Have you ever wondered how different groups of people in an organization can access a different set of resources and information? How are some people eligible to execute certain processes in the IT team while others are privileged to use the CRM application? Security groups in Active Directory make this happen.
Network administrators assign privileges and access to users and computers using Active Directory security groups, which is why you can never compromise on AD security. To help you improve the safety of your organization’s data and assets, this article discusses the best practices for maintaining Active Directory security groups – because precaution is always better than cure.
Table Of Contents
- What are Active Directory Security Groups?
- Why should Active Directory groups stay secure?
- Active Directory Security Groups Best Practices
- Use Group Nesting to Simplify Access Management
- Avoid Using Redundant Names for Security Groups
- Keep Permissions at a Bare Minimum
- Users Should Not be Members of Unnecessary Groups
- Keep Track of Group Activity and Changes
- Service Accounts Should be Properly Configured and Locked
- Remove All Inactive User Accounts
- Implement Strong Password Policies
- Utilize a Password Solution Tool
- Use a Secure Admin Workstation for Administrative Tasks
- Have Multiple Accounts
- Inspect Security Using MS Secure Score
- Always Create a Recovery Plan
- How to Enhance the Protection of Active Directory Security Groups?
What are Active Directory Security Groups?
Active Directory Security groups are used to delegate user rights and assign permissions on shared resources. Rather than setting up rights and permissions for individual users, administrators should assign them to security groups once and then add members to groups. Each member is entitled to the rights and permissions assigned to that group.
Why should Active Directory groups stay secure?
Active Directory groups such as security groups should be always protected with clear security protocols because they govern user and computer access to resources that could be highly confidential, sensitive, and critical to the organization. Any oversight may result in security breaches and data theft with lasting consequences.
Read More: Zero Trust Security in Active Directory and Azure Active Directory Groups
Active Directory Security Groups Best Practices
Owing to the sensitivity of security groups, they need to be secured by implementing the following best practices:
- Use Group Nesting to Simplify Access Management
- Avoid Using Redundant Names for Security Groups
- Keep Permissions at a Bare Minimum
- Users Should Not be Members of Unnecessary Groups
- Keep Track of Group Activity and Changes
- Service Accounts Should be Properly Configured and Locked
- Remove All Inactive User Accounts
- Implement Strong Password Policies
- Utilize a Password Solution Tool
- Use a Secure Admin Workstation for Administrative Tasks
- Have Multiple Accounts
- Inspect Security Using MS Secure Score
- Always Create a Recovery Plan
Use Group Nesting to Simplify Access Management
When we talk about group nesting, we refer to making an AD group a member of another group. This strategy enables us to give permissions across domains through universal groups. It works this way:
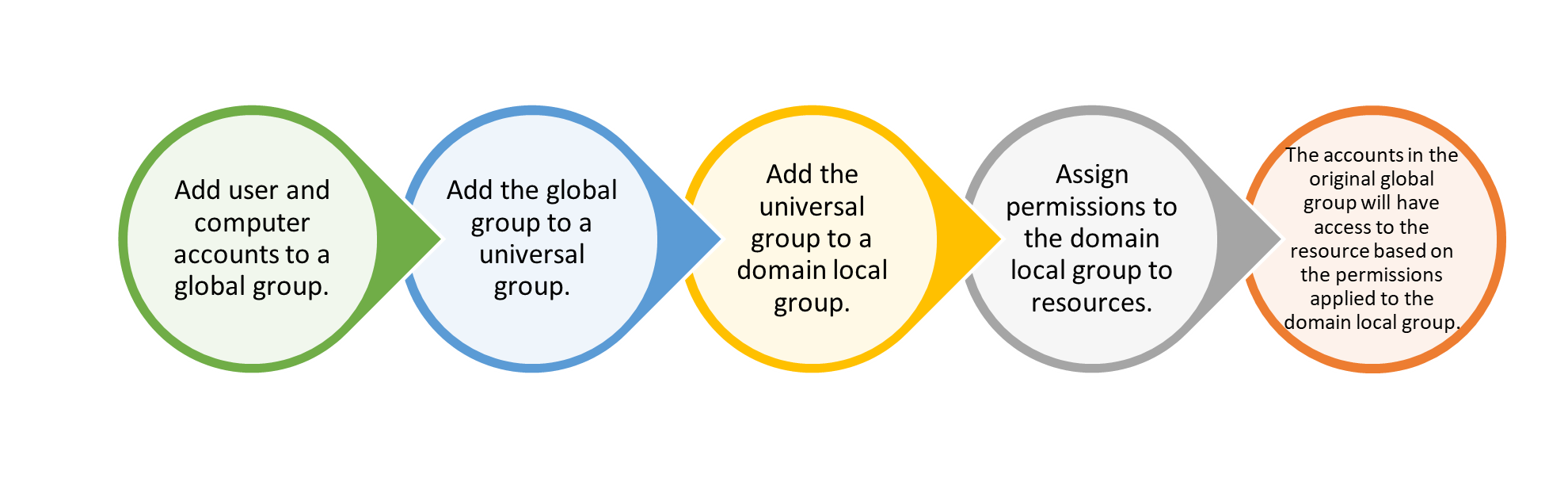
Avoid Using Redundant Names for Security Groups
Not only can this be confusing, but it can also lead to a breach in security when IT admins are not aware of multiple groups falling under the same name. For example, if a series of security groups are called ‘Sales Data 1’, ‘Sales Data 2’, and so on, the group’s purpose is not clear. Active Directory group naming conventions should be followed, and groups should be named according to their scope or purpose.
Keep Permissions at a Bare Minimum
It is easy to give access; however, it is difficult to maintain security after doing so. Group owners should be aware of group members and the level of rights and permissions the group has. Keep a check on permissions, as users do not need to have complete control and access to the system. After all, excessive permissions and elevated privileges may lead to insider privilege abuse and network vulnerabilities.
Evaluate the tasks that group members have to accomplish, then assign the minimum possible rights and permissions to the group.
Users Should Not be Members of Unnecessary Groups
Avoid adding users to groups they do not need to be a part of. Removing unnecessary users makes groups easier to manage. For example, if a user’s department changes, they should be removed from the previous department’s group before becoming a member of the new department’s group. This way, the user only has access to the required resources, and the security aspect of the organization remains intact.
Keep Track of Group Activity and Changes
AD groups should be monitored at all times and audited periodically to prevent malicious attacks. Especially default security groups, such as Domain Admins and Enterprise Admins, need to be examined closely. Suspicious behavior can be detected by looking out for the following:
- Unauthorized permission and membership changes to security groups
- Unnecessary or unusual use of admin accounts
- Failed password attempts
- Locked out accounts
- Disabled antivirus software or removal of the antivirus software
Collect all logs on a server and use a log analyzer to generate reports to spot unusual activity. Setting up real-time alerts on changes to security groups is also a great way to counter threats before they take root.
Service Accounts Should be Properly Configured and Locked
A service account is a special user account that is explicitly created to run a particular application or service on the Windows OS. More often than not, these service accounts have a password that is set to ‘never expire’, while these accounts are loaded with various permissions and access to resources. Therefore, service accounts should be properly configured and locked with strong passwords. The best way to manage service accounts is to:
- Set secure passwords
- Do not assign service accounts in built-in privileged groups
- Do not give admin rights
- Grant minimal access to only what is required to be accomplished through the service account
Remove All Inactive User Accounts
As per the regulations set by CIS, dormant accounts should be disabled or deleted after around 45 days of inactivity. You should set up a system to distinguish inactive accounts from active accounts. This will prove helpful in removing inactive accounts from security groups. Hackers can easily target unused accounts since no one keeps track of the account’s activities. And if that unused account is a member of multiple security groups, the implications could be devastating.
Implement Strong Password Policies
Eight-digit codes are no longer safe because, in today’s time, hackers have access to readily available lists with millions of passwords that permit them to crack the system easily. Instead, enforce:
- Twelve-digit passwords
- Use passphrases
- Implement multifactor authentication
- A lockout policy after five failed attempts.
Remember, longer passwords are harder to crack and are more secure.
Utilize a Password Solution Tool
LAPS (Local Administrator Password Solution) is a Microsoft tool that enables IT to set unique, one-of-a-kind passwords for local administrator accounts and store them in Active Directory for ease of access. This is a quick and automated process, and the passwords are difficult to crack.
Use a Secure Admin Workstation for Administrative Tasks
Administrative tasks should be performed on a secure admin workstation (SAW). Regular workstations are more helpless against cyberattacks, fraudulent websites, and keylogging devices. Using a SAW ensures enhanced security against hackers and viruses from both inside and outside the system.
