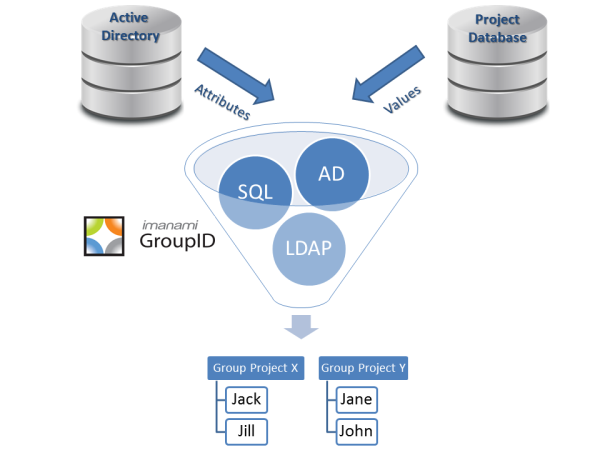
Active Directory and Exchange services enable security groups to manage distribution lists. However, the capabilities around groups owning other groups are limited.
Table Of Contents
- Why Distribution Lists are Managed by Security Groups?
- How Distribution Lists are Managed by Security Groups
- Use Cases for Distribution List Management via Security Groups
- List of Common Group Attributes in Active Directory and Exchange
- Distribution Lists Management by Security Groups Using a Third-Party Application
Before digging down into managing distribution lists by security groups, it is important to answer the following question:
Why Distribution Lists are Managed by Security Groups?
Since distribution lists cannot be used to assign permissions, it makes sense to set security groups as their owners. Besides other things, security group members can easily set authorizations and send/receive message restrictions for a distribution list. Enterprises can benefit significantly by setting security groups as owners of distribution lists.
How Distribution Lists are Managed by Security Groups?
Once security groups are made owners of distribution lists, it enables members in security groups to manage the distribution lists as follows:
-
Manage Memberships in Distribution Lists
The best part of making security groups as owners of distribution groups is that you can have anyone in the security group manage memberships in their respective distribution lists.
-
Define and Update Group Attributes
Group owners can define and update various attributes for a group, provided that your IT team has authorized it.
Use Cases: Distribution Lists Management via Security Groups
- Project teams own various distribution lists.
- Helpdesk users own security groups.
- Anyone In Corporate Communications owns all distribution groups.
- HR Directors and above own certain sensitive security groups.
- Security groups have full access to SharePoint sites.
Let’s take the last use case to elaborate on making security groups with access to SharePoint sites as owners of distribution lists.
