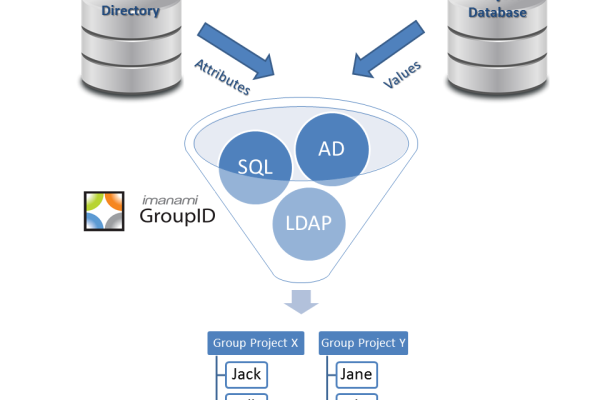
How to Avoid Flaws in Identity Management
David Bell wrote an interesting piece in Secure Computing on how to avoid flaws in Identity Management. The part that I really liked was how he pointed out that the IT security industry is focusing its efforts on “where” enterprises keep their critical data instead of “who” has access to it. It is this “who”…