (SID), or SAM account name can all be used as parameter value to identify the object.
- You can also build a user, group, or computer object variable or provide an object via the pipeline to the Identity parameter. As a combination, you could retrieve a group object using the Get-ADGroup cmdlet and then send it through the pipeline to the Get-ADPrincipalGroupMembership cmdlet. In a similar way, you may obtain user and computer objects to pass through the pipeline by using Get-ADUser or Get-ADComputer.
You can specify the user, group, computer, or service account on which Get-ADPrincipalGroupMembership will perform the actions by using the Identity parameter.
ResourceContextPartition
Names the partition of an AD or AD LDS instance to search by its distinguishing name. To indicate a partition hosted by the provided server, combine this option with the ResourceContextServer parameter. The ResourceContextServer’s default partition is searched if the ResourceContextPartition option is not provided.
ResourceContextServer
This parameter allows you to look for groups in a domain other than the one where the user’s account is located. Include the ResourceContextPartition parameter as well if you want to search in a partition other than the domain’s default partition.
Server
You can use this parameter to provide the fully qualified domain name, NetBIOS name, or fully qualified directory server name of the AD Domain Services instance that you want to connect to (with or without port number).
Group Memberships for User in AD LDS Instance
For example, if you want to retrieve a user’s group membership information from a specific server and partition, use the following cmdlet. The -Identity parameter is used with the distinguished name of the user whose membership you want to see.
Get-ADPrincipalGroupMembership -Server localhost -Identity " CN=AbbeyCrawford,OU=Versacorp,DC=virgo,DC=local" -Partition "DC=Virgo,DC=local"
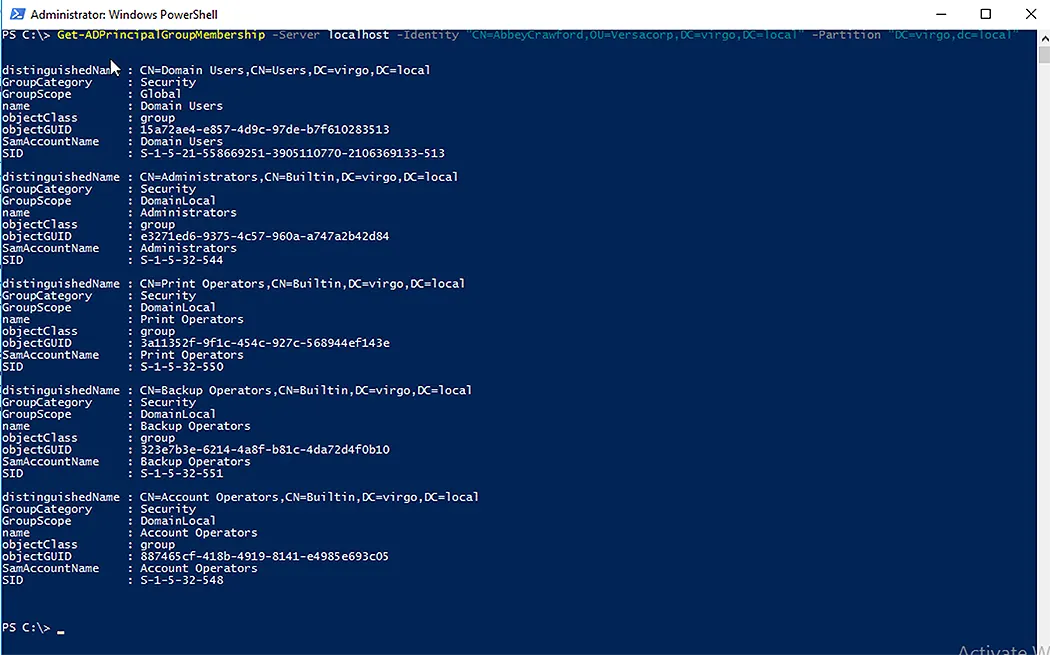
Group Memberships for Administrator
To view the group membership of built-in administrator of a domain, use the following cmdlet with the Identity parameter or without the Identity parameter containing the administrator’s name.