Security Groups with Full Access to SharePoint Site
A security group that has full access to a SharePoint site can be set as the owner of a distribution list, where the members of the distribution list have read-only access to that same SharePoint site. In this way, group owners would be aware of any communication between group members.
Common Group Attributes in Active Directory and Exchange
IT admins and group owners can manage attributes for distribution lists in Active Directory and Exchange through:
- Active Directory
- Exchange Administration Center
- Exchange Management Shell
Following are some of the most used attributes for groups:
- ManagedBy
- AcceptMessagesOnlyFrom
- AcceptMessagesOnlyFromDLMembers
- AcceptMessagesOnlyFromSendersOrMembers
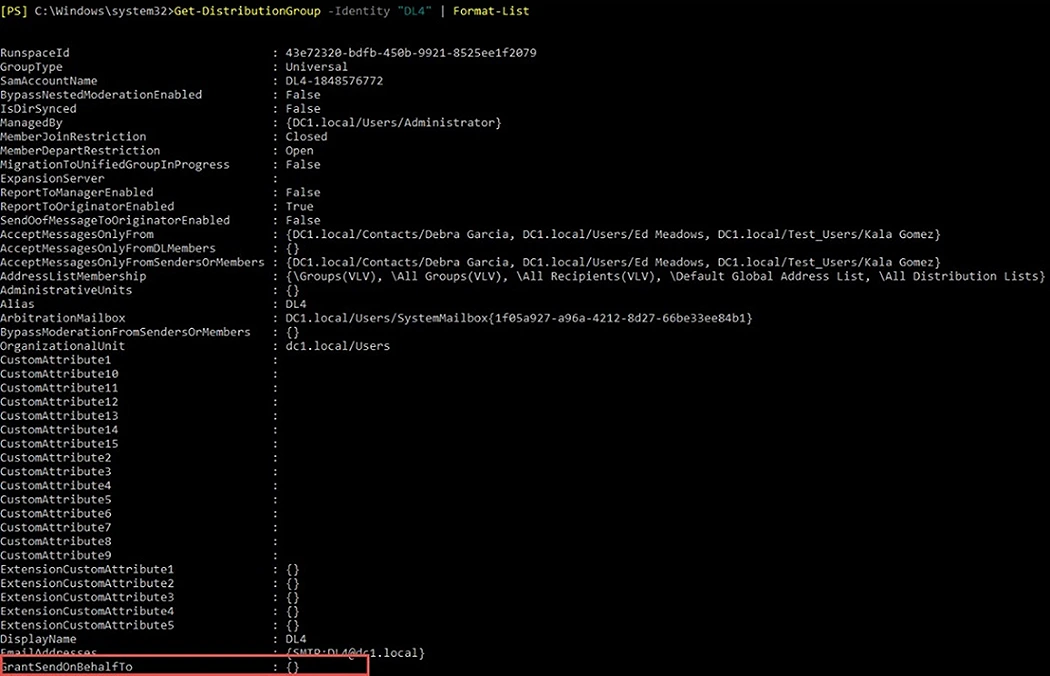
- GrantSendOnBehalfTo
- RejectMessagesFrom
- RejectMessagesFromDLMembers
- RejectMessagesFromSendersOrMembers
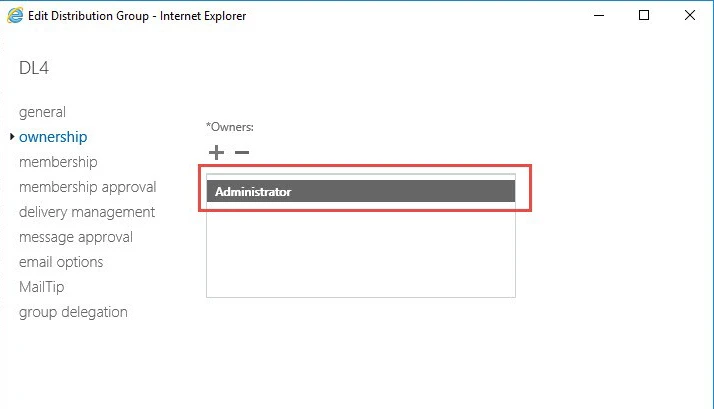
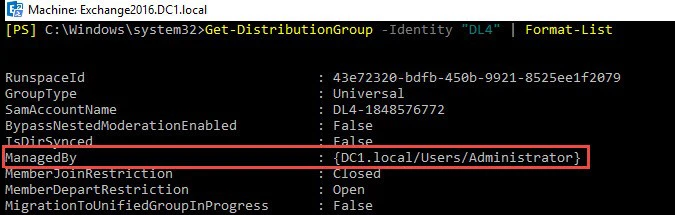
ManagedBy
The ManagedBy attribute enables administrators to set a group owner who can:
- Make changes to the group’s properties
- Add new members and remove old members
- Approve member join and leave requests
- Moderate the content being sent
Prerequisites
- A group must have at least one owner, and if the owner isn’t set, then by default, the person who created the group is the owner with permission to make changes to the group.
- This owner should be a mailbox user or a mail-enabled security group.
The owner can be identified by a unique ID, such as:
- Name
- GUID
- Alias
- Canonical DN
- Distinguished name (DN)
- Domain\username
- LegacyExchangeDN
- SamAccountName
- User principal name
- User ID
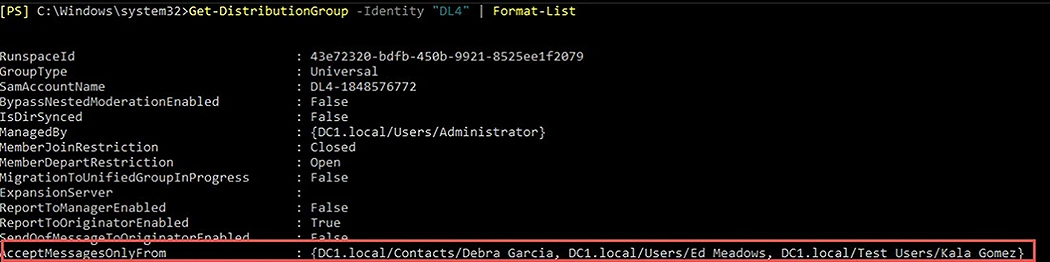
AcceptMessagesOnlyFrom
The AcceptMessagesOnlyFrom attribute allows the members of a distribution list to receive messages from a specific set of users. The users in the specified list can be identified on the basis of a unique ID, such as:
- Name
- GUID
- Alias
- Canonical DN
- Distinguished name (DN)
By default, this attribute is set to null, meaning that messages from all users are accepted.
