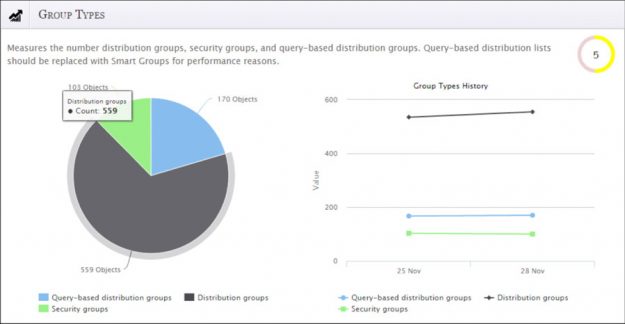
3 Steps to Better Group Management
Group management in Active Directory is so much more than just making sure that memberships are correct. There’s an entire lifecycle process devoted to improving the management of groups — and the security they represent. But for many of you, there simply isn’t enough time (yet) to devote to implementing an entire group lifecycle. So,…