Group nesting in Active Directory simplifies network management for administrators. It enables them to assign access rights and permissions to resources within the domain and across domains with ease. However, due to the various types of groups and their scope in Active Directory, group nesting can get confusing at times. Therefore, it is important to understand the concept of nesting groups, the types of groups in AD and their scope of nesting, and the best practices to observe when nesting.
Table Of Contents
What is Group Nesting?
Group nesting in Active Directory is the process of planting one group inside another group. Active Directory Nested groups inherit all the permissions and privileges of the group that they are planted in. Nevertheless, it is important to note that not all groups can be nested into other groups because it depends on the type of group and its scope of nesting.
How to Nest Groups in Active Directory
Here is how you can nest a group into another group in Active Directory.
- Open the Active Directory Users and Computers console.
- Select the group that you want to nest inside another group.
- Right-click the group and go to Properties.
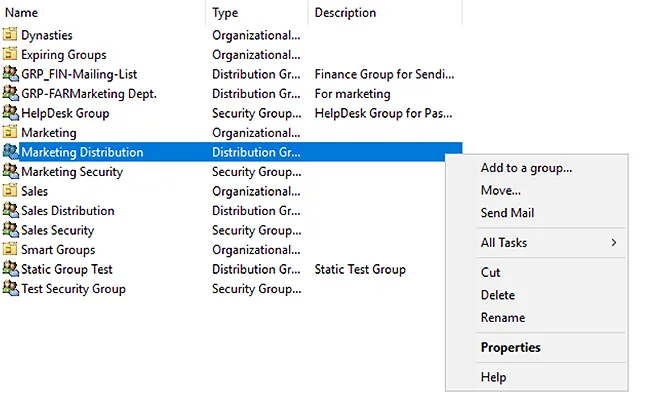
- Go to the Member Of tab in group properties.
- Click Add to search for the group in which you wish to plant this group.
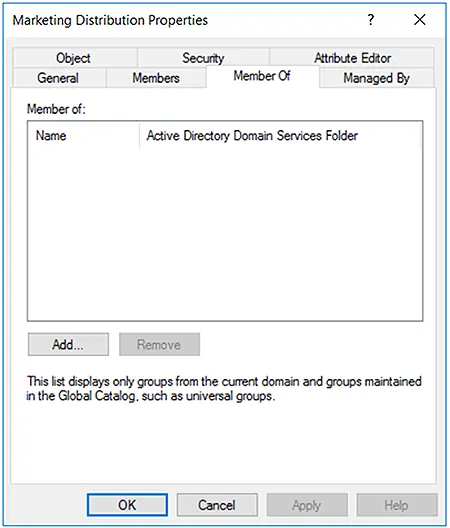
- You can search for the group by typing in a name and then clicking on the Check Names button.
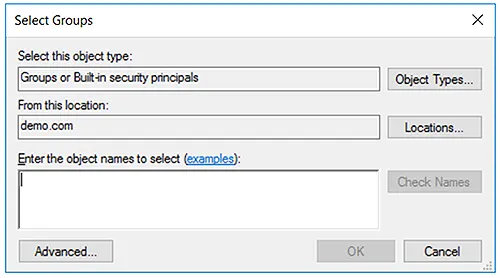
- Select the group from the list and click OK.
- Now, the Member Of tab will show the group you just selected.
- Click OK.
The group is now successfully nested in the desired parent group.
Nesting AD Groups based on Scope
Nesting of Domain Local Groups
- Domain local groups can be a member of another domain local group that resides in the same domain.
- Users and computers can also become members of domain local groups.
- You can also nest local groups containing users or computers of other domains by using a trusted domain of the same forest.
Nesting of Global Groups:
- Global groups can become members of other global groups that reside in the same domain.
- Users of the same domain can also become members of global groups.
- Global groups can become a member of domain local groups in the same domain.
- It is also possible to nest users, computers, and domain local groups in global groups through a trusted domain of the same forest.
Nesting of Universal Groups:
- Universal groups can contain users, global groups, and other universal groups from any domain in the forest.
- They can be a member of domain local groups or other universal groups.