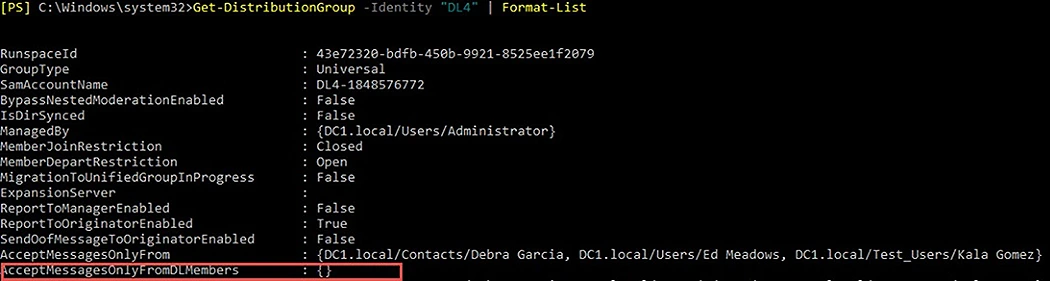
AcceptMessagesOnlyFromDLMembers
The AcceptMessagesOnlyFromDLMembers attribute allows the distribution list to receive messages only from specific groups in your organization (distribution groups, mail-enabled security groups, and dynamic distribution groups). All members of the specified groups can send messages to this distribution list. Senders can be identified based on a unique ID, such as:
- Name
- GUID
- Alias
- Canonical DN
- Distinguished name (DN)
By default, this attribute is set to null, meaning that messages from all groups are accepted.
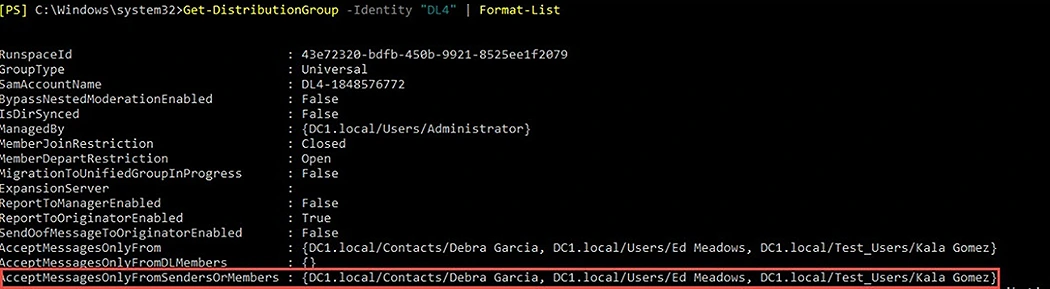
AcceptMessagesOnlyFromSendersOrMembers
The AcceptMessagesOnlyFromSendersOrMembers attribute enables the members of a distribution list to receive messages from specific groups from within the organization and from specified individuals.
Senders can be identified on the basis of a unique ID, such as:
- Name
- GUID
- Alias
- Canonical DN
- Distinguished name (DN)
By default, this attribute is null, meaning that messages from all senders are accepted.
GrantSendOnBehalfTo
The GrantSendOnBehalfTo attribute enables the administrator to choose who can send emails on behalf of the group. This sender should be a mailbox user or a mail-enabled security group.
Senders can be identified on the basis of a unique ID, such as:
- Name
- GUID
- Alias
- Canonical DN
- Distinguished name (DN)
- Domain\username
- LegacyExchangeDN
- SamAccountName
- User principal name
- User ID
When the sender sends on behalf of the group, their name is clearly shown; however, the replies are not sent to the sender but the whole group. By default, this attribute is set to null, which means no one has permission to send on behalf of the group.
RejectMessagesFrom
The RejectMessagesFrom attribute prevents a distribution list from receiving messages from specified users. The users added to the list cannot send messages to the group.