Get-ADPrincipalGroupMembership administrator
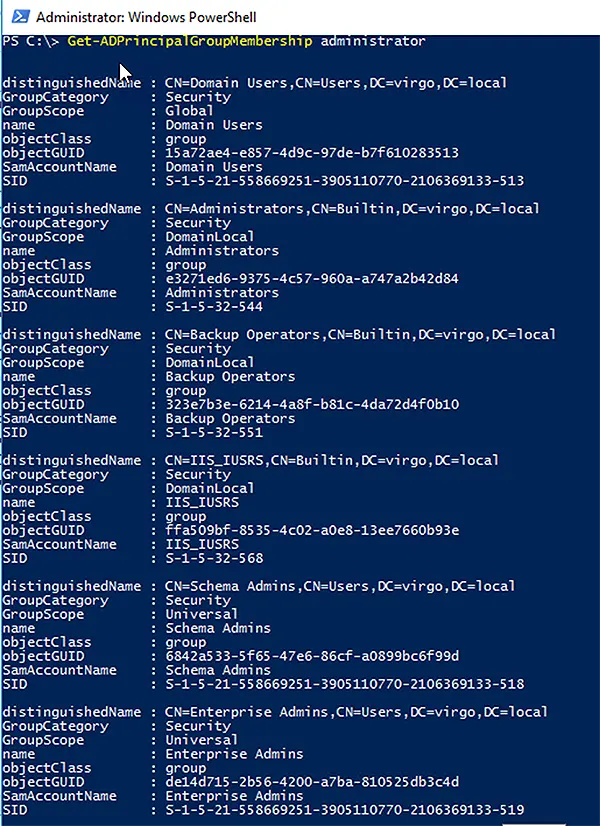
By default, the built-in administrator is a member of the commonly known security groups (e.g., Administrators, Backup Operators, Schema Admins, Enterprise Admins and Domain admins).
This information seems raw and you may want to view it in a tabular form or in columns. For that, run the Get-ADPrincipalGroupMembership cmdlet in conjunction with Get-ADGroup and select the desired properties to be displayed. Here we are using the Name and Description properties.
Get-ADPrincipalGroupMembership -Identity administrator | Get-ADGroup -Properties Description | Select Name, Description
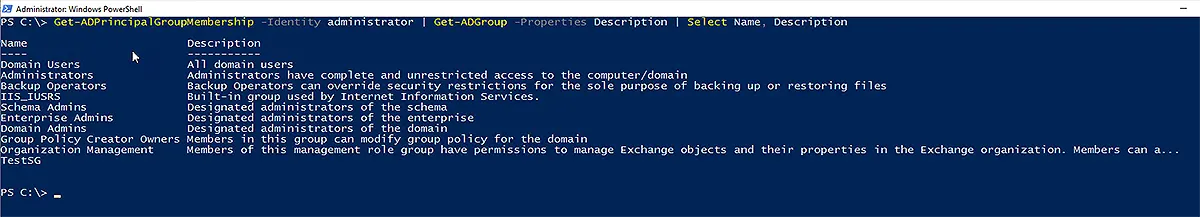
Using the first command, you get the group memberships of the user identified in the Identity parameter. Then the result passes to Get-ADGroup, which passes the description of those groups to the third cmdlet “Select”, which then prints the name and description of the membership groups in PowerShell.