Best Practices for Nesting Groups in Active Directory
When nesting groups in Active Directory, you must adhere to some of the best practices:
Best Practice No. 1 – When Users are Part of the Same Domain
If users are part of the same domain, you can nest groups by:
- Adding user and computer accounts to global groups
- Adding global groups to domain local groups
- Granting the domain local groups access to resources
- Assigning permissions to domain local groups for appropriate access
Best Practice No. 2 – When Users are Part of Multiple Domains
If users are part of multiple trusted domains, you can nest groups by:
- Adding user and computer accounts to global groups
- Adding global groups to universal groups
- Adding universal groups to domain local groups
- Assigning permissions to domain local groups for appropriate access
The Risks of Active Directory Nested Groups
As beneficial as it is, group nesting can also swirl out of control if not managed correctly, creating a wild mess in your directory. For large organizations, the unwieldy disaster of groups caused due to nesting may result in losing grip on who has access to what, ironically the exact reason you are nesting groups in the first place.
Quite often, users in your directory need access to resources on a temporary basis and after their task is accomplished, access should be revoked immediately for security reasons. However, due to the complexity of nested groups, the IT department is usually reluctant to make such changes in the directory. Such dereliction of duties can become insider threats to the organization, resulting in the loss of crucial data and information.
To overcome the challenges posed by nested groups and to cater to their complexities, you need a third-party tool that significantly reduces security risk and improves the overall management of your Active Directory groups. This is where GroupID comes in with its powerful feature of Dynasties that help you create and manage nested groups based on your organization’s hierarchy.
Active Directory Group Nesting with GroupID Dynasties
GroupID, with its proactive approach towards building nested Active Directory groups, adds intelligence by using Dynasties. The concept of Dynasties is based on the nesting of groups in keeping with the hierarchal nature of your business. The groups that a Dynasty creates are called child groups, which become members of their respective parent Dynasty.
GroupID offers three types of Dynasties:
- Organizational Dynasty
- Geographical Dynasty
- Managerial Dynasty
In addition to this, It also offers a custom Dynasty template where you can set your own attributes to create child groups.
Organizational Dynasty
An Organizational Dynasty creates Active Directory groups based on business companies, departments within a company, and job titles within each department.
Geographical Dynasty
A Geographical Dynasty creates Active Directory groups based on country, each state within a country, and each city within a state.
Managerial Dynasty
A Managerial Dynasty creates Active Directory groups based on direct reports of each manager and sub-level manager in a company.
Nesting Active Directory Dynamic Groups
Dynamic groups created in Active Directory using GroupID can dynamically maintain their memberships based on rules set by the administrator. These rules are applied in the form of a user-defined LDAP query. This query is defined once and scheduled for membership update using a Dynamic Group Update job. When this job runs, it applies the defined rules to renew the group’s membership. This way, Dynamic Active Directory groups are auto-updated whenever the directory information changes, making group management for administrators incredibly easy as they no longer have to add or remove members manually.
The Query Designer in GroupID enables you to define queries for fetching group memberships.
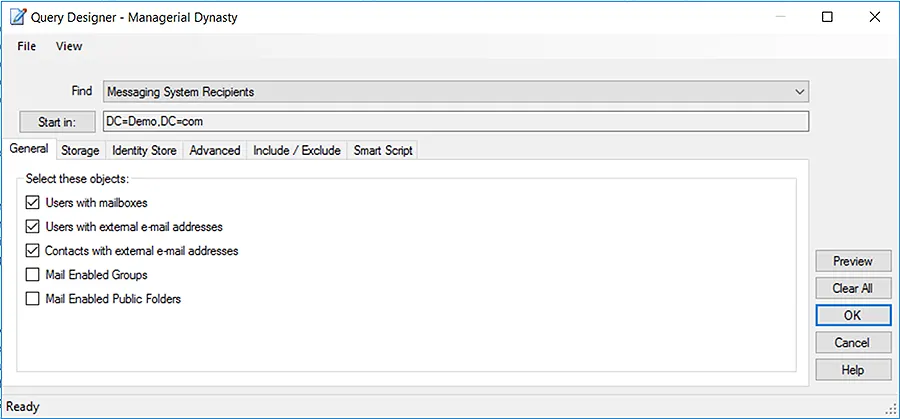
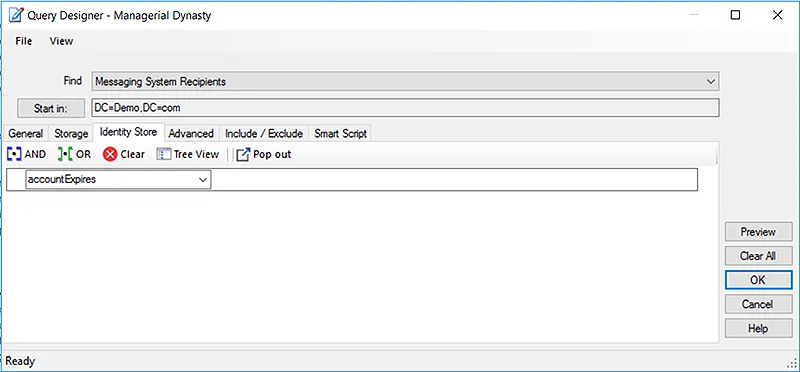
Nesting Active Directory Dynamic Groups
Every organization needs Active Directory groups based on location, department, and manager so that it can easily manage rights and permissions at various levels. By nesting Active Directory dynamic groups, you ensure that the most used and important groups in your directory are accurate and up to date with the latest information and permissions.
Let’s consider the following scenario to understand why nesting dynamic groups is a good idea for ensuring accurate and up-to-date information:
- A multinational organization is operating in three different countries: USA, UK, and Canada.
- It has three core departments in all three countries: Marketing, Sales, and Finance.
- Each department has a different manager.
- The organization wants distinct groups for each country.
- Users of every country should have different levels of access and permissions.
Based on this situation, the organization can do the following:
- Create different groups for its users in USA, UK, and Canada.
- Once the groups are created and their memberships are established, the organization can then create groups department-wise and nest them in their respective country groups.