Have Multiple Accounts
Even if you have a privileged account with all admin rights, avoid using it at all times. Instead, use a regular account to perform tasks that do not require admin permissions. By using a regular account, you can eliminate the risk of a virus attack. For instance, if you are checking your email, you can unknowingly download a virus. And if you are doing so from your admin account that is also a member of security groups, a lot of credentials and classified data can be accessed through the attack.
Inspect Security Using MS Secure Score
Microsoft Secure Score is a tool that inspects your organization’s security settings and activity in Microsoft 365. Following the inspection, it gives a security score that reflects your strength in terms of security and protection. Use this tool to measure security and improve it.
Always Create a Recovery Plan
Despite keeping security intact, data breaches may happen at times due to an error. As a proactive measure, it is best to have a recovery plan in place with due attention to recovering security groups. IT teams must be trained to handle such a situation with quick and intelligent decision-making.
How to Enhance the Protection of Active Directory Security Groups?
To improve the overall security of your organization, we highly recommend using a solution like GroupID, which helps you monitor and manage your Active Directory security groups on a constant basis. Here are some of the functions that you can perform on security groups through GroupID:
- Apply Group Naming Best Practices
- Use LDAP Queries to Determine Security Group Memberships
- Identify Inactive Users through User Profile Validation
- Implement Strong Password Policies
- Attest to a Security Group’s Existence
- Set the Expiry of Security Groups
- Enable Group Expiry Notifications
- Set a Default Group Approver
Apply Group Naming Best Practices
It would be great to have security groups with logical, identifiable names that give a clue to the group’s scope and purpose. GroupID helps implement consistency and convention in group names with the following features:
- Group names prefixes
- Regular expressions
- Templates to name nested child groups
- Blocked words list
Read More: Active Directory Group Name Examples & Best Practices
Use LDAP Queries to Determine Security Group Memberships
Security group membership is a sensitive matter and manual management, which often falls prey to delays and mistakes, could jeopardize your organization’s security.
GroupID innovates group membership management with LDAP queries. Define a query for a group and rest assured that membership is always up-to-date with objects that meet the criterion laid out in the query. Hence, security groups have just the needful members; no more, no less.
Identify Inactive Users through User Profile Validation
Maintaining an organized Active Directory is an essential part of creating a secure environment, and to do so, you need to identify and clean up inactive user accounts. GroupID’s User Profile Validation feature offers one of the best possible ways to identify inactive accounts. IT administrators can force users to validate their profile after a specific period of time (e.g., 1 week, 1 month, or any other frequency) to ensure that the account is still in use. If a user account is not validated within the set timeframe, the account is locked and marked as inactive.
Implement Strong Password Policies
Passwords are the first line of defense against threats and intrusions. Therefore, always implement a strong password policy to ensure that your system is safe and secure from prying eyes. GroupID aids password management by enabling IT admins to:
- Specify restricted passwords to prevent users from setting easy passwords.
- Define regular expressions for allowed passwords.
- Specify disallowed passwords using an external file.
- Set password validation checks that vary for roles. In this way, you can have stricter password requirements for admin accounts.
- Set a password expiry date.
Attest to a Security Group’s Existence
Group attestation is an added benefit that comes with GroupID. This feature enables group owners to review and certify some key aspects of a security group: attributes, membership, permissions, and existence. A group that fails attestation is an unnecessary group that can be expired and deleted.
Set the Expiration of Security Groups
Group expiration is a very useful feature in GroupID as it enables group owners to expire groups when they are no longer required. An expired group is locked for all the activities and its permission are no longer applicable. For security groups, GroupID distinctly lets you choose between expiring and not expiring them.
- As projects end, the accompanying security groups may also need to be dismantled so that access is revoked when not required anymore. You can set an expiry date for a security group accordingly.
- Groups that are expired and deleted by GroupID can also be conveniently restored.
- Certain security groups, such as the default security groups in Active Directory, should live forever. You can apply certain configurations to them, so that they skip expiry.
Enable Group Expiration Notifications
GroupID sends out email notifications to group owners 1 day, 7 days, and 30 days before the expiration of a security group, thereby providing them a chance to renew the group. If the group is not renewed, GroupID safely expires and then deletes it. In this way, the group cannot remain a threat.
Set a Default Group Approver
You can designate a default approver for groups in GroupID. For groups without owners, group expiry notifications are sent to the default approver. In this way, no group is left unattended.
Summing Up
Consistent group permission audits always contribute to a secure network. So, stay one step ahead in protecting your organization’s data by implementing the aforementioned best practices for managing Active Directory security groups.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.