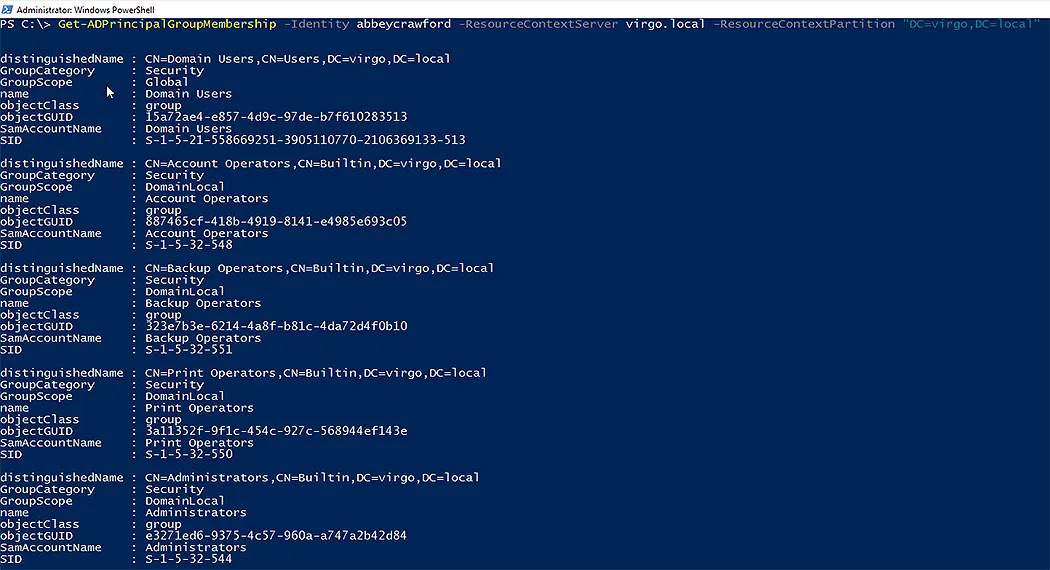
Get the Group Memberships for an Account in Resource Domain
Run the following command using the ResourceContextServer parameter to define the resource domain if you wish to collect every group membership for an AD user account there.
Filter Groups using Get-ADPrincipalGroupMembership
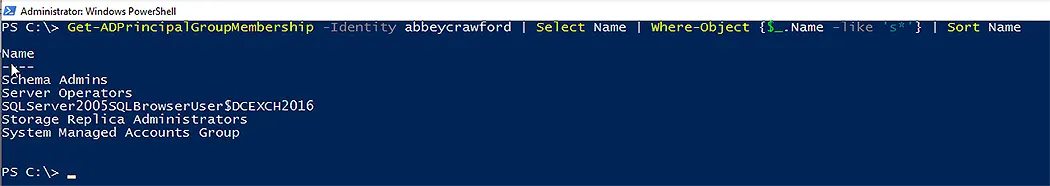
If you want to filter groups returned as membership of the specific user, run the following command:
Get-ADPrincipalGroupMembership -Identity AbbeyCrawford | Select Name | Where-Object {$_.Name -like 'S*'} | Sort Name
In this cmdlet:
- Get-ADPrincipalGroupMembership brings the group memberships of administrator and passes the output to the second command.
- The second command only selects the names of the groups.
- The third command uses the where-object argument to filter the users according to the condition or filter applied.
- The last command sorts the filtered list and displays them in the PowerShell console.
Get Computer Membership Using Get ADPrincipalGroupMembership
With Get-ADPrincipalGroupMembership, you can also get the membership of any computer object by running the following cmdlet:
Get-ADPrincipalGroupMembership -Identity 'CN=DCEXCH2016,OU=Domain Controllers,DC=virgo,DC=local' | Select-Object Name
Here, the Get-ADPrincipalGroupMembership cmdlet gets the membership of the computer object specified in the Identity parameter as a distinguished name, then passes the output to the second cmdlet to be displayed in the PowerShell console.