Users in the list can be identified on the basis of a unique ID, such as:
- Name
- GUID
- Alias
- Canonical DN
- Distinguished name (DN)
By default, this attribute is set to null, which means that messages from all senders are accepted.
![]()
![]()
RejectMessagesFromDLMembers
The RejectMessagesFromDLMembers attribute prevents a distribution list from receiving messages from specific groups in the organization. Members of the specified groups will not be able to send messages to this distribution list.
Groups in the RejectMessagesFromDLMembers list can be identified on the basis of a unique ID, such as:
- Name
- GUID
- Alias
- Canonical DN
- Distinguished name (DN)
By default, this attribute is set to null, which means that messages from all groups are accepted.
![]()
![]()
RejectMessagesFromSendersOrMembers
The RejectMessagesFromSendersOrMembers attribute prevents a distribution list from receiving messages from specific groups from within the organization as well as from specified individuals. The objects in the RejectMessagesFromSendersorMembers list can be identified on the basis of a Unique ID, such as:
- Name
- GUID
- Alias
- Canonical DN
- Distinguished name (DN)
By default, this attribute is set to null, which means that all groups and individuals can send messages to this distribution group.
![]()
![]()
Distribution Lists Management by Security Groups Using a Third-Party Application
Independent software vendors like GroupID by Imanami reduce the burden on IT administrators by automating and delegating group management tasks. GroupID’s web-based Self-Service portal enables you to conveniently set security groups as owners of distribution lists. Here are some of the functions that you can perform with GroupID:
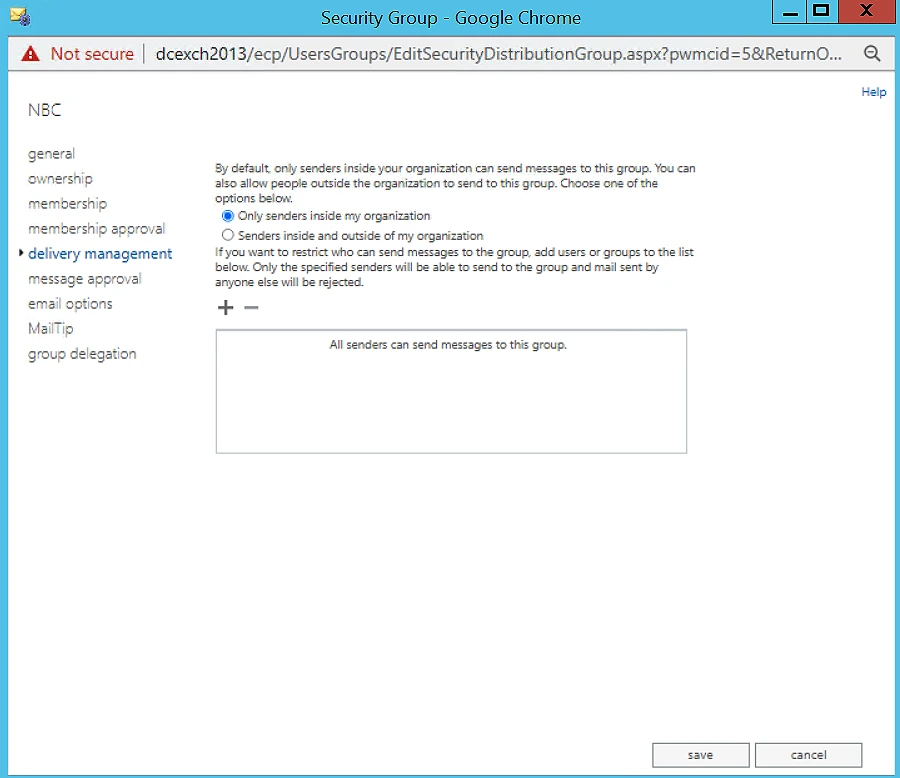
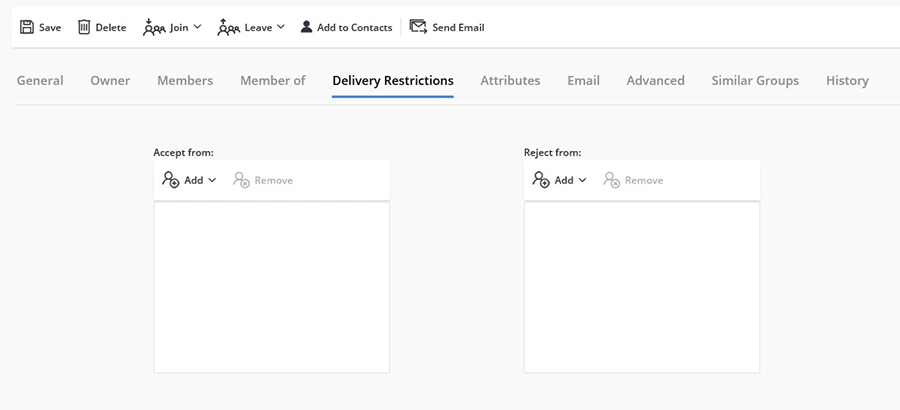
Set Delivery Restrictions
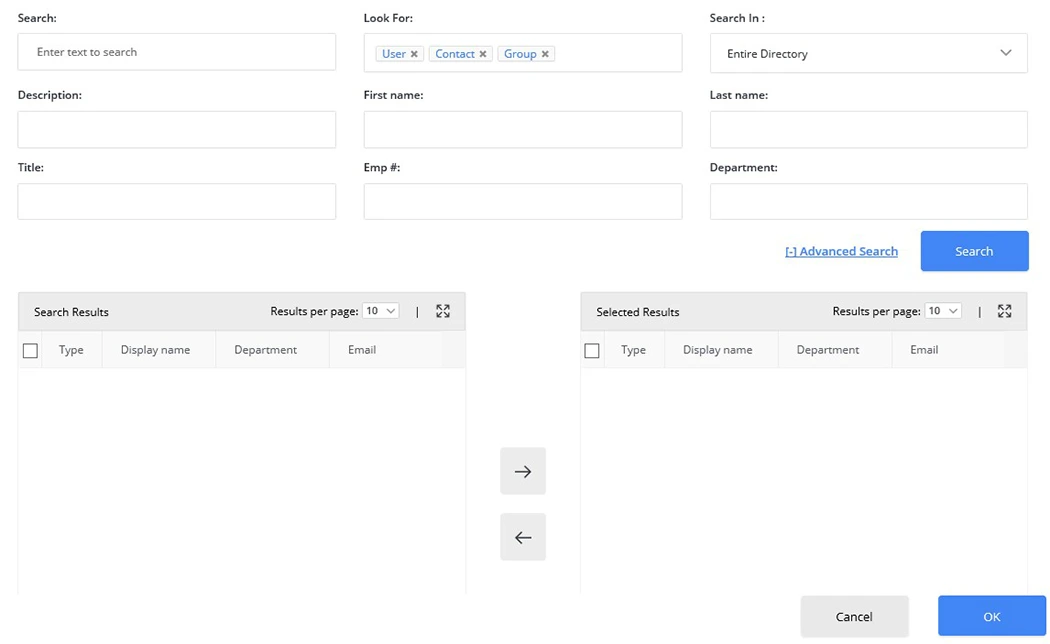
This setting allows you to control who can and cannot send messages to a group. For example, in Group A’s properties, simply add the users and groups that Group A can receive and reject messages from. GroupID also gives you an advanced search option to conveniently search for the desired groups and users.
By clicking Add, you can perform a simple or advanced search. The Advanced Search page is as follows:
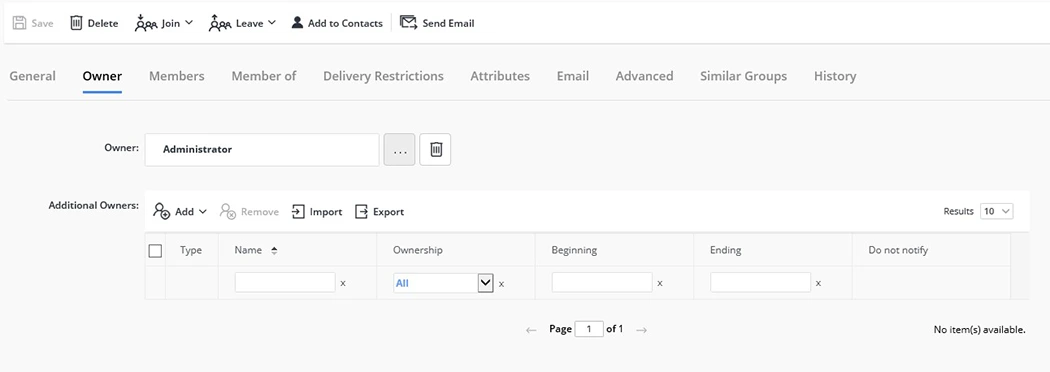
Manage Group Owners
A distribution list can have multiple owners who can be users, contacts, and security groups. In the case of a group, all its members are considered as additional owners with full rights to manage the distribution list.
