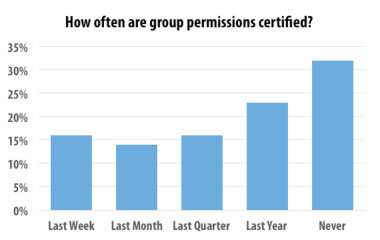
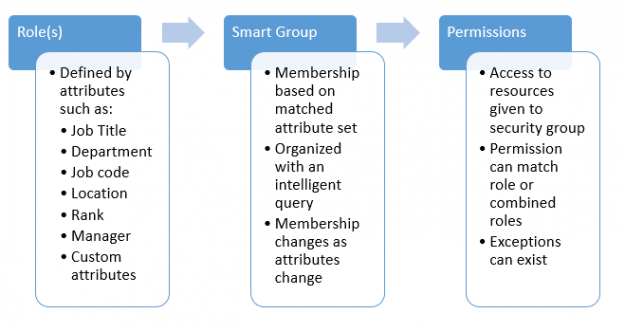
The State of Active Directory Groups: Confusion, Chaos, or Control
If you’re like most IT professionals, after a group is created, you never really give that group a second thought. Once you go to the Members tab, add a user or two, and press OK, you don’t look back. It makes sense — it’s just groups, right? I mean, who cares? Perhaps the better question…