In Active Directory, a computer object is a security principal. This means that just as with a user, you can give permissions for resources and assign security group memberships to the computer.
Applying permissions to Active Directory groups, more specifically, Active Directory security groups instead of OUs is a generally accepted best practice. For user objects, you can delegate part of this and automate most of the rest, leaving a small amount of manual work for system admins to perform.
Active Directory stores information in the form of objects. These objects represent resources in the network. They can be Users, Computers, Printers, Shared Folders /Files, Contacts, and many more. Objects in Active Directory are described by a set of information called Attributes.
Let’s explore the computer objects in active directory in detail.
Computer Objects
Computer object represents a computer inside an Active Directory network of an organization. It is categorized as a leaf object, that means a computer object cannot contain any other Active Directory object. Computer objects have mandatory attributes containing information that are computer name, ID, role, description, location, DNA name, operating system version that the computer is running on, Managed By, and more.
Computer Objects as Security Principle
Like user objects, computer objects also act as a security principle i.e., they must have a username and password to connect to a domain. Security principles are basically an entity that can be authenticated by the system. They are assigned permissions and can be used to manage access to certain network resources.
Each computer is assigned a unique identifier called SID along with GUID that it retains for its entire lifetime. Computer accounts identify and manage Windows-based clients that are members of the domain. They determine access rights to these clients’ computers participating in Active Directory data base. System administrators manage security settings and can place restrictions on a certain computer to increase security.
Creating Computer Objects in Active Directory
There are several ways to create computer objects in active directory. Administrators consider different factors before choosing which tool is better to create computer objects.
Following are the four ways to create computer objects.
- Active Directory Users and Computers (ADUC)
- Active Directory Administrative Center (ADAC)
- Dsadd.exe
- PowerShell
Creating Computer Objects by ADUC
To create a computer object, launch Active Directory Users and Computers console in Windows server 2016.
To do this, follow the below mentioned steps.
- Open Server Manger and select Tools from top-right menu. Select Active Directory Users and Computers from the drop-down list.
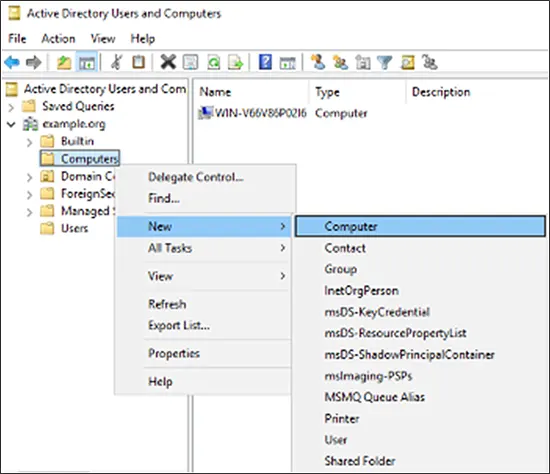
- In the left pane, expand the domain. Right click on the computer container and select New > Computer.
- New Object – Computer wizard opens. Enter the Computer name.
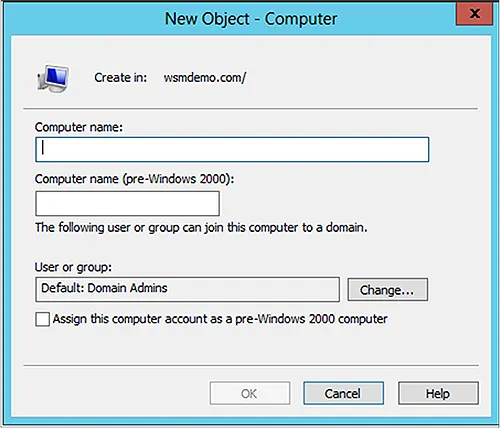
- The Computer name (pre-Windows 2000) will auto-populate to match the name.
- In the User or group field, change the user or group that the computer should be a part of. Click Change and search for the user or group to give access to the computer.
- Click OK.
Creating Computer Objects by ADAC
To create computer objects in the ADAC, select Active Directory Administrative Center from the list as shown in Figure 1.
Follow the following steps:
- Launch ADAC.
- Select the OU or container in which you want to create the computer object. For example, Computers.
- Chose New from the task list and select Computer.
- Create Computer wizard opens.
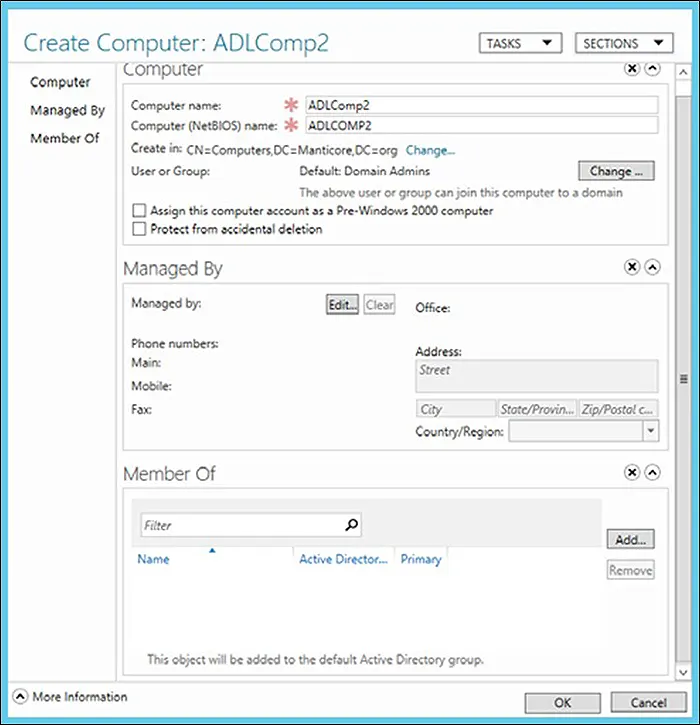
- Add the Computer name. Computer (NetBIOS) name automatically fills based on the name.