Enable Delivery Reports:
You can set non-delivery report (NDR) recipients when a message sent to this group is not delivered. The non-delivery report lets the recipient know that the message was not delivered. GroupID gives you three options to choose from:
- Report to Originator: In this option, non-delivery reports are sent to the message originator instead of the group owner.
- Report to Owner: This option sends non-delivery reports to the group owner instead of the message originator.
- Do Not Send Delivery Report: Delivery reports are not sent to anyone.
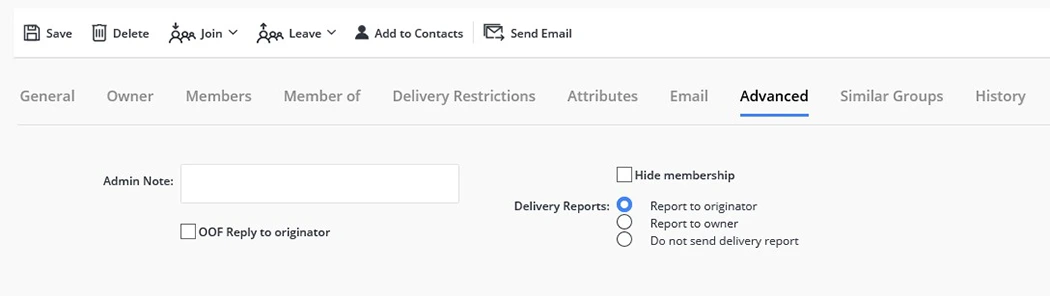
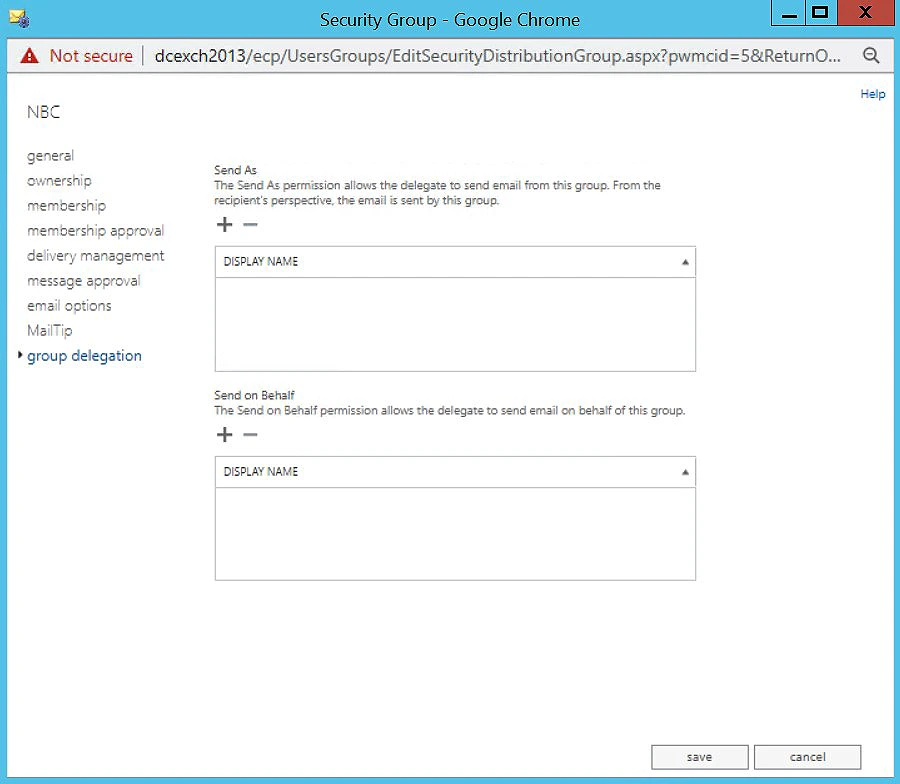
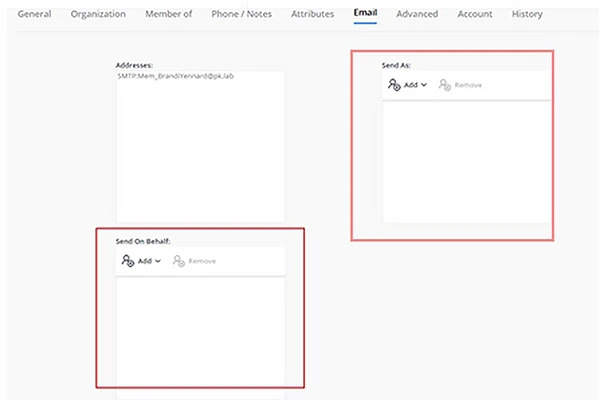
Set the Send as and Send on Behalf Permissions for a Group:
Using the GroupID Self-Service portal, you can set up both the Send As and Send on Behalf permissions for a group.
