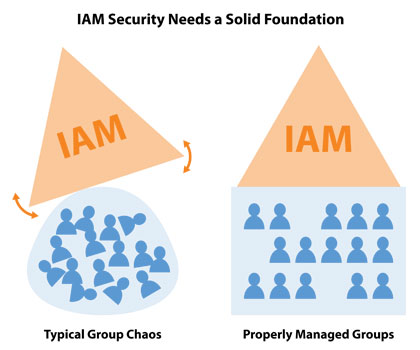
The Role of Group Management in PAM Strategy
Privileged Account Management (PAM) is a key part of any security strategy. For those of you who may not be familiar with it, PAM focuses on improving the security of privileged accounts and providing more controlled access to those accounts — from an account with Enterprise Admin rights all the way down to an account…