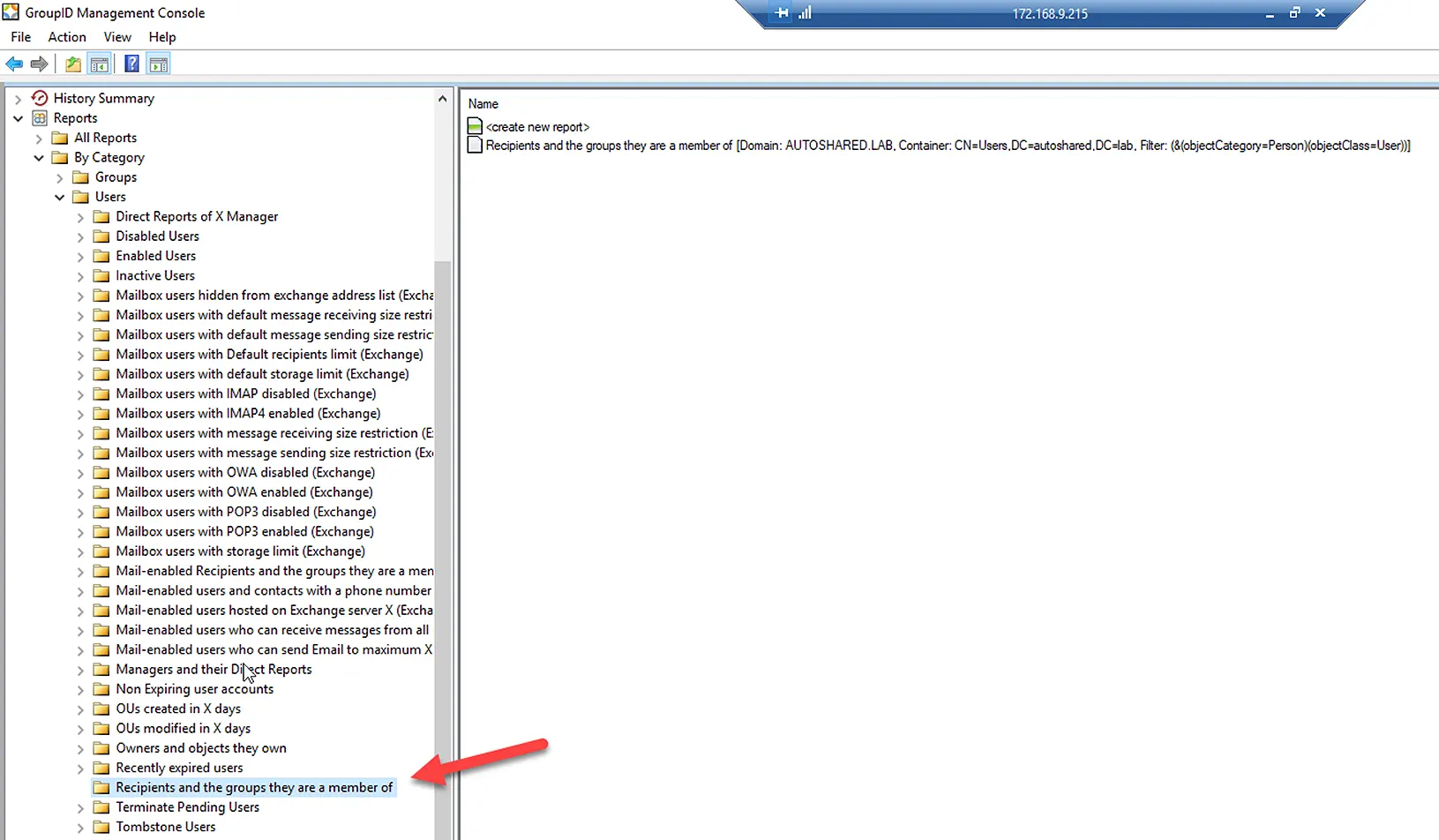
View Memberships using the GroupID Report Module
The GroupID Reports module is a free reporting tool designed to run reports on Active Directory, Microsoft Exchange, and Office 365.
Using it, you can generate the following report to view users and their group memberships.
- Recipients and the groups they are members of
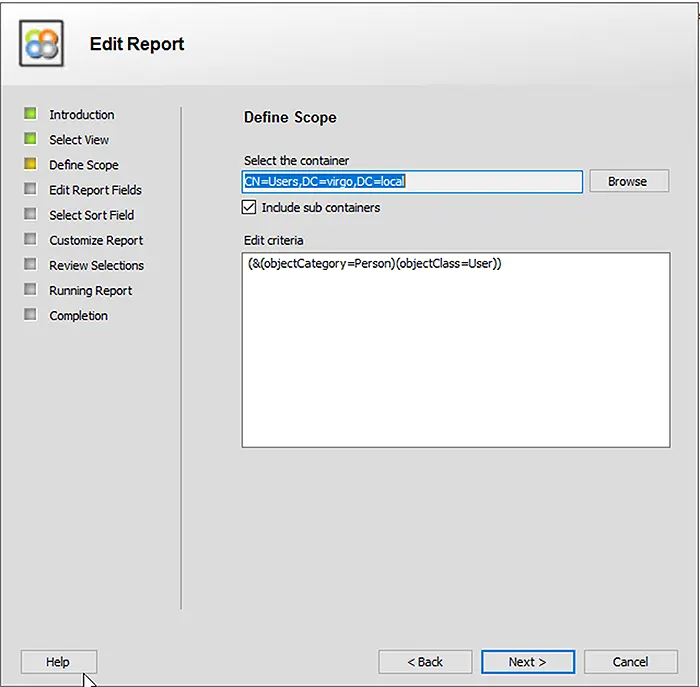
 You can create a report and schedule it to run as required. The report uses the following LDAP query to fetch users and their group memberships from Active Directory:
You can create a report and schedule it to run as required. The report uses the following LDAP query to fetch users and their group memberships from Active Directory:
(&(objectCategory=Person)(objectless=User))
The following screenshots displays some of the attributes/columns displayed in the report. You can add more columns or remove the default ones as needed.
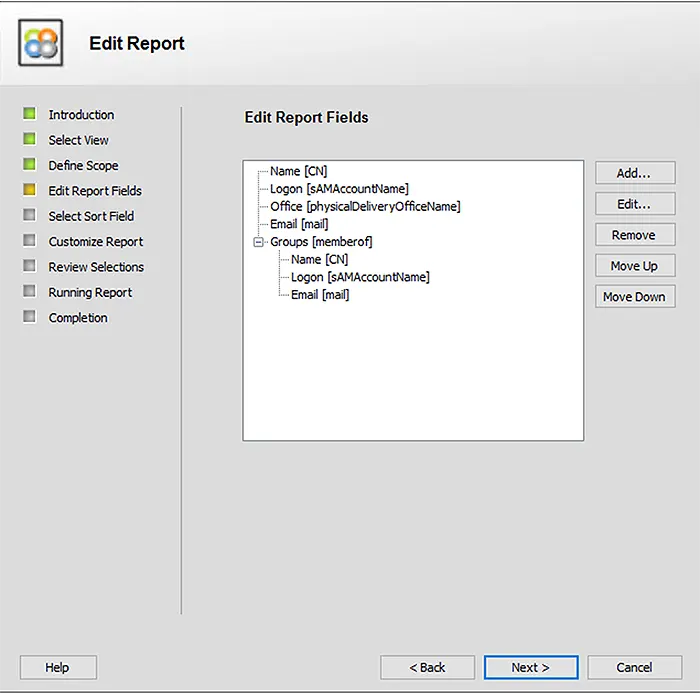
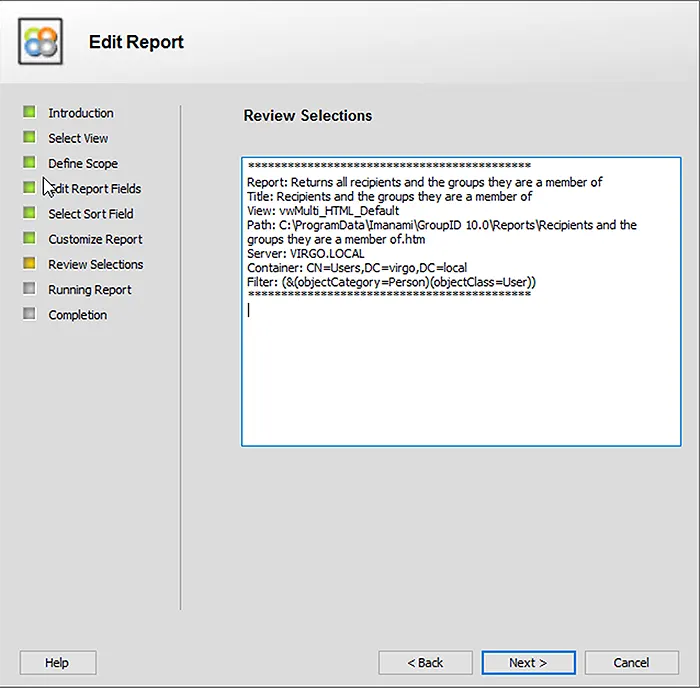
You can review your selections and edit them if you are not satisfied with the query.
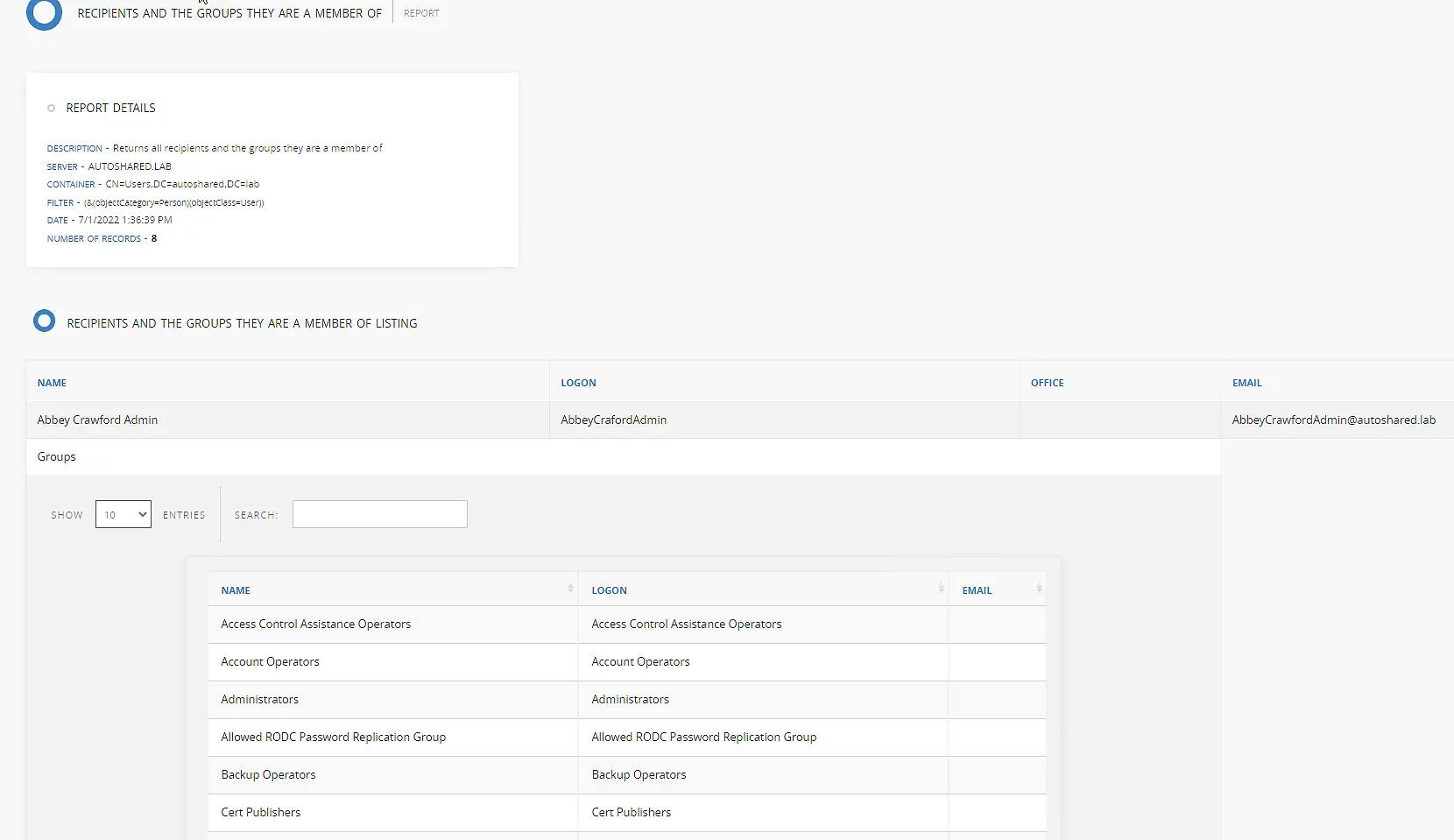
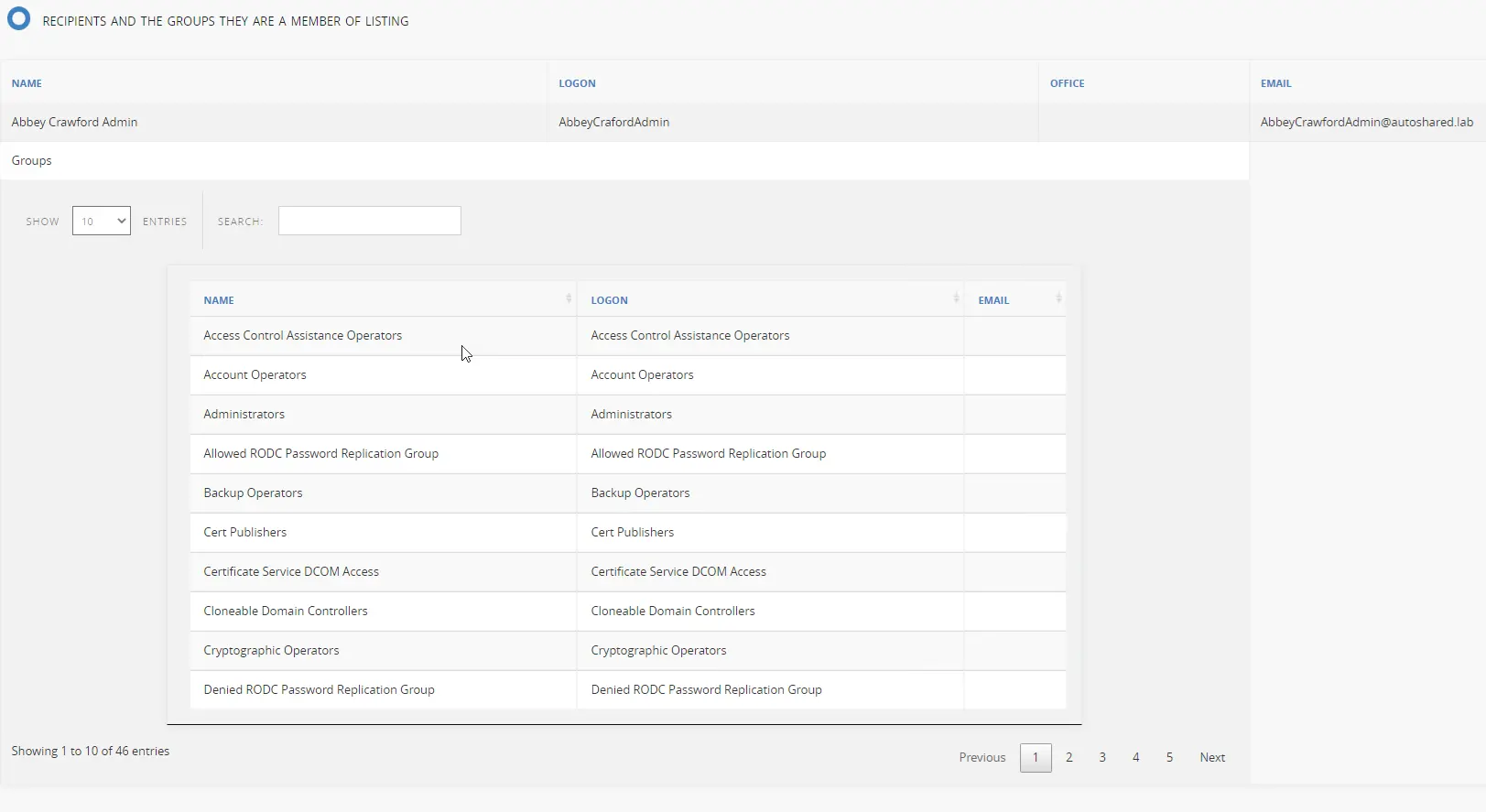
You will get the report as a webpage, as shown below. You can also select the output as an Excel sheet or as XML format.
Conclusion
In this blog, we firstly discussed the traditional ways to get the group memberships of an object. Then we explored the different parameters of Get-ADPrincipalGroupMembership and their uses with examples. We also used the cmdlet to get the membership of a computer object, especially a domain controller. Then we discussed GroupID Reports for the same purpose, thereby showcasing the ease it offers to administrators while saving them from hectic PowerShell cmdlets and scripts.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.