- Select the checkbox Protect from accidental deletion.
- Click Change to select the User or Group that can be the part of domain.
- Add computer manager in the Managed By section if required. To do that, click Edit.
- To add the computer in any group, click Add in Member Of section if required.
- Click OK.
Creating Computer Objects by using Dsadd.exe
Many administrators prefer using a command line while creating multiple objects. Dsadd.exe enables them to create multiple objects in just a single command. They create a batch file of Dsadd.exe commands that generate multiple objects in a single go. The syntax for creating computer object is:
dsadd computer <ComputerDN>
The <ComputerDN> parameter represents the name of the new computer object that this command generates.
Creating Computer Objects by using Windows PowerShell
Other than ADAC, ADUC and Dsadd.exe, Windows PowerShell also helps in creating objects. The cmdlet New-ADComputer creates computer objects. The syntax is as follows:
new-ADComputer -Name -path
This creates computers but does not allow them to join domain.
Properties of Computer Objects
Properties define an object and are also called object attributes. Each object has a set of attributes assigned to it in Active Directory. Some of the common attributes that define a computer’s properties are:
| Attributes | Description |
|---|---|
| Name | Name assigned to computer object |
| Location | Shows location of the computer object |
| Member Of | Lists OUs or groups this computer is a member of |
| Description | Read only text describing the computer object. |
| Managed By | Shows details about user who manages that computer. |
Among these attributes, there are some that must have a value. These mandatory attributes are as follows:
- cn: It is the unique name assigned to the computer object to distinguish it in Active Directory network.
- SAMAccountName: This is also a naming attribute. It uniquely identifies the computer object in Active Directory network.
- ObjectCategory: It represents the distinguished name of the object class that the computer object belongs to, or name of one of its superclasses
- ObjectClass: It is a single value property that contains unique name of the object class that the computer object belongs to.
Management of Computer Objects
User can modify the attributes of computer objects through ADUC and PowerShell.
Modifying Computer Objects via ADUC
Follow the following steps:
- Open ADUC console and locate the computer object to modify.
- Right click on the computer object and select Properties from the menu.
- Computer Object Properties dialogue box with several tabs opens.
- Navigate through the tabs and make required changes.
- Apply the changes and then click OK.
Modifying Computer Objects via ADUC
In PowerShell, the Set-ADComputer cmdlet modifies computer objects in Active Directory. This cmdlet modifies the commonly used property values. Property values not associated with cmdlet parameter are updated using Add, Remove, Replace, and Clear parameters.
For example: If you want to set the location of a computer that is specified by Identity parameter, use the following command.
Set-ADComputer -Identity "USER02-SRV1" -Location "NA/HQ/Building A"
You can also modify multiple attributes of a computer using Powershell.
For example: To modify location and Managed By attribute of a computer, use the following command.
$Comp = Get-ADComputer -Identity "USER04-SRV1" $Comp.Location = "NA/HQ/Building A" $Comp.ManagedBy = "CN=SQL Administrator 01,OU=UserAccounts,OU=Managed,DC=USER04,DC=COM" Set-ADComputer -Instance $Comp
Moving Computer Objects
The default location for newly created computer objects is CN = Computers Containers. The standard AD location “Computers” is not OU object. Hence, it cannot be linked to any group policies.
To place the newly created computer objects in relevant OUs with group policies, modify their default location. Modification of default location for new computer objects can be done in Windows Server 2003 and above.
If the required OU does not exist, create the OUs where you want to place the computers that you created. At the command prompt, run Redircmp.exe by using the following syntax:
redircmp container-dn
CONTAINER-DN is the name of the OU where you want to redirect the newly created computer object.
While moving a computer object,
- The permissions assigned to the moving object move with it.
- The moving object inherits permissions and group policies from its new location. Policies and permissions inherited from the previous location do not move with the moving object.
Deleting Computer Objects
In ADUC, locate the computer you intend to delete. Right click on the computer and select delete. Since there is no Undo option, it will confirm the deletion process before permanently deleting the computer object.
Once a computer object is deleted, it is no longer part of the domain. If you recreate the computer object, it will not have the permissions and memberships of the old one.
Resetting Computer Objects
If a computer’s secure channel fails, the administrator needs to reset the computer account. In ADUC console, locate the computer object in appropriate container. Right click on that computer object and then select Reset Account. The reset will break the computer’s connection to the domain and will require it to join again.
Computer Objects in Security Groups
Active Directory Security Groups are objects placed in a container in Active Directory. These groups have an attribute called Members that lists the objects that are members of a particular security group. These objects can be User accounts, Computer accounts, Service accounts and other groups. Windows operating systems have several built-in security groups that are assigned appropriate permissions and rights. You can also create additional security groups with a unique set of security requirements.
Computer object is a security principal. This means you can give permissions for resources and assign security group memberships to the computer. There are several computer objects attributes that you can query to make dynamic groups whether it be department, company, OS, last login, etc. Some of the filters are do-able at the GPO level but some make more sense just to have accurate group membership.
Once you have the group membership accurate, it’s easy to start offering different IE settings based on department (less restrictions on one department vs another), or software installation based on department (PowerPoint for sales, VSTS for engineering), or even based on location (no proxy setting for home offices).
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.