Group owners and administrators can add objects to the Send As and Send on Behalf lists for a group.
A user who has been granted the Send As or Send on Behalf permissions can send email as the group or on behalf of the group respectively.
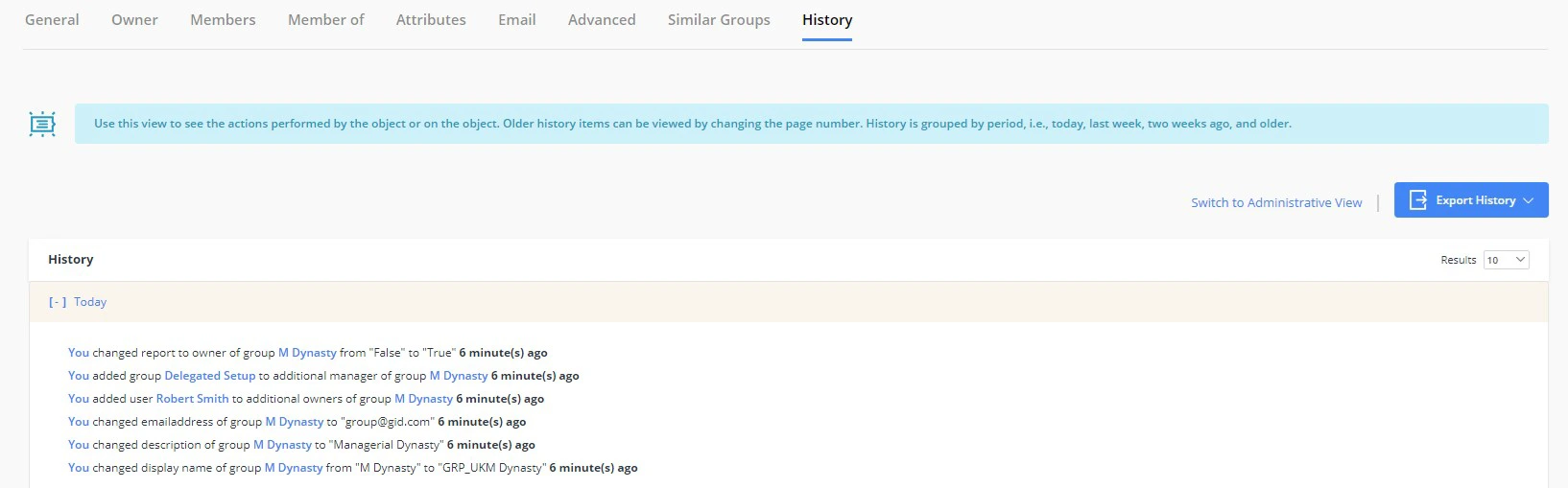
Track History:
GroupID enables administrators and group owners to view all the actions performed on a group since its creation. The History tab in group properties displays history in a tabular and linear layout, along with comments. If the history record spans across multiple pages, you can navigate through them using the buttons at the bottom of the tab. You can also use the Export History button on the page to export history data to an external file, to view it outside of GroupID. Supported formats are MS Excel, CSV, and XML.
GroupID – A Leader in Group Management for 20+ Years
GroupID unlocks several features when you enable a security group to manage a distribution list. It is a one-stop solution for managing groups, allowing IT administrators to delegate Active Directory group management control to users. By using GroupID, you can significantly reduce the overload on your IT department and improve productivity, which is precisely what you need to make your business flourish in this competitive world.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.