- After nesting the department groups in the country groups, the organization can create groups with direct reports of managers and nest them in the department groups.
This way, the organization will be able to maintain distinct groups for every country and manage the rights and access to resources separately for every department. The following screenshots show how Dynasties are displayed in GroupID as well as ADUC:
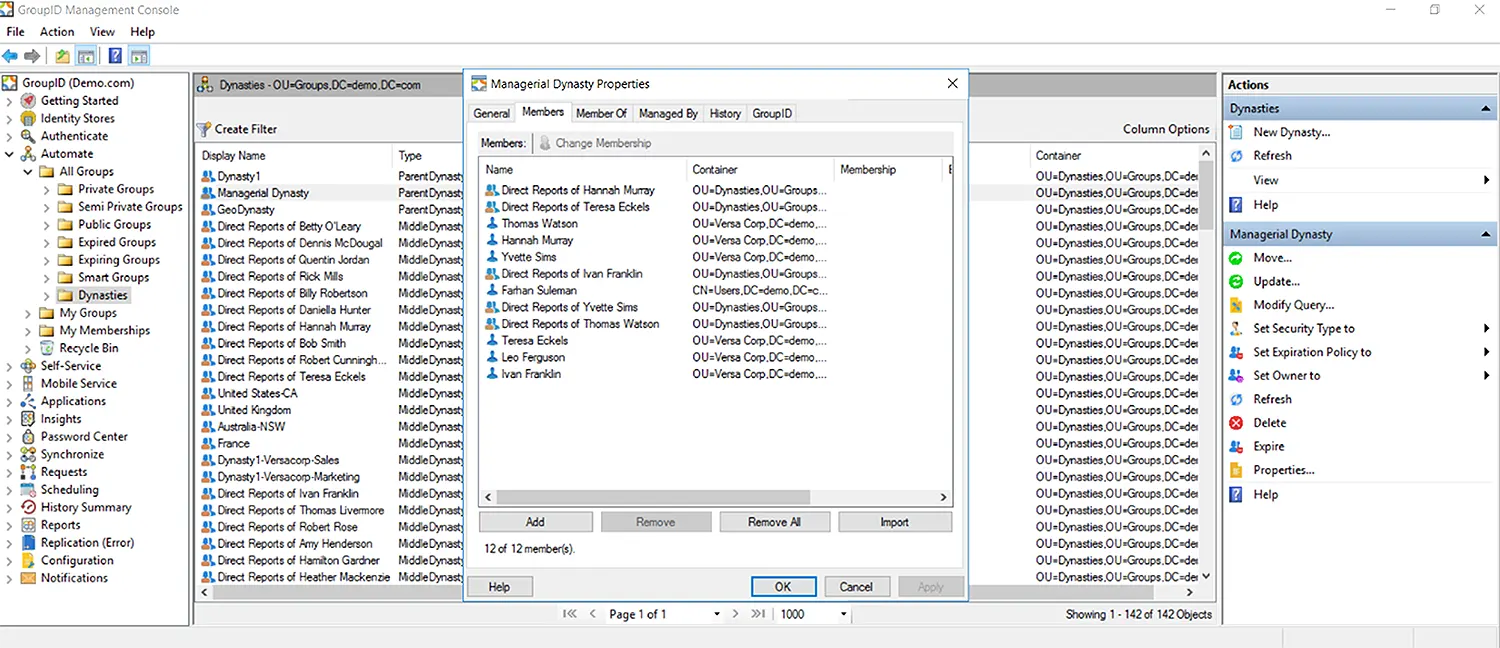
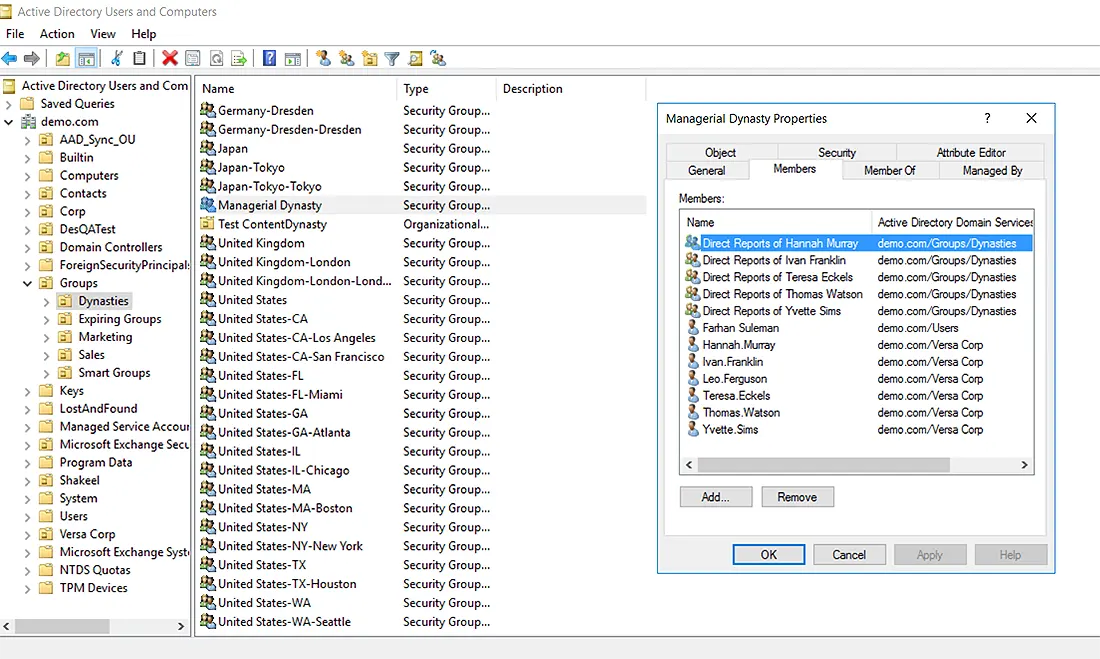
Conclusion
When managing Active Directory nested groups becomes too much of a burden to bear, it is time for a change. Get started with GroupID today and see how much more you could be doing with your Active Directory groups while improving productivity.
Jonathan Blackwell
View ProfileSince 2012, Jonathan Blackwell, an engineer and innovator, has provided engineering leadership that has put GroupID at the forefront of group and user management for Active Directory and Azure AD environments. His experience in development, marketing, and sales allows Jonathan to fully understand the Identity market and how buyers